SD-WAN
MEF New Standards for SD-WAN Services; SASE Work Program; Dec 2022 UPDATE!
The Metro Ethernet Forum (MEF) [1.] has published new SD-WAN standards that add critical enhancements, including new service capabilities for underlay connectivity, important application performance metrics, and security zones for service providers deploying SD-WAN managed services.
Note 1. The MEF is an industry forum empowering enterprises to transform digitally with standard services and APIs for network, cloud, and technology providers. While initially focused on Carrier Ethernet, the MEF scope has broadened to encompass overlay services like SD-WAN. The ITU-T does not have an active SD-WAN standardization program so the industry must look to the MEF for service definitions and standards for that subject.
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………
The new MEF standards include:
- MEF 70.1 updates MEF 70, the industry’s first global SD-WAN standard, to include new service attributes for underlay connectivity services, new measurable performance metrics that provide visibility into an application’s performance within the provider network and across multiple service providers, and the infrastructure to support application-based security defined in MEF 88 (see below).
- MEF 88, MEF’s first security standard, enhances an SD-WAN service to add security functions. These include defining threats, malware protections, security policy terminology and attributes, and describing what actions a policy should take in response to certain threats.
- MEF 95 provides a unified policy framework for MEF’s SD-WAN (MEF 70.1), Network Slicing (MEF 84), and SASE (MEF W117) and Zero Trust (MEF W118) standards coming in 2022.
“We’re seeing a healthy uptick in SD-WAN deployments driven by work from anywhere, as more users are connecting to the cloud and cloud-based applications. We estimate the global SD-WAN service market will grow from $2.85B in 2020 to $14.5B in 2025 (CAGR of 38%),” said Roopa Honnachari, vice president of research & global program leader – network & edge services, Frost & Sullivan.
“MEF’s work in standardizing and certifying SD-WAN managed services is helping to drive that adoption, and we believe certified services and professionals will continue to play an important role in moving the market forward.”
“MEF develops standards and certifications to provide clarity and assurance and remove complexity for SD-WAN managed services.
The new standards define the service behavior and associated policy language needed to deliver high-performance, secure SD-WAN managed services,” said Pascal Menezes, CTO, MEF.
Source: MEF
……………………………………………………………………………………..
“These standards, and the forthcoming SASE and Zero Trust standards, benefit both customers and providers—customers know what to expect when purchasing SD-WAN managed services from a provider, and providers have the tools needed to deliver secure SD-WAN services that drive customer satisfaction,” Pascal added.
Both service providers and vendors can attain certification for MEF’s SD-WAN standards in the MEF 3.0 SD-WAN certification program which validates compliance with MEF standards for delivering managed SD-WAN services and the underlying technology. The objective is to eliminate market confusion, and enable faster SD-WAN market adoption.
In 2022, secure SD-WAN requirements will be added to the MEF 3.0 certification program. Currently, 17 companies have achieved MEF 3.0 SD-WAN certification. In addition, the MEF-SDCP Professional Certification training and certification provides an opportunity for the engineers, architects, product managers, and others deploying SD-WAN solutions to demonstrate their expertise in MEF 3.0 service standards.
- Worldwide, there are over 700 MEF-SDCP professionals employed by more than 120 companies.
- Over 60 service providers have either the Carrier Ethernet or SD-WAN certification within the MEF 3.0 framework, and a handful have both.
- AT&T, Verizon, Comcast Business and Windstream are among the service providers with MEF 3.0 SD-WAN Certification. Those companies also rank within the top five of Vertical Systems Group’s 2020 US Carrier Managed SD-WAN Leaderboard.
MEF SASE Work:
MEF will also be releasing SASE (MEF W117) and Zero Trust (MEF W118) standards in 2022. MEF started developing its secure access service edge (SASE) framework last fall to clarify the service attributes and definitions for SASE.
The SD WAN market has already become bogged down by different SASE definitions, which has led to confusion among enterprise customers and frustration for service providers.
MEF defines SASE as a “service connecting users (machine or human) with their applications in the cloud while providing connectivity performance and security assurance determined by policies set by the Subscriber.” The networking and security functions within a SASE service include routing, VPN, path selection, traffic shaping, firewall, threat prevention and more.
Yet finding one vendor that meets all those requirements, and delivers a SASE service that is simple to deploy, is proving challenging for service providers that want to provide SASE as a managed service to enterprise customers.
“The ideal is one vendor, right? That’s the ideal, we all agree with it. But at least for enterprise customers, we’d haven’t found a single vendor solution that meets their needs yet from a SASE perspective,” said Verizon’s Vincent Lee.
MEF Media Contact: Melissa Power [email protected]
……………………………………………………………………………………………………………………………………………………………………………………………………
References:
MEF Introduces New Standards for High-Performance, Secure SD-WAN Services
https://www.mef.net/service-standards/overlay-services/sase/
……………………………………………………………………………………………………………………………………………………………………………….
December 2022 UPDATE:
MEF SD-WAN and SASE Standards:
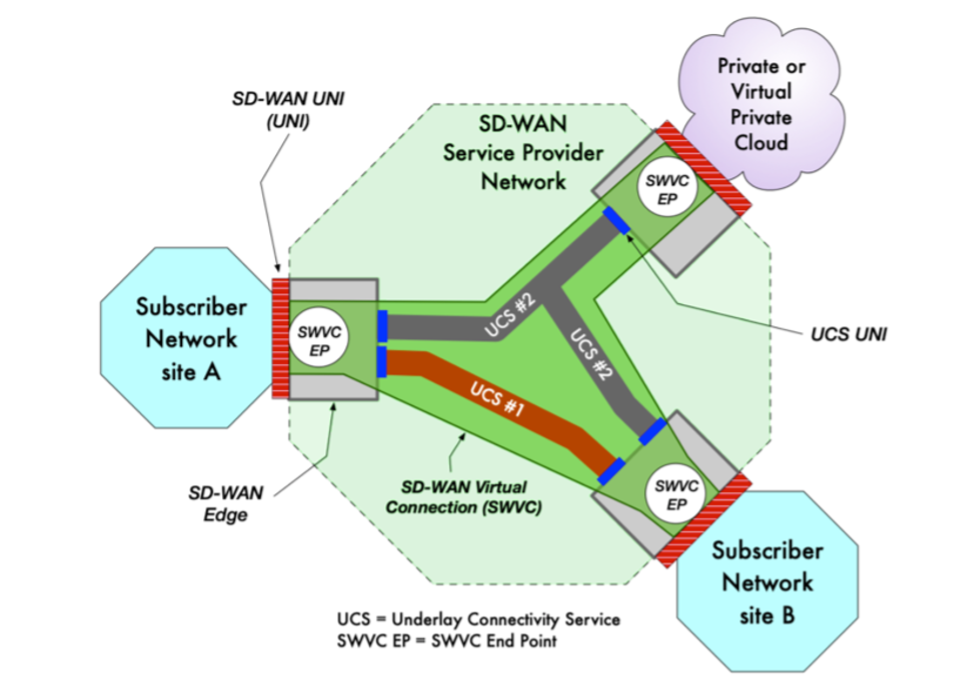
In August 2019, the MEF published the industry’s first global standard defining an SD-WAN service and its service attributes. SD-WAN Service Attributes and Services (MEF 70). The MEF SD-WAN standard describes requirements for an application-aware, over-the-top WAN connectivity service that uses policies to determine how application flows are directed over multiple underlay networks irrespective of the underlay technologies or service providers who deliver them. However, it does not address interoperability because it does not specify either a UNI or NNI protocol stack.
MEF 70 defines:
- Service attributes that describe the externally visible behavior of an SD-WAN service as experienced by the subscriber.
- Rules associated with how traffic is handled.
- Key technical concepts and definitions like an SD-WAN UNI, the SD-WAN Edge, SD-WAN Tunnel Virtual Connections, SD-WAN Virtual Connection End Points, and Underlay Connectivity Services.
SD-WAN standardization offers numerous benefits that will help accelerate SD-WAN market growth while improving overall customer experience with hybrid networking solutions. Key benefits include:
- Enabling a wide range of ecosystem stakeholders to use the same terminology when buying, selling, assessing, deploying, and delivering SD-WAN services.
- Making it easier to interface policy with intelligent underlay connectivity services to provide a better end-to-end application experience with guaranteed service resiliency.
- Facilitating inclusion of SD-WAN services in standardized LSO architectures, thereby advancing efforts to orchestrate MEF 3.0 SD-WAN services across automated networks.
- Paving the way for creation and implementation of certified MEF 3.0 SD-WAN services, which will give users confidence that a service meets a fundamental set of requirements.
In December 2022, MEF published two Secure Access Service Edge (SASE) standards defining 1.] SASE service attributes, common definitions & a framework and 2.] a Zero Trust framework that together allow organizations to implement dynamic policy-based actions to secure network resources for faster decision making and implementation for enterprises. MEF’s SASE standard defines common terminology and service attributes which is critically important when buying, selling, and delivering SASE services. It also makes it easier to interface policy with security functions for cloud-based cybersecurity from anywhere. MEF’s Zero Trust framework defines service attributes to enable service providers to implement and deliver a broad range of services that comply with Zero Trust principles.
- SASE Service Attributes and Service Framework Standard: specifies service attributes to be agreed upon between a service provider and a subscriber for SASE services, including security functions, policies, and connectivity services. The standard defines the behaviors of the SASE service that are externally visible to the subscriber irrespective of the implementation of the service. A SASE service based upon the framework defined in the standard enables secure access and secure connectivity of users, devices, or applications to resources for the subscriber. MEF’s SASE standard (MEF 117) includes SASE service attributes and a SASE service framework.
- Zero Trust Framework for MEF Services: The new Zero Trust Framework for MEF Services (MEF 118) defines a framework and requirements of identity, authentication, policy management, and access control processes that are continuously and properly constituted, protected, and free from vulnerabilities when implemented and deployed. This framework also defines service attributes, which are agreed between a subscriber and service provider, to enable service providers to implement and deliver a broad range of services that comply with Zero Trust principles.
Dell’Oro: SD-WAN market grew 45% YoY; Frost & Sullivan: Fortinet wins SD-WAN leadership award
According to a recently published report by Dell’Oro Group, the worldwide SD-WAN market grew 45% in the third quarter of 2021 compared to the prior year. Cisco maintained the top position for the revenue share for the quarter and was followed by Fortinet and VMware in the second and third spots.
“Enterprises are upgrading network infrastructures at accelerated rates compared to pre-pandemic times, and our research finds that the SD-WAN market is growing at strong double-digit rates in all regions of the world,” said Shin Umeda, Vice President at Dell’Oro Group. “Because SD-WAN is software-based technology, the global supply chain disruptions have had less of an effect compared to hardware-based networking products,” added Umeda.
Additional highlights from the 3Q 2021 SD-WAN Report:
- The SD-WAN market continues to consolidate around a small number of vendors with the top six vendors accounting for 69 percent market share in 3Q 2021.
- Cisco’s quarterly SD-WAN revenue nearly doubled in 3Q 2021 with especially strong growth in the North America region.
- The market for hardware-based Access Routers grew quarterly revenues for the first time in almost two years.
The Dell’Oro Group SD-WAN & Enterprise Router Quarterly Report offers complete, in-depth coverage of the SD-WAN and Enterprise Router markets for future current and historical periods. The report includes qualitative analysis and detailed statistics for manufacture revenue by regions, customer types, and use cases, average selling prices, and unit and port shipments. To purchase these reports, please contact us by email at [email protected].
Dell’Oro Group is a market research firm that specializes in strategic competitive analysis in the telecommunications, networks, and data center IT markets. Our firm provides in-depth quantitative data and qualitative analysis to facilitate critical, fact-based business decisions. For more information, contact Dell’Oro Group at +1.650.622.9400 or visit www.delloro.com.
…………………………………………………………………………………………………………………………………………………………………………………………………………………………………
Separately, Frost & Sullivan recently analyzed the global SD-WAN vendor market, and recognized Fortinet with the 2021 Global SD-WAN Vendor Product Leadership Award for transforming and securing the WAN. Fortinet’s Security-driven Networking approach to SD-WAN enables a wide range of use cases including secure and optimized connections to cloud-based applications. The company’s Secure SD-WAN solution integrates SD-WAN capabilities, advanced routing functions, next-generation firewall (NGFW), and zero trust network access (ZTNA) proxy on a single appliance or a single virtual machine (VM) to deliver secure networking capability. The solution can be deployed in a virtual or physical format on-premise or as a VM in the cloud, with a throughput of 20 Gbps, the highest available in the industry.

Fortinet’s Secure SD-WAN solution, powered by the industry’s first SOC4 SD-WAN ASIC [1.] for accelerated performance, features an unrestricted WAN bandwidth consumption model on appliances that is unique in the industry. Cloud adoption continues to grow, but enterprises have generally struggled to implement and maintain a secure, high-performing WAN that allows for efficient access to cloud-based applications across their user base. With the rise in remote working and with distributed users accessing cloud-hosted applications, the enterprise perimeter is no longer limited to users within the company site. Fortinet’s solution securely connects users to cloud-based applications delivering consistent policies off- and on-network.
Note 1. On Apr 9, 2019 John Maddison, EVP of product and solutions, Fortinet said:
“The WAN edge is now a part of digital attack surfaces, but the edge of your network must never be a bottleneck. For branch offices, the ability to provide best-of-breed WAN Edge — including SD-WAN, WAN optimization, security and orchestration — with optimal performance and security is critical to enable the digital experience. Fortinet’s SoC4 SD-WAN ASIC allows organizations to realize security-driven networking whether they have 100 or 10,000 branch offices.”
…………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
Roopa Honnachari, VP of Research, Network Services & Edge, explained that “Fortinet has been a long-time leader in the network security market, which has enabled them to deliver a solution that tightly knits advanced security features with SD-WAN. Though Fortinet is best known as a security company, they have shown their strength and innovation in networking as one of the top SD-WAN solutions on the market capable of supporting enterprise digital transformation.”
To break the perception that it is a security vendor that also does SD-WAN and to eliminate the risk of not appealing to enterprise infrastructure or network decision makers, the company has consciously focused on highlighting its routing and networking capabilities in marketing activities and proofs of concept.”
With its focus on SD-WAN with integrated advanced security and ability to deliver multiple functions in a single hardware appliance or VM, Fortinet has experienced significant growth in the last three years. The company sells 100% through channel partners, including large telcos, such as AT&T, Verizon, British Telecom, Masergy, GTT, KDDI, Orange, and Windstream, that are looking to add secure SD-WAN to their portfolios. As a result, Fortinet has nearly doubled its revenue.
Honnachari added that “Fortinet has emerged as a formidable competitor in the enterprise secure networking space. While the company has always served as a leading competitor in the network security space, the transformation to adding SD-WAN, NGFW, ZTNA access proxy, and advanced routing capabilities on a single operating system and managed by a single console is highly commendable.”

Gartner’s Magic Quadrant for WAN Edge Infrastructure
Cisco is a leader in this Magic Quadrant. It has two branded offerings: Cisco SD-WAN powered by Viptela and Cisco SD-WAN powered by Meraki. Both include hardware and software appliances, and associated orchestration and management. Cisco also provides optional additional security via the Cisco Umbrella Security Internet Gateway (SIG) platform. Cisco is based in California, U.S., and has more than 40,000 WAN edge customers. The vendor operates globally and addresses customers of all sizes, in all verticals. We expect the vendor to continue to invest in this market, particularly in the areas of improved self-healing capabilities, new consumption-based pricing models and integrated security to enable a single-vendor SASE offering.
Fortinet is a leader in this Magic Quadrant. Its offering is the FortiGate Secure SD-WAN product, which includes physical, virtual appliances and cloud-based services managed with FortiManager orchestrator. Fortinet is based in Sunnyvale, California, U.S., and Gartner estimates that it has more than 34,000 WAN edge customers with more than 10,000 SD-WAN customers. FortiOS v.7.0 combines ZTNA to its broad WAN and network security functionalities to deliver a capable SASE offering. It has a wide global presence, addressing customers across multiple verticals and sizes. We expect the vendor to continue investing in SASE, artificial intelligence for IT operations (AIOps) and 5G functionality.
VMware is a leader in this Magic Quadrant. Its offering is branded as VMware SD-WAN, and is part of VMware SASE. The offering includes edge appliances (hardware and software), gateways — VMware points of presence (POPs) offering various services — and an orchestrator and its Edge Network Intelligence. VMware provides additional optional security via VMware Cloud Web Security and VMware Secure Access. Based in California, U.S., it has more than 14,000 SD-WAN customers. The vendor operates globally and addresses customers of all sizes, and in all verticals. Gartner expects the vendor to continue investments in this market, including enhancing options for remote workers and building out its SASE offering.
………………………………………………………………………………………………………………………
Each year, Frost & Sullivan presents this award to the company that has developed a product with innovative features and functionality that is gaining rapid market acceptance. The award recognizes the quality of the solution and the customer value enhancements it enables.
About Frost & Sullivan:
For six decades, Frost & Sullivan has been world-renowned for its role in helping investors, corporate leaders, and governments navigate economic changes and identify disruptive technologies, Mega Trends, new business models, and companies to action, resulting in a continuous flow of growth opportunities to drive future success. Contact us: Start the discussion. Contact us: Start the discussion.
Contact: Bianca Torres
P: 1.210.477.8418
E: [email protected]
References:
https://www.gartner.com/doc/reprints?id=1-27EGPR7B&ct=210909&st=sb
ONF and Deutsche Telekom Demonstrate Fully Disaggregated Open RAN and SD-WAN
Deutsche Telekom is working with the Open Networking Foundation (ONF) and eight vendors to test software-defined radio access networks (SD-RAN) and Open RAN in what it calls a fully disaggregated system. This is the first field trial implementing fully disaggregated open RAN solutions using ONF’s RAN Intelligent Controller (RIC) software platform as defined by the O-RAN architecture. This 4G and 5G Standalone (SA) outdoor trial is live at Deutsche Telekom in Berlin, Germany.
In addition, the Facebook-backed Telecom Infra Project (TIP) is taking part by providing hardware and facilities out of the TIP Community Lab in Berlin hosted by Deutsche Telekom.
Carriers are investing in open RAN to enable a new breed of modular and customizable 5G solutions to accelerate innovation and enable the mix-and-match of best-of-breed components from multiple vendors. Open RAN gives operators choice and flexibility to customize and optimize their networks. This SD-RAN trial hosted by DT highlights the promise and flexibility of open RAN by integrating components from eight companies: AirHop, Edgecore, Facebook, Foxconn, Intel, Radisys, Supermicro and Wiwynn. Additionally, the Telecom Infra Project (TIP) is participating by providing hardware and facilities out of the TIP Community Lab in Berlin hosted by DT. The on-site field trial integration and testing is being coordinated and supported by Highstreet Technologies.
The live trial features horizontally disaggregated hardware (separate RU, DU, and CU units), as well as vertically disaggregated software components including an open source near real-time RIC (nRT-RIC) and xApps coming from the ONF’s SD-RAN project. By integrating proprietary and open source components, including a near real-time RIC and xApps, this ground-breaking trial exemplifies a model for how future open RAN deployments are envisioned to take shape.
The entirety of the trial is operationalized leveraging ONF’s Aether platform, a centrally-managed, multi-cloud, cloud-native platform providing Connectivity-as-a-Service, and highlights network slicing with multiple UPFs running at the edge. The SD-Core component of Aether provides 5G connectivity and the control plane running from the public cloud while SD-Fabric is a fully programmable network fabric optimized for the edge cloud used to instantiate a P4-based 4G/5G UPF in hardware.
Aether hosts the Radisys containerized CU while the Intel® Smart Edge Open (formerly known as OpenNESS) software toolkit hosts the Radisys DU to enable cloud-native deployment of the RAN workload with optimization on the 3rd Gen Intel® Xeon® Scalable processor and Intel® vRAN Dedicated Accelerator ACC100. The CU and DU are integrated with ONF’s nRT-RIC, xApps, SD-Core 5G core and Foxconn O-RU.
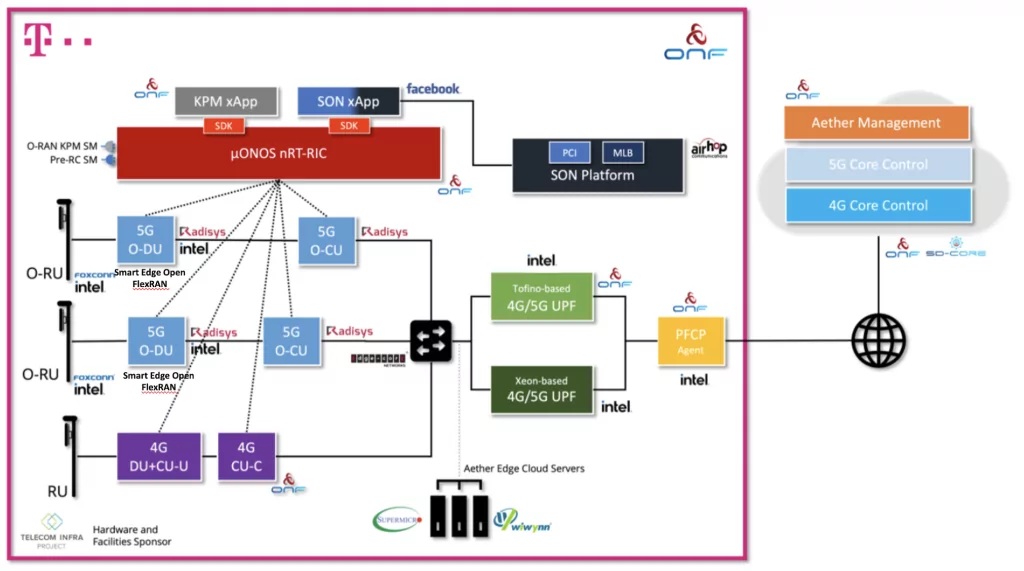
“The Berlin SD-RAN Open RAN Trial, is a momentous step towards realizing the vision of fully disaggregated and intelligent RAN, leveraging ONF’s leading open source RAN Intelligent Controller software platform. In addition to open fronthaul, this trial includes disaggregated RU/DU/CU units, and also vertically disaggregates the RIC and xApps according to SDN principles. Together, we are demonstrating the power of truly open RAN and ecosystem collaboration to accelerate innovation.”
– Alex Choi, Senior Vice President Strategy & Technology Innovation, Deutsche Telekom and Founding Board Member, O-RAN Alliance
“The SD-RAN Berlin Trial with DT is a significant industry milestone for open RAN. At ONF we are seeing tremendous interest from the mobile community for our open source implementation of the O-RAN architecture, and this trial demonstrates the maturity of the SD-RAN open source RIC and xApp development platform.”
– Guru Parulkar, Executive Director, ONF
“AirHop is thrilled to be participating in this DT SD-RAN trial. We are contributing commercially hardened 5G xApps that work with the complete Open RAN end-to-end solution. The trial demonstrates that commercial xApps can be quickly integrated and deployed using O-RAN defined standard interfaces to deliver automated performance optimization.”
– Yan Hui, CEO, AirHop
“Open systems are the future, and Edgecore is pleased to be leading the charge and to be providing open network hardware that is running software from ONF as part of this DT SD-RAN trial. It has been amazing working with this dynamic community, and a real pleasure to be collaborating with DT on this effort.”
– Jeff Catlin, VP of Technology, Edgecore Networks
“We are excited to see multiple ecosystem partners collaborating to test and trial this disaggregated Open RAN solution. We have made great progress with the RIC-xApp portability paradigm and we look forward to continuing to make contributions to the SD-RAN project.”
– Manish Singh, Head of Wireless Ecosystem Programs, Facebook
“Foxconn has contributed the Radio Units (RUs) that are deployed in the SD-RAN trial. Given that this represents the first deployment of a truly disaggregated RAN solution, we’ve been very pleased with the collaboration and commitment shown by the whole SD-RAN community.”
– Dr. Benjamin Wang, Sr. 5G RD Director, Infrastructure Product Division, Foxconn
“Our long-standing collaboration with ONF and its partners reflects our priority to collaborate with the Open Source community and aligns very well to initiatives such as Intel Smart Edge Open® targeted for open innovation and developer acceleration. It is great to see an entire portfolio of Intel technologies enabling ONF SD-RAN and SD-Core ranging from Intel® Xeon® Scalable processors, vRAN accelerators to software offerings such as Intel® FlexRAN and Smart Edge Open® get featured in this trial, paving the way to the next wave of disaggregated and intelligent networks.”
– Renu Navale, VP & GM in the Network Platforms Group, Intel
“The OCP and ONF have a synergistic relationship, with OCP focused on open hardware and ONF focused on open software that can run on OCP hardware. The SD-RAN trial with DT exemplifies this relationship, demonstrating OCP Inspired™ openEdge servers from Wiwynn, an OCP Certified Solution Provider, running critical components of the SD-RAN solution.”
– Steve Helvie, VP of Channel, Open Compute Project (OCP)
“As a founding member of the SD-RAN initiative with ONF, Radisys is excited to participate in this important SD-RAN trial at DT, demonstrating use cases of RAN optimization and multi-vendor interoperability. We worked closely with the ONF community to develop service models, use cases and in the end-to-end integration of this field trial. This is a significant step towards commercial adoption of O-RAN based solutions by operators.”
– Arun Bhikshesvaran, CEO, Radisys
“Supermicro is excited to have our servers included in the SD-RAN Berlin trial. This trial is a significant step in realizing the potential of open RAN, and it has provided a great opportunity for multi-vendor collaboration and learning. We are a strong supporter of open source and disaggregation, and believe that it is essential for enabling 5G edge, core and cloud networks.”
– Jeff Sharpe, Director, 5G / IoT Edge Solutions, Supermicro
“TIP is pleased to be collaborating to support the SD-RAN Berlin Trial. The RIA sub-group of the TIP OpenRAN project is prioritizing use cases for open RAN that are being highlighted by this effort, so we see terrific synergies working with ONF and the broader SD-RAN community to support this first-of- its-kind trial featuring a multi-vendor mix of RU/DU/CU controlled by an open RIC and xApps.”
– Attilio Zani, Executive Director, Telecom Infra Project
“Wiwynn is pleased to be providing our edge cloud optimized servers as part of the DT SD-RAN trial. These systems are designed for edge and telco applications, and are certified by ONF for the Aether platform used for this DT trial. We are committed to building solutions optimized for open RAN deployments, and we’re very excited to see this DT trial advancing the state-of-the-art for open RAN.”
-Steven Lu, Senior Vice President, Wiwynn
DEUTSCHE TELEKOM SD-RAN TRIAL EVENT:
ONF and DT will be co-hosting a virtual event October 19th offering an in-depth view into the trial and key learnings from the community. Featuring live keynotes and on-demand talks from operator and vendor leaders from across the open RAN movement. Register to hear about lessons learned directly from the experts who have deployed the first trial of its kind! The event is open to anyone.:
Deutsche Telekom SD-RAN Trial – Webinar
October 19th, 2021
5pm CEST, 11am EDT, 8am PDT
REGISTER HERE
References:
ONF and Deutsche Telekom Demonstrate Fully Disaggregated Open RAN with Open RIC Platform
VSG Global SD-WAN Leaderboard Rankings and Results
Orange Business Services (France), AT&T (U.S.), and Verizon (U.S.) topped Vertical Systems Group’s (VSG) latest leaderboard for global carrier-managed SD-WAN. They were followed in the rankings by NTT (Japan), BT (UK), Telefonica Global Solutions (Spain), and Vodafone (UK). [The rank order is based on site share outside of the provider’s home country, as of June 30, 2021.]
Rosemary Cochran, principal analyst and co-founder of Vertical Systems Group said that global networks are far more complex to manage and administer compared to domestic SD-WAN offerings. They often require service providers to negotiate contracts with multiple countries, meet diverse regulatory requirements, and support numerous network technologies.
This industry benchmark for multinational SD-WAN market presence ranks companies that hold a 5% or higher share of billable retail sites outside of their respective home countries.

Twelve companies qualify for the Mid-2021 Global Provider Managed SD-WAN Challenge Tier (in alphabetical order):
Aryaka (U.S.), Colt (U.K.), Deutsche Telekom (Germany), Global Cloud Xchange (India), GTT (U.S.), Hughes (U.S.), Lumen (U.S.), PCCW Global (Hong Kong), Singtel (Singapore), Tata (India), Telia (Sweden) and Telstra (Australia).
The Challenge Tier includes companies with site share between 1% and 5% of this defined SD-WAN segment.
“We’re pleased to release the first benchmark that measures Global Provider market presence based on multinational managed SD-WAN customer sites,” said Rick Malone, principal of Vertical Systems Group. “Enterprises with business-essential applications that span multiple regions of the world are choosing SD-WAN solutions from network operators with the global infrastructures, experience, partnerships and technical expertise necessary to deliver world-class services.”
Research Highlights for Global Provider SD-WAN Services:
- Orange Business Services gained the top share rank on the Mid-2021 Global Provider Managed SD-WAN LEADERBOARD with the largest number of customer sites installed.
- Vertical’s SD-WAN Coverage Analysis for five regional markets – North America, Latin America, Europe, Africa/Middle East, Asia/Pacific – shows that all seven companies ranked on the Mid-2021 Global Provider SD-WAN LEADERBOARD have good to strong coverage in at least three of these regions.
- COVID-19 continues to appreciably impact every region of the world. Just being able to get the SD-WAN equipment and support the services has been a disruptive experience for service providers and their customers.
- Challenges cited by Global SD-WAN operators include: workforce health protection, tracking the shift back from remote to office environments, service disconnects due to business closures, and supply chain disruptions.
- Most multinational Managed SD-WAN customer implementations are hybrid network configurations that incorporate MPLS, IP VPN, Cloud connectivity or other services, plus multiple security capabilities that are integral or supplied by technology partners.
- SD-WAN customers with MPLS connections are migrating to more cloud-suitable broadband services that provide bandwidth flexibility and lower pricing.
- Ethernet DIA (Dedicated Internet Access) is the preferred choice for SD-WAN customers that require dedicated, symmetrical connectivity.

Fictitious image of a global mesh connected SD-WAN
…………………………………………………………………………………………..
Five of the seven companies on the Mid-2021 Global Provider SD-WAN LEADERBOARD are ranked on the 2020 Global Provider Ethernet LEADERBOARD (in rank order): AT&T, Orange Business Services, Verizon, BT Global Services and NTT.
- Two companies ranked on the Mid-2021 Global Provider SD-WAN LEADERBOARD – AT&T and Verizon – have attained MEF 3.0 SD-WAN Services Certification to date. Additionally, three companies cited in the Challenge Tier – Colt, PCCW Global and Telia – have MEF 3.0 SD-WAN Services certification.
- The primary technology suppliers to the nineteen Mid-2021 Carrier Managed SD-WAN LEADERBOARD and Challenge Tier companies are as follows (in alphabetical order): Cisco, Fortinet, HPE Aruba, Nuage Networks (Nokia), Versa and VMware.
The Market Player tier includes providers with site share below 1%. Companies in the Mid-2021 Market Player tier are as follows (in alphabetical order):
Batelco (Bahrain), China Telecom (China), Claro Enterprise Solutions (Mexico), CMC Networks (South Africa), Cogent (U.S.), Epsilon (Singapore), Etisalat (Abu Dhabi), Expereo (Netherlands), HGC Global (Hong Kong), Intelsat (U.S.), KDDI (Japan), Masergy (U.S.), Meriplex (U.S.), PLDT Enterprise (Philippines), SES (Luxembourg), Sparkle (Italy), StarHub (Singapore), Syringa Networks (U.S.), T-Mobile (U.S.), Telenor (Norway), Telin(Singapore), Transtelco (U.S.), Virgin Media (U.K.), Zayo (U.S.) as well as other providers (unnamed) selling SD-WAN services outside their home country.
Closing Comment:
This VSG report highlights the disparate implementations of global SD-WANs. “…implementations are hybrid network configurations that incorporate MPLS, IP VPN, Cloud connectivity or other services, plus multiple security capabilities that are integral or supplied by technology partners.”
That is because there is no clear definition of functionality (yeah we know about MEF’s definition) and no specification of any exposed interfaces, e.g. UNI, network node to network node, or NNI between two SD-WAN networks.
As such, global SD-WANs are really a concept, not a set of required networking technologies with defined reference points and standardized interfaces/APIs. As a result, it’s a serious challenge for the global SD-WAN operator to ensure interoperability between each of the different subnetwork interfaces so that end to end connectivity is achieved.
…………………………………………………………………………………………….
References:
Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role
Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role
Disclaimer:
The IEEE Techblog has not covered this topic for a very long time, because there are no standards or accepted specifications for any type of SD-WAN or SASE interoperability. Those networks are all supplied by a single vendor, but that hasn’t stopped them from gaining market share, especially from legacy IP-MPLS VPNs. That’s even though functionality differs for each vendor’s SD-WAN or SASE offering and there is no interoperability, especially from one provider’s SD-WAN to another’s.
Explanations:
SD-WANs use Application-aware routing across the WAN, whereas classical SDN used a centralized controller to compute routes at the Network layer for the Control plane with “L2/L3 packet forwarding engines” in the Data Plane. The SDN Control and Data planes are separated with the “OpenFlow” API used to communicate between them.
NFV is not about routing but virtualizing network functions (“virtual appliances”) that would otherwise be implemented in hardware-firmware boxes.
Network virtualization (defined below) has played a key role in the popularity of SD-WAN and SASE, even though that network paradigm was not included in the original definition of SDN in which no overlay networks were permitted. (That was referred to as “SDN Washing” from 2011-2014, by SDN strongman Guru Parulker, now Executive Director of the Open Network Foundation.)
………………………………………………………………………………………….
Discussion:
At many data networking industry conferences and events from 2011 to 2014, participants claimed that Software Defined Networks (SDNs) would usher in a whole new era for networking. One colleague of mine said it would be “a new epoch for networking.” Instead, there were various versions of SDNs, used primarily by hyper-scale cloud service providers (most notably Google and Microsoft) and a few large telcos (e.g. NTT, AT&T). But SDN never spread to enterprise or campus networks.
When SDN fizzled out, the industry’s focus shifted to Software Defined WANs (SD-WANs), which provides user control of a virtual network overlay via the Application layer. There are three components to a SD-WAN:
- SD-WAN edge is where the network endpoints reside. This can be a branch office, a remote data center, or cloud platform.
- SD-WAN Orchestrator is the virtualized manager for network, overseeing traffic and applying policy and protocol set by operators.
- SD-WAN Controller centralizes management, and enables operators to see the network through a single software interface, and set policy for the orchestrator to execute.
In addition, there are three main types of SD-WAN architecture: on-premises, cloud-enabled, and cloud-enabled with a backbone.
SD-WANs continue to roll out in many different shapes, forms and flavors, without any standards for any type of interoperability (e.g no UNI, NNI, Interface to legacy IP-MPLS VPNs, etc). Even the definition and certification by the MEF (Metro Ethernet Forum) has failed to catch on so there is no uniform functionality between one SD-WAN and another.
Because of its virtualized network architecture [1.], SD-WANs don’t require specific hardware for specialized network functions. Instead, the infrastructure is made of commercial off-the-shelf (COTS) equipment, also known as white-boxes. Therefore, all SD-WAN products are 100% software based.
Note 1. Network virtualization is the process of transforming network functions into software and disconnecting them from the hardware they traditionally run on. The software still consumes the hardware’s resources, but is a separate entity that can be changed, moved, and segmented while the hardware remains the same.
The virtualized and software-based version of the network is an overlay on top of the physical network infrastructure. The physical network’s devices like switches and routers still perform tasks like packet forwarding, while how to forward those packets is handled by the software running on the switches and routers.
………………………………………………………………………………………….
Meanwhile a newer entry known as Secure Access Service Edge (SASE) has garnered a lot of media attention. This Gartner-coined product category, which combines elements of SD-WAN, cloud-based security, and edge computing, has gained significant traction in the two years since its inception.
SASE’s remote access functionality and low barrier to entry made it an attractive option for enterprises trying to cope with the rapid shift to remote work due to the pandemic. Within months of the first lockdown orders going into effect, nearly every SD-WAN and security vendor had announced a SASE security architecture, either through internal development, partnerships, or acquisitions.
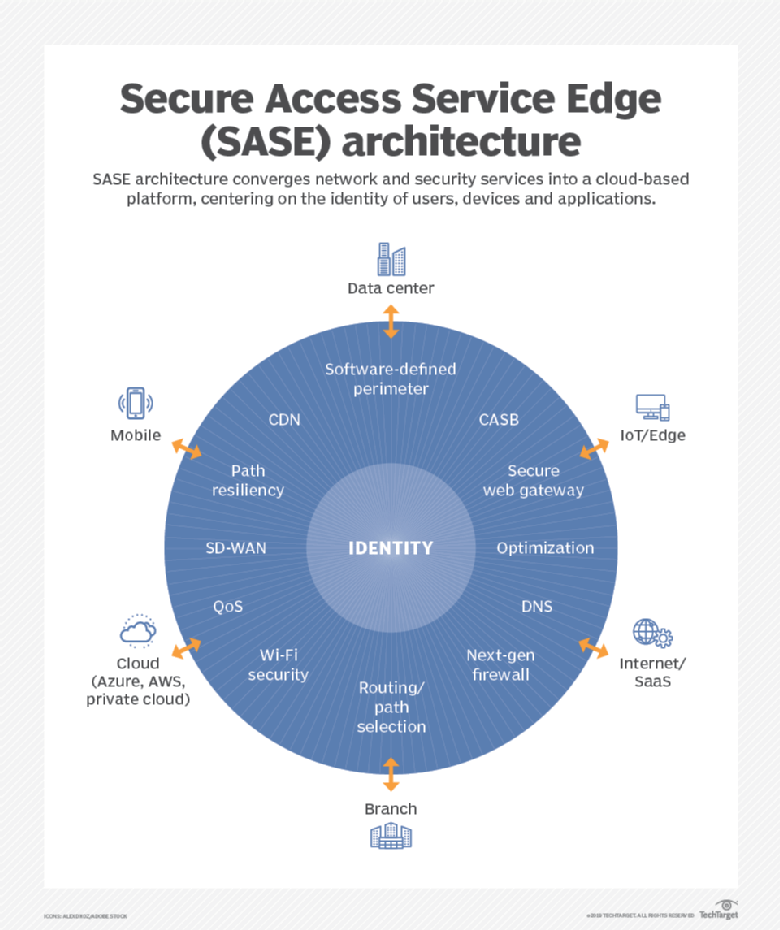
SASE is the convergence of wide area networking, or WAN, and network security services like CASB (Cloud Assisted Security Broker), FWaaS (Firewall as a Service) and Zero Trust, into a single, cloud-delivered service model.
According to Gartner, “SASE capabilities are delivered as a service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations.”
Gartner forecasts that, “by 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018.”
A SASE architecture identifies users and devices, applies policy-based security, and delivers secure access to the appropriate application or data. This approach allows organizations to apply secure access no matter where their users, applications or devices are located.
According to Cisco’s latest CISO Survival Guide, almost all (98%) CISOs plan to spend money on secure access service edge (SASE), and 55% of them intend to prioritize 25% to 75% of future IT security budgets on it, according to
Cisco surveyed more than 100 CISOs and security leaders for this report. The biggest shift for CISOs this year is toward SASE, following the pandemic and related trend of working from anywhere in the world, said Dug Song, chief strategy officer at Cisco Secure.
“I think hybrid work is here to stay,” Song told SDxCentral in an interview. Most organizations have decided to maintain flexible work for employees even post-pandemic, which requires changes to their IT security programs.
………………………………………………………………………………………….
Many industry experts say SASE services must be built on a cloud-native architecture (like 5G SA core network) and distributed across multiple edge locations.
While several vendors including Cisco and Fortinet have rejected the cloud native approach, arguing that networking and security appliances still have a role to play both at the branch and the edge, it’s a principle that’s reflected in Gartner’s own literature and wholeheartedly embraced by VMware, CATO and other SASE vendors.
Specifically, VMware offers a cloud-native SASE architecture that has combined multiple solutions in it such as SD-WAN Gateways, VMware Secure Access, ZTNA solution, SWG, CASB, AND VMware NSX Firewall. VMware delivers all these solutions through PoPs. It delivers the network and security services in an intrinsic or sequenced manner.
Cato CMO Yishay Yovel told SDxCentral, “The feeling I have is that a lot of the market is trying to talk about SASE now in a generic way, like everybody has everything, or everybody has the same capabilities, and it doesn’t matter exactly how they’re done.”
Yovel also said that just because a vendor claims to offer the full SASE software stack, doesn’t mean it’s been implemented in a way that’s scalable.
Many of the SASE functions — cloud-based firewalls in particular — are compute-intensive, they usually have to be run in cloud data centers and can’t run on the cloud provider’s more numerous content delivery network edge locations.
This dramatically limits the number of locations a SASE vendor can offer if relying on public cloud infrastructure. For example, Google Cloud claims services in 146 edge locations around the globe, but only operates 21 global data centers, which it refers to as regions.
Scalability and availability are another challenge, Yovel noted. In many cases, these virtual appliances aren’t multi-tenant and have to be assigned to a specific customer account, resulting in additional resources being required should the customer bump up against the limits of a single instance.
Yovel argues that unless a vendor’s SASE software stack is unified, customers may miss out on the ability to share context across multiple security or network functions. He explained that many functions, SD-WAN for example, are only aware of certain contexts like what application is being used, but this context could be used in conjunction with other contextual information like time, location, or identity to inform other parts of the SASE stack.
“We collect all the context elements. It doesn’t matter which part of these engines need them. Everything is built into a unified thing,” Yovel said.
The bottom line for today’s cybersecurity professionals is that both zero trust and SASE networking trends should be watched closely and integrated into forward-looking enterprise network architectural decisions.
…………………………………………………………………………………….
References:
https://www.sdxcentral.com/networking/sd-wan/definitions/software-defined-sdn-wan/
https://start.paloaltonetworks.com/gartner-report-roadmap-for-sase-convergence.html
https://www.paloaltonetworks.com/cyberpedia/what-is-sase
https://www.softwaretestinghelp.com/top-sase-vendors/
https://www.sdxcentral.com/articles/news/cato-ribs-palo-alto-networks-other-sase-imposters/2021/07/
https://www.sdxcentral.com/networking/sd-wan/
https://www.sdxcentral.com/networking/nfv/definitions/network-virtualization-and-how-it-works/
https://searchcloudsecurity.techtarget.com/tip/Why-its-SASE-and-zero-trust-not-SASE-vs-zero-trust
Masergy Performance Edge™ minimizes packet loss over public broadband connections
Masergy, a software-defined network and cloud platform company, today announced its latest patent-pending innovation which is aimed at solving a fundamental problem with broadband internet transport. Masergy Performance EdgeTM, a new SD-WAN and SASE (Secure Access Service Edge) capability, minimizes packet loss over public broadband connections, making them perform more like a private Ethernet circuit.
“Today broadband is being used ubiquitously” in home and business sites, says Ajay Pandya, director of Product Management for Masergy. “We are seeing this over the last year a lot. We used to sell 60-70% of our sites with one of the links as broadband. Now it’s in the 90’s.”
Broadband can be up to 70% cheaper than private access networks, says Pandya, but it’s still a “best effort” technology that doesn’t always provide reliable performance for applications such as voice and video conferencing.
“If I’m a contact center person or a power-user executive delivering my quarterly announcement to analysts, I don’t want the connection to be any less than excellent,” says Pandya. He also said that Masergy aims to improve the quality of last-mile connections with its Performance Edge.
“Masergy Performance EdgeTM is revolutionary because it turns the low-cost, low-performance access methodology into a high-performing service meeting the demands of today’s digital-first businesses,” said Zeus Kerravala, Founder and Principal Analyst, ZK Research. “It saves precious IT dollars and removes the productivity uncertainties of working from home all within a SASE environment.”
Most companies have become more dependent on broadband since the 2020 pandemic, but it hasn’t always served them well — particularly in cases where guaranteed performance is needed. According to an Altman Solon 2021 State of SD-WAN Study, 50% of IT leaders using only public access say their application performance is insufficient, and 48% say the cost savings don’t justify the lower quality of service. Inherently broadband is a “best effort” technology unfit for real-time data applications like voice and video conferencing. Thus, broadband often fails to deliver the performance needed, causing losses in productivity, sales, and revenue.
“Masergy is working to ensure our clients’ new need for broadband doesn’t impact their business continuity. Remote work success shouldn’t hinge on network connectivity types, and we’ve created Masergy Performance EdgeTM to make sure it doesn’t,” said Chris MacFarland, CEO, Masergy. “Masergy pioneered software-defined networking 20 years ago. We were the first to market with AIOps integrated in our SD-WAN and SASE solutions, and we’re already on the path to autonomous networking — so there’s no better company to revolutionize broadband, making it the high-performance, predictable service everyone wants it to be.
The patent-pending Performance Edge is aimed at assisting home workers, SD-WAN, SASE and MPLS customers in improving their broadband performance by reducing packet loss. The feature can be added on to Masergy’s SD-WAN and SASE services, but there is an additional cost to utilize Performance Edge. In addition, it’s currently centrally managed, so customers need to request it directly from Masergy to turn the service on.
Masergy Performance EdgeTM is available with Masergy’s Managed SD-WAN Secure and SASE offerings and uses proprietary network architecture along with industry standard and compatible routing algorithms to enable businesses of all sizes to realize increased efficiency and productivity. It provides these key benefits:
- Better Performance: Minimize packet loss over public broadband connections for more predictable application experiences
- Less Expensive: Save up to 70% compared to the cost of a private line and reduce outages with AI-powered performance visibility
- Fast to Install: Connect new sites in days versus weeks and boost existing broadband circuits for immediate results
 Image Credit: Masergy
Image Credit: Masergy
Zeus Kerravala, founder and principal analyst of ZK Research, told Light Reading that Performance Edge could be useful in delivering the “performance of private IT with broadband” for remote workers, retail and small branch locations. Kerravala says Masergy is “using a multitude of different optimization techniques to make that broadband connection work better” with tools such as WAN optimization, compression and forward-error correction.
“SD-WAN does a good job of load balancing across 2 connections, but there are a number of situations where you only have your broadband connection available … Masergy also has their MPLS backbone, so it’s the combination of two that gives you the end-to-end performance. Performance Edge optimizes the last mile, and Masergy has always been good at the middle mile,” says Kerravala.
References:
Learn more about Masergy Performance Edge
Viavi Solutions and Mavenir collaborate to validate new SD, cloud-native RAN infrastructure
VIAVI Solutions Inc today announced that Mavenir, an upstart provider of end-to-end cloud-native network software for mobile operators, is collaborating with VIAVI for lab validation of radio access solutions in the U.S. VIAVI’s lab test platform, in use by almost every base station manufacturer in the world, provides scalable test systems for validating network performance as experienced by end users, across multiple cells and different radio access technologies.
The year 2020 marked a significant inflection point for mobile networks around the globe. With 229 million subscribers as of December 2020, 5G became the fastest growing mobile technology in history. New MNOs (like Dish Network) were granted licenses to establish greenfield networks to take advantage of this demand. Meanwhile, #1 base station maker Huawei was restricted from supplying infrastructure in markets around the globe. These trends have driven an expansion of the supply chain for mobile network solutions.
VIAVI tools are able to measure the complete performance of the network over multiple interfaces including O-RAN and RF through to the packet core. Capable of emulating one to many thousands of UEs, the platforms create a sophisticated and precise test environment, including comprehensive feature interactions, simulated RF and mobility, accurate replications of real-world user behavior profiles, together with mobility across the radio access network.

“Mavenir is proud to be a leading vendor to mobile operators around the globe, offering software-defined infrastructure that can adapt to evolving requirements for both brownfield and greenfield networks, large-scale to startup networks,” said Ramnik Kamo, EVP Quality, Systems and People, Mavenir. “VIAVI has been a highly collaborative partner with our two companies’ engineering teams working together to prove a new technology against very tight customer timescales.”
“As vendors across the industry develop open, cloud-native and disaggregated architectures, testing against user expectations of service quality will be critical to accelerate adoption at scale,” said Luiz Cesar Oliveira, Vice President, Americas, VIAVI. “We are excited to help Mavenir optimize their advanced radio access solutions based on our unique experience supporting over 200 service providers and virtually every network equipment manufacturer worldwide.”
About VIAVI
VIAVI (NASDAQ: VIAV) is a global provider of network test, monitoring and assurance solutions for communications service providers, enterprises, network equipment manufacturers, government and avionics. We help these customers harness the power of instruments, automation, intelligence and virtualization to Command the network. VIAVI is also a leader in light management solutions for 3D sensing, anti-counterfeiting, consumer electronics, industrial, automotive, and defense applications. Learn more about VIAVI at www.viavisolutions.com. Follow us on VIAVI Perspectives, LinkedIn, Twitter, YouTube and Facebook.
………………………………………………………………………………………………………………………………………………………………….
References:
Barracuda CloudGen SD-WAN runs on Microsoft Azure Virtual WAN Hubs; 5G Next Target for CSPs?
In the new world of cloud service providers (CSPs) taking over every aspect of communications, Microsoft Azure will now be used as the basis of what Barracuda calls “the first SD-WAN service built natively inside Azure Virtual WAN Hubs.” Those so called “hubs” are interconnected through Microsoft’s Global Network.
The new Barracuda CloudGen SD-WAN is a SaaS deployed directly from the Azure Marketplace for as many regions as needed and administered centrally in the CloudGen WAN portal for all office locations and remote endpoints. Since the Microsoft Global Network is automatically provisioned as the backbone for anywhere, anytime application access, service providers can create a pragmatic SASE platform in the public cloud tailored to their specific needs.
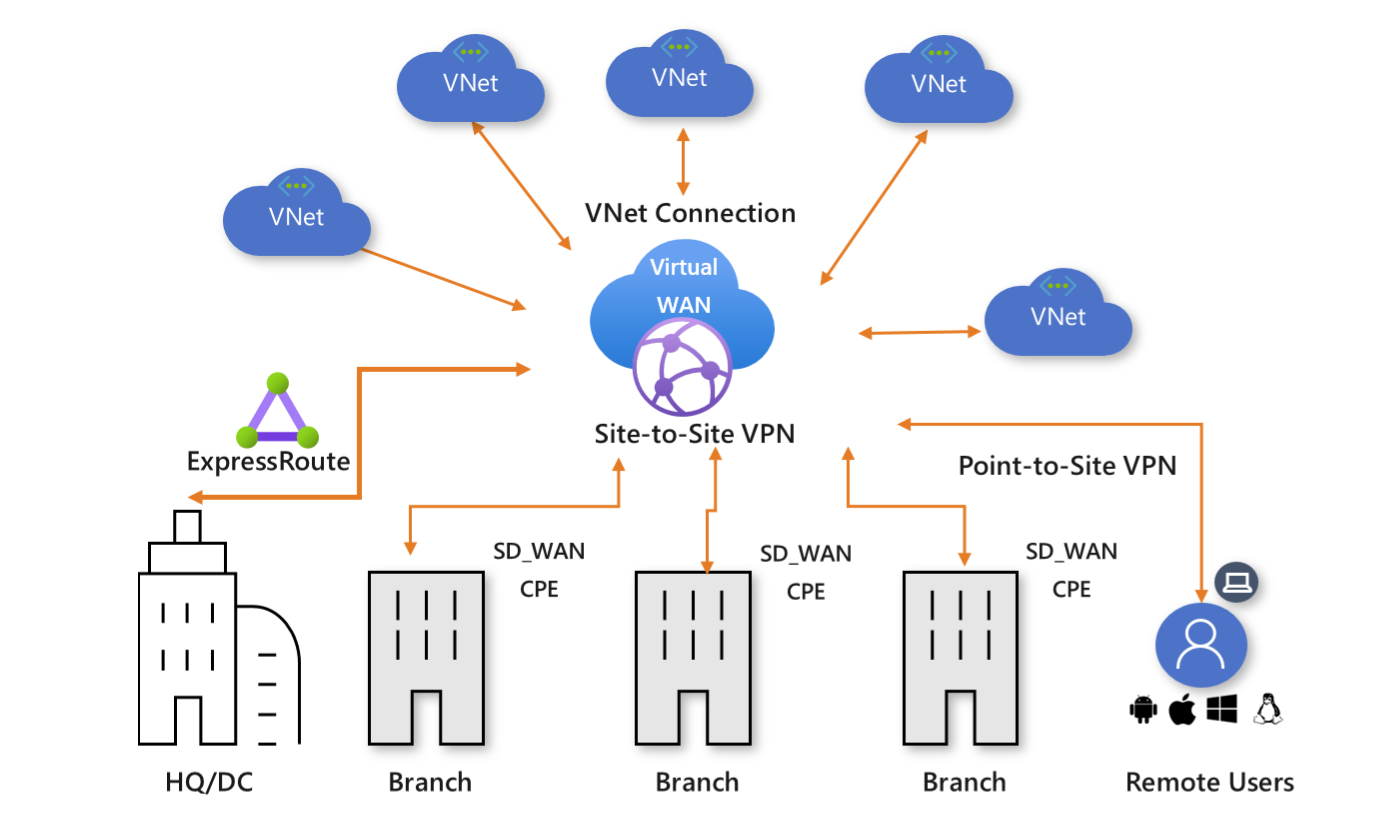
Illustration of Azure Virtual WAN from Microsoft (see reference below)
Microsoft says its Virtual WAN offers the following advantages:
- Integrated connectivity solutions in hub and spoke: Automate site-to-site configuration and connectivity between on-premises sites and an Azure hub.
- Automated spoke setup and configuration: Connect your virtual networks and workloads to the Azure hub seamlessly.
- Intuitive troubleshooting: You can see the end-to-end flow within Azure, and then use this information to take required actions.
………………………………………………………………………………………………………………………………………………………….
Barracuda said that their CloudGen WAN architecture can replace costly, inflexible network connectivity circuits, and the entire network can be dynamically sized to match current traffic workload, which can optimize network performance and minimize cost.
“A cloud-first strategy asks for a different approach on connectivity,” said Leon Sevriens, program manager, IT at Humankind, a large organization in the Netherlands that offers daycare and after-school care, with over 3,000 employees and over 450 locations. “We have invested heavily in Microsoft Office 365 adoption across the organization, and traditional connectivity doesn’t fit the bill anymore. We need a solution that is focused on delivering application performance, not just ‘plain’ connectivity. That’s why we’re moving forward with Barracuda CloudGen WAN,” he added.
In the recent report “Secure SD-WAN: The Launch Pad into Cloud,” Barracuda found that SD-WAN is being used by more than half of those who have added security to their public cloud. As the report explains, “SD-WAN can help overcome the top two security challenges organizations are facing when it comes to public cloud: lack of access control and backhauling traffic.”
Cloud-native, secure SD-WAN:
The perimeter is changing, and organizations need to be ready to adapt. According to Gartner, “The enterprise perimeter is no longer a location; it is a set of dynamic edge capabilities delivered when needed as a service from the cloud.”1
Secure SD-WAN services built natively on the cloud combine ease of use, full security, and cloud-scalable SD-WAN connectivity to use the Microsoft Global Network as the WAN backbone instead of leased lines. The new Barracuda CloudGen WAN is a SaaS service deployed directly from the Azure Marketplace for as many regions as needed and administered centrally in the CloudGen WAN portal for all office locations and remote endpoints. Since the Microsoft Global Network is automatically provisioned as the backbone for anywhere, anytime application access, service providers can create a pragmatic SASE solution in the public cloud tailored to their specific needs.
“With an all-in-one, secure SD-WAN solution natively built on the public cloud network, enterprises can finally make the shift to more public cloud deployments, both faster and more securely,” said Hatem Naguib, COO at Barracuda. “We appreciate the relationship we have developed with Microsoft over the years and the close collaboration over many months to integrate Barracuda SD-WAN technology natively on Microsoft Azure Virtual WAN Hubs. We know this is the future of networking in the public cloud, and we’re excited to be on this forefront with Microsoft.”
Yousef Khalidi, Corporate Vice President, Azure Networking at Microsoft said, “Cloud-native, secure SD-WAN technology, like the new CloudGen WAN service from Barracuda, provides a fast, reliable, and direct path to Microsoft Azure. We’re pleased to collaborate with Barracuda for this new wave of faster public cloud adoption to help our joint customers optimize network performance.”
Opinion: The huge implication here is that the major cloud service providers (Amazon AWS, Microsoft Azure and Google Cloud) will be replacing traditional telco networks. In this case, it’s SD-WAN access and Microsoft’s WAN backbone, but in the future it will likely be 5G network access built mostly from software building blocks. Why else did Microsoft acquire Affirmed Networks and Metaswitch?
For an Amazon AWS executive’s take on this topic (“we’re partners with telco’s”) read this Light Reading piece.
………………………………………………………………………………………………………………………………………………………………….
References:
https://docs.microsoft.com/en-us/azure/virtual-wan/virtual-wan-about
Will Hyperscale Cloud Companies (e.g. Google) Control the Internet’s Backbone?
Resources from Barracuda:
For more information about Barracuda CloudGen WAN, visit https://www.barracuda.com/products/cloudgenwan
Read the Barracuda blog post: http://cuda.co/40855
Read the Microsoft blog post from Yousef Khalidi: https://aka.ms/vwan-sdwan
Watch Reshmi Yandapalli’s session on “Use Azure networking services to accelerate, scale or re-architect your customer’s global network” for Microsoft Inspire: https://aka.ms/T4D193
Read the market report: https://www.barracuda.com/sdwan-report-2020
Find out Barracuda was recognized as a finalist for Commercial Marketplace 2020 Microsoft Partner of the Year: http://cuda.co/40853
1 Gartner, “The Future of Network Security Is in the Cloud”, Neil MacDonald, Lawrence Orans, Joe Skorupa, 30 August 2019.
……………………………………………………………………………………………………………………………………………………………………………
Futurium: 2020 SD-WAN market set to accelerate
Despite no standards for multi-vendor operator (UNI) or network-to-network (NNI), Futurium projects continued growth in SD-WAN through at least the next 3-5 years. Enterprises and service providers alike are interested in deploying SD-WAN technology in services to deliver cloud-based orchestration and automation of networking and security.
Based on a survey of 100 end users as well as dozens of interviews with professionals in the IT and networking markets, Futurium forecasts the SD-WAN tools and software market will increase to $4.6 billion by 2023 as enterprises increasingly move their IT and networking services to a cloud infrastructure.
In the nearer term, Futuriom’s founder and principal analyst, Scott Raynovich, expects a market growth rate of 34% CAGR to hit $2 billion this year and reach $2.85 billion in 2021 as more enterprises demand “agile, high-performance, and secure connections to cloud applications.”
Cloud-delivered SD-WAN, a growing technology domain that enables enterprises and organizations to set up and manage secure WAN connections using cloud software deployment and management approaches, is gaining and increasing role to speed up and secure cloud connectivity. Enterprises are buying SD-WAN to reduce the complexity in configuring branch-office devices, routing schemes, and network addresses. With SD-WAN, many of these functions can be abstracted into the cloud and managed by the service provider or an enterprise manager using a cloud interface, rather than using proprietary networking equipment.
The report was sponsored by Aryaka Networks, Citrix Systems, Fortinet, Nuage Networks, Silver Peak, Versa Networks, and VMware (VeloCloud).
Report highlights:
- Momentum in the SD-WAN market continues. Despite a slight slowdown in the 1H due to pandemic-related supply chain and sales challenges, the market is likely to accelerate in 2H 2020 and into 2021 as the features of SD-WAN serve growing cloud demand.
- Futuriom expects the SD-WAN tools and software market to accelerate to a growth rate of 34% CAGR to reach $2.0 billion in 2020, $2.85 billion in 2021, and $4.6 billion by 2023. The acceleration will be spurred by demand for more agile, high-performance, and secure connections to cloud applications.
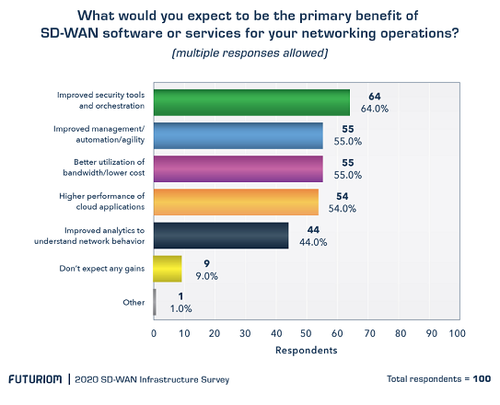
- The top four benefits of SD-WAN adoption include improved security, better management/agility, bandwidth optimization/cost savings, and faster cloud applications performance. These benefits were picked in our Futuriom 2020 SD-WAN Infrastructure Survey of 100 enterprise end users, which also indicated broadening use cases and adoption in the market.
- Awareness of SD-WAN is growing as the market matures. In the Futuriom 2020 survey, 92% of respondents said they are evaluating SD-WAN services and/or software.
- The Work from Home (WFH) trend is giving the SD-WAN market a boost. SD-WAN integrates virtual private networking (VPN) functionality for both remote workers and enterprises branches, which is a key feature demand.
- As predicted in 2019, M&A and consolidation has continued and is likely to continue. The acquisition leaves fewer players on the dance floor. Aryaka, Cato Networks, FatPipe, Silver Peak, and Versa Networks are all strong candidates for M&A or IPO. (Last year, CloudGenix was on this list – Palo Alto Networks announced earlier this year that it’s acquiring the startup.)
- Companies featured in this report: Adaptiv Networks, Aryaka Networks, Bigleaf Networks, Cisco Systems (Viptela), Cato Networks, Citrix Systems, CloudGenix (Palo Alto Networks), HPE, FatPipe Networks, Fortinet, Juniper Networks, Nuage Networks (Nokia), Riverbed, Silver Peak, Versa Networks, VMware (VeloCloud).
……………………………………………………………………………………………………………………………………………………….
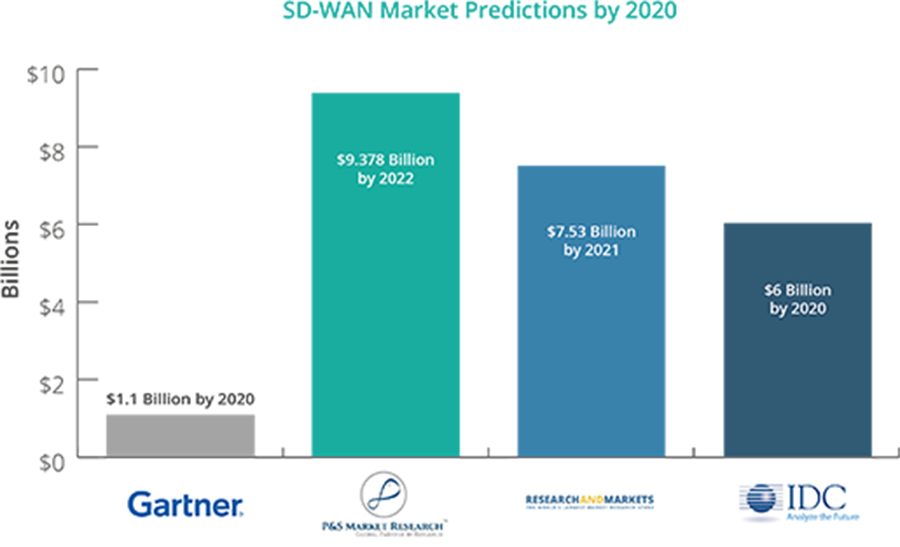
In April, Omdia released similar predictions for the SD-WAN market, reporting that SD-WAN revenue reached $2 billion in 2019, up from $1.1 billion in 2018. Omdia predicts SD-WAN revenue will hit $4.8 billion in 2024.
While the COVID-19 pandemic slowed SD-WAN market momentum in the first half of 2020, Raynovich forecasts a pickup in the market in the second half of 2020 and into 2021 as more enterprise employees are working from home and require secure, remote access services.
“Enterprises aren’t going to pay for people to have MPLS in their home, it’s too expensive. SD-WAN is serving its role as a quick, secure VPN for work-from-home situations. That’s a driver of growth,” Raynovich told Light Reading. SD-WAN is continuing to reduce dependence on MPLS and is becoming “one of the go-to solutions to work from home where there is no alternative,” he said.
IT and networking professionals cited “improved security tools and orchestration” (64%) as the top benefit of utilizing SD-WAN in their networks, according to a Futuriom survey of 100 networking and cybersecurity professionals. About 55% of respondents also cited improved management/automation/agility; better utilization of bandwidth/lower cost; and higher performance of cloud applications as the primary benefits of SD-WAN. As network security is a top priority for enterprises, the majority of SD-WAN vendors have added cloud security and next-generation firewall products from security suppliers such as Check Point, Zscaler and Palo Alto, according to the report.
…………………………………………………………………………………………………………………………………………………..
Separately,
Market Research Inc has recently published a new market assessment report titled “Global SD-WAN Market – Growth, Future Scenarios, and Competitive Analysis, 2019 – 2025”. The market study provides an extensive understanding of the present-day and forthcoming stages of the industry market based on factors such as major sought-after events, research ingenuities, management stratagems, market drivers, challenges and visions and all-encompassing industry subdivision and regional distribution.
A key utilization of SD-WAN is to enable organizations to fabricate higher-execution WANs utilizing lower-cost and economically accessible Internet get to, empowering organizations to mostly or entirely supplant progressively costly private WAN association innovations, for example, MPLS. The global market is forecasted to expand rapidly at a compound annual growth rate (CAGR) of +35%.
Request a Sample of this Report and Analysis of Key Players at https://www.marketresearchinc.com/request-sample.php?id=15951
……………………………………………………………………………………………………………………………………………………….
References:
https://www.lightreading.com/sd-wan/sd-wan-market-to-exceed-$4b-by-2023—report/d/d-id/761907?
Dell’Oro: Data Center Switch market declined 9% YoY; SD-WAN market increased at slower rate than in 2019
Market research firm Dell’Oro Group reported today that the worldwide Data Center Switch market recorded its first decline in nine years, dropping 9 percent year-over-year in the first quarter. 1Q 2020 revenue level was also the lowest in three years. The softness was broad-based across all major branded vendors, except Juniper Networks and white box vendors. Revenue from white box vendors was propelled mainly by strong demand from Google and Amazon.
“The COVID-19 pandemic has created some positive impact on the market as some customers pulled in orders in anticipation of supply shortage and elongated lead times,” said Sameh Boujelbene, Senior Director at Dell’Oro Group. “Yet this upside dynamic was more than offset by the pandemic’s more pronounced negative impact on customer demand as they paused purchases due to macro-economic uncertainties. Supply constraints were not major headwinds during the first quarter but expected to become more apparent in the next quarter,” added Boujelbene.
Additional highlights from the 1Q 2020 Ethernet Switch – Data Center Report:
- The revenue decline was broad-based across all regions but was less pronounced in North America.
- We expect revenue in the market to decline high single-digit in 2020, despite some pockets of strength from certain segments.
The Dell’Oro Group Ethernet Switch – Data Center Quarterly Report offers a detailed view of the market, including Ethernet switches for server access, server aggregation, and data center core. (Software is addressed separately.) The report contains in-depth market and vendor-level information on manufacturers’ revenue; ports shipped; average selling prices for both Modular and Fixed Managed and Unmanaged Ethernet Switches (1000 Mbps,10, 25, 40, 50, 100, 200, and 400 GE); and regional breakouts. To purchase these reports, please contact us by email at [email protected].
…………………………………………………………………………………………………………………………………………………
Separately, Dell’Oro Group reported that the market for software-defined (SD)-WAN equipment increased by 24% in the first quarter (year-to-year), which was significantly below the 64% growth seen in 2019. Citing supply chain issues created by the coronavirus pandemic, the market research firm’s Shin Umeda predicted the market will post double-digit growth in 2020 despite “macroeconomic uncertainty.”
- Supply chain disruptions accounted for the majority of the Service Provider (SP) Router and CES Switch market decline in 1Q 2020.
- The SP Router and CES market in China showed a modest decline in 1Q 2020, but upgrades for 5G infrastructure are expected to drive strong demand over the rest of 2020.