Enterprises Deploy SD-WAN but Integrated Security (SASE) Needed
A new IDC study, commissioned by GTC, reveals that over 95% of enterprises have deployed software-defined wide area networks (SD-WANs) or plan to do so within the next 24 months. However, nearly half (42%) reported they either don’t have security integrated with SD-WAN or have no specific SD-WAN security at all.
Enterprises today are facing what IDC calls “storms of disruption:” waves of economic, political, and social disruptions that are hampering companies’ efforts to become “truly digital enterprises” – like the Russia-Ukraine war, global recession, and industry-wide skills gaps. Networks need to support businesses in their move toward a cloud-native, digital-first, hybrid-working model of operation, and SD-WAN is now a cornerstone of network transformation, IDC stated in its GTT-commissioned study.
When asked to list the challenges they faced when taking a do-it-yourself (DIY) approach to SD-WAN, respondents cited difficulties related to hiring and retaining a skilled in-house workforce, keeping up with technology developments and the ability to negotiate favorable terms with technology vendors.
“Now that SD-WAN has matured and has been widely adopted, the complexity of deployments has grown, challenging enterprises on multiple fronts and compromising their ability to realize the full benefits of the technology,” said James Eibisch, research director, European Infrastructure and Telecoms, IDC.
“Enterprises are increasingly reliant on the resources and expertise of a managed service provider to ensure they deploy SD-WAN in a way best suited to their meet their organizations’ objectives. Security approaches like Secure Access Service Edge (SASE) [1.] that combine the benefits of SD-WAN with zero trust network access and content filtering features are well poised to dominate the next phase of SD-WAN enhancements as enterprises continue to enable the cloud IT model and a hybrid workforce.”
Note 1. SASE, when combined with a SD-WAN overlay network, is seen as a less expensive way to get circuits exactly where they are needed — especially to remote locations — than using traditional architectures like IP-MPLS. Scaling the enterprise WAN out to more user devices and more locations also becomes easier, a necessity at a time when hybrid and remote working continues to be popular.
…………………………………………………………………………………………………………………………………………………………..
The IDC survey found that more than 80% of respondents worldwide have either made SASE a priority (39%) or have recognized its benefits and are already incorporating it into company initiatives (42%). Only 19% of respondents worldwide reported they do not view SASE as a priority.
Despite this widespread recognition of the value of integrating security and SD-WAN, the survey found that many enterprises have not been able to leverage these benefits. In the U.S., 45% of respondents said they either don’t have security integrated with SD-WAN or have no specific SD-WAN security at all. In some countries, such as Switzerland and France, that figure was more than 50%. This trend held across vertical industries such as manufacturing (47%), retail (46%), healthcare (47%) and transportation (49%). Financial and business services were exceptions, with only 32% and 34%, respectively. Seven out of 10 respondents (71%) worldwide expect to use integrated security in the next 12 months.
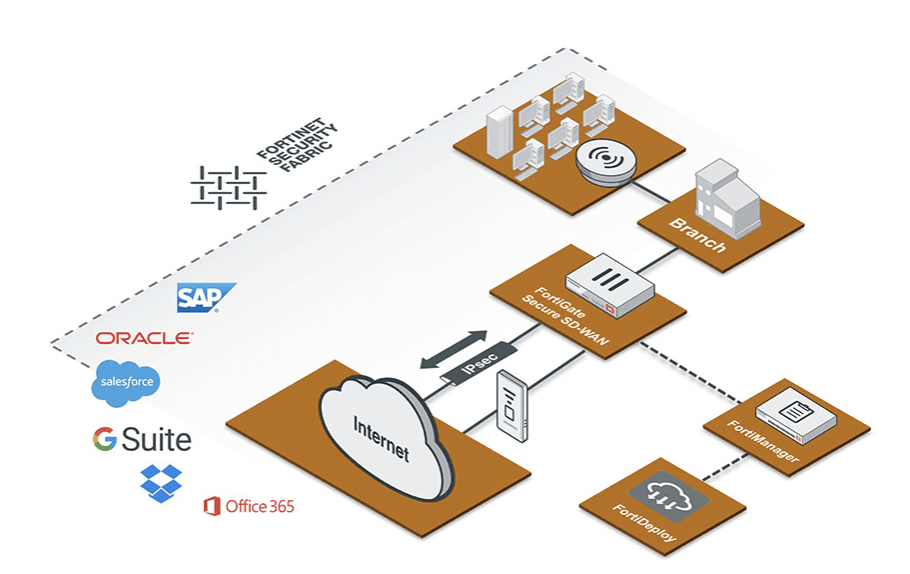
Image Credit: Fortinet
“This IDC study highlights the critical role of expert managed services support for enterprises deploying SD-WAN. Experienced managed services providers can help integrate technology, connectivity and security, while also managing costs and increased complexity,” said Lisa Brown, CMO at GTT. “The research shows that a DIY approach to SD-WAN presents a number of challenges that can be addressed by teaming with a managed services provider.”
When respondents who were adopting a managed services approach to SD-WAN were asked for their reasons, many said they wanted to outsource day-to-day management tasks. The top reason cited by respondents globally for using a managed services provider was the benefit of always-on help desk support in local languages, with 36% citing this as a reason. Running a close second, 35% cited visibility, insights and control without the need for technology certification as a benefit. In addition, 34% cited ease of configuration management; the ability to manage, maintain and facilitate technology upgrades; and better protection against security threats.
Todd Kiehn, SVP at GTT, told SDxCentral, “There will be a continued evolution to SD-WAN integrated with cloud security over the coming year. The IT organization is going to require ever-increasing visibility into the actions of the end user. Consistently through our customers, prospects, CIO roundtables and through this recent research, the biggest obstacle enterprises are having in implementing new security solutions is finding and securing a staff with the necessary skills. The cybersecurity skill shortage particularly is a global problem.”
Companies that have no position on SD-WAN-specific security yet face the challenge of adopting these new technologies on their own or through managed service provider partnerships — either of which take time and resources.
“Enterprises can view SASE as a security architecture transformation alongside the deployment of SD-WAN. Our customers are deploying security to support their varied digital transformation initiatives such as work from anywhere, branch transformation or cloud migrations,” Kiehn noted.
“Security solutions based on the SASE framework provide choice and a roadmap to address the specific business needs of the enterprise such as enhancing the security posture of mobile users by replacing legacy VPN technology, improving security for guests and employees at brick and mortar locations, and developing a more comprehensive posture to support a hybrid cloud model,” Kiehn added.
About GTT:
GTT is a managed network and security services provider to global organizations. We design and deliver solutions that leverage advanced cloud, networking and security technologies. We complement our solutions with a suite of professional services and exceptional sales and support teams in local markets around the world. We serve thousands of national and multinational companies with a portfolio that includes SD-WAN, security, Internet, voice and other connectivity options. Our services are uniquely enabled by our top-ranked, global, Tier 1 IP backbone, which spans more than 260 cities on six continents. The company culture is built on a customer-first service experience reinforced by our commitment to operational excellence and continuous improvement in our business, environmental, social and governance practices. For more information, visit www.gtt.net.
References:
https://www.sdxcentral.com/networking/sd-wan/definitions/software-defined-sdn-wan/
https://www.sdxcentral.com/articles/news/sd-wan-security-needs-a-refresh-idc-says/2022/11/
MEF survey reveals top SD-WAN and SASE challenges
Omdia: VMware and Versa Networks are SD-WAN revenue leaders; SD-WAN market to hit $6.7B by 2026
AT&T tops VSG’s U.S. Carrier Managed SD-WAN Leaderboard for 4th year
Dell’Oro: SD-WAN market grew 45% YoY; Frost & Sullivan: Fortinet wins SD-WAN leadership award
MEF New Standards for SD-WAN Services; SASE Work Program
VSG Global SD-WAN Leaderboard Rankings and Results
3 thoughts on “Enterprises Deploy SD-WAN but Integrated Security (SASE) Needed”
Comments are closed.



Verizon said in its guide for the “right approach” to secure access service edge (SASE) – the Gartner-coined infrastructure that combines cloud-native network and security stacks- that managing and securing an increasingly complex environment poses “significant challenges.”
https://www.verizon.com/business/resources/T8d/whitepapers/the-right-approach-to-sase.pdf
In 2021 Verizon Business launched SASE solution with a multi-vendor approach that combines SD-WAN and network security capabilities from Versa Networks and Zscaler into a single managed service. Rival AT&T had rolled out its own solution earlier that year in partnership with Fortinet.
Verizon cites the COVID-19 pandemic, virtualization and the move to the cloud, increased security threats, and a shift away from the network appliance box as the primary factors that drove the “SASE frenzy” in recent years.
By 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018, according to the Verizon guide.
“Getting SASE right may be a complex proposition that presents significant challenges,” the provider said. “For one thing, it is a still-evolving technology target.”
The SASE architecture combines network edge capabilities like SD-WAN and a set of security capabilities Gartner dubbed the security services edge (SSE) – a cloud-delivered suite that includes zero-trust network access (ZTNA), cloud-access security broker (CASB), secure web gateway (SWG), and firewall-as-a-service (FWaaS).
The major elements that make up SASE have been around in some form or another for “at least 10 years,” Verizon pointed out.
For this reason, a critical component of getting SASE right is cross-technology integration. “There’s no one-size-fits-all SASE solution, which means enterprises will need to be comfortable working with a variety of technologies in order to build an effective implementation that solves a given organization’s specific challenges,” the provider said.
Enterprises adopting SASE need to be able to integrate a broad range of network technologies from physical transport – like private IP and MPLS – up through the virtualization SDN layer in order to build an integrated SD-WAN capability with traffic routing, prioritization, and bandwidth optimization.
Another “key ingredient” to SASE is edge computing like content delivery networks, multi-access edge computing (MEC), or an IoT gateway. “Managing security across these complex and distributed systems will be essential and require a deep understanding of how edge computing fits into the SASE model,” Verizon explained.
Orchestrating SASE Infrastructure
How the technology components of SASE come together is critical.
Verizon recommends enterprises implement service chaining as a key component of SASE because it is a “way of automating and optimizing the service delivery experience.”
In an environment where many vendors are still unable to provide a complete end-to-end SASE solution, organizations likely need to combine technologies and products to create their desired solutions. “Being able to optimize new and already-deployed technology components so each is functioning and contributing at its full potential will be important,” Verizon said.
The ability to conduct testing to make sure SASE is properly integrated and performing at necessary levels will also be critical. Verizon indicated this requires the “proper tools to conduct the integration, performance, and stress testing needed to ensure that functions have been deployed in the optimal order and the most efficient configuration.”
Service chaining and other orchestration in a virtual network requires expertise, which has led to challenges for many organizations in the midst of a global skill shortage. However, this can be mitigated in part through organizational restructuring that sees networking and security teams – which have traditionally operated separately – merge their administration and management from the organizational perspective.
Lastly, Verizon suggested that because SASE is still a work in progress, “CIO and CISO groups will need to rethink their respective roles in supporting enterprise infrastructure operations.”
“Proper governance will be key to success as these changes percolate down through the organization, as they will eventually touch the network architects, security architects, application architects and others that need to work together to execute on a company’s SASE strategy,” Verizon added.
https://www.sdxcentral.com/articles/analysis/verizons-critical-components-to-getting-sase-right/2022/11/
Security Service Edge vs. SASE: What Is the Difference?
Secure Access Service Edge (SASE) is a category of networking solutions defined by Gartner in 2019, which combines traditional network security functions with wide area networking (WAN) capabilities. The goal of SASE is to provide secure and reliable connectivity for users and devices, regardless of their location or the type of network they are connected to.
Gartner defines SASE as a cloud-delivered, network security as a service platform that provides secure network connectivity and network security functions in a unified offering, delivered through a common infrastructure and management. SASE combines network security functions, such as zero trust networking, firewalls, and intrusion prevention systems (IPS), with cloud-based networking services like SD-WAN (software-defined wide area networking) and internet connectivity.
……………………………………………………………………..
Secure Services Edge (SSE) is a set of integrated, cloud-delivered secure services that use identities and policies to establish secure connections between authenticated users and business resources. First introduced by Gartner in 2021, SSE is a security category that will secure connectivity in the future of hybrid environments and remote work.
As more employees work outside corporate boundaries, SaaS applications become the norm, and applications move to the public cloud, organizations cannot continue to backhaul user traffic to corporate networks. Many IT organizations are replacing their existing network security appliances, such as firewalls, VPN gateway appliances, and web gateways, with cloud-based options that can better protect data, provide a better user experience, and reduce costs.
SSE platforms provide cloud services that extend secure connectivity to user locations, without connecting users to corporate networks, exposing IT infrastructure to the public internet, or requiring complex network segmentation. Instead, SSE allows IT to provide secure access from anywhere to on-premise applications, secure access to the internet, and fast access to the cloud and SaaS applications.
………………………………………………………………………………………..
Security Service Edge vs. SASE: What Is the Difference?
The main difference between Secure Access Service Edge (SASE) and Security Service Edge (SSE) is the focus of the solutions. SASE combines traditional network security functions with wide area networking (WAN) capabilities, while SSE focuses specifically on security functions.
SASE solutions are designed to provide secure and reliable connectivity for users and devices, regardless of their location or the type of network they are connected to. This can include traditional networking functions like VPNs and SD-WAN (software-defined wide area networking), as well as security functions like firewalls, intrusion prevention systems (IPS), and other controls. SASE solutions are often used by organizations with remote and hybrid workforces to ensure secure access to corporate resources and protect against cyber threats.
https://wire19.com/security-service-edge-vs-sase-difference/
From Fierce Telecom January 12, 2023:
Randy Anders is VP of North American sales with HughesNet for Business. He said HughesNet has been providing SD-WAN to enterprise customers for several years, using its GEO satellite connectivity.
The company works with VMware, Cisco Meraki and Fortinet for the SD-WAN technology.
“We have over 52,000 SD-WAN locations and over 100 customers in the U.S. over retail, healthcare, banking, energy, restaurants and government customers,” said Anders. For instance, it connects about 2,000 gas stations in far-flung locations with SD-WAN.
He did concede that with GEO “you have the latency issue because the satellite is so much further from earth” than with LEO. But HughesNet and its partners use compression software “to make the user experience better.”
Hughes is also establishing a partnership with the LEO satellite company OneWeb. Together they’ll be able to provide LEO and GEO connectivity to suit a customer’s specific needs.
“We’ve been involved with OneWeb for a few years,” said Anders. “We’ve actually done deals where they bought 10,000 of our electronically steerable antennas.”
There’s a huge difference in the number of satellites needed for GEO as opposed to LEO.
Starlink has more than 3,000 satellites in orbit and has recently received FCC approval to launch 7,500 more. As if that’s not enough Starlink wants to launch about 20,000 more on top of that.
In comparison, Hughes needs only a handful of satellites — it uses a few of its own and has hosted payloads on a few others.
The FCC is very concerned about space debris from all the companies that are entering the satellite business.
RELATED: How does SpaceX remove old, obsolete satellites from space?
SpaceX has developed technology that can control the de-orbiting of its satellites once they reach the end of their life. Once the satellites de-orbit, they pass through the earth’s atmosphere and burn up.
But it’s different for GEO satellites. First, there are far fewer of them. Once they reach the end of their life, they move out of their operating orbit and drift further out into space.
https://www.fiercetelecom.com/telecom/hughes-geo-satellites-can-do-sd-wan-too