Month: January 2023
SK Telecom inspects cell towers for safety using drones and AI
SK Telecom, South Korea’s largest wireless carrier, announced on Tuesday that it’s developed a new cell tower safety inspection system using drones and image analysis artificial intelligence (AI). The newly-developed image analysis AI model checks the status of nuts and bolts by analyzing images taken by drones.
Cell towers with antennas for sending and receiving telecommunications signals are installed across the country, with their maximum height estimated at 75 meters. Since cell towers require regular maintenance to prevent accidents that can be caused by deterioration such as corrosion or loosening of nuts and bolts, specialized personnel had to climb them to inspect their condition with their bare eyes.
Engineers from a subsidiary of SK Telecom Co. inspect a cell tower in this photo provided by the wireless carrier on Jan. 31, 2023.
…………………………………………………………………………………………………………………………………………….
Now with an intelligent safety inspection system in place, not only can SK Telecom prevent accidents due to aging cell towers, but it can also ensure the safety of workers by minimizing the need to go up the cell towers. Moreover, the company can drive up work productivity through the application of an AI model that automatically identifies defects by analyzing images taken by drones.
Previously, safety inspectors had to study around 100 images to complete the inspection of one cell tower by inspecting multiple images taken by drones. With the adoption of the new AI analysis model, SK Telecom has been able to reduce the time required for the process by 95%, while increasing the reliability and consistency of the analysis results.
The company says, going forward, it will enhance the system even further by adding inspection items such as wind pressure safety/inclination. It will also look to improve the AI model and link the application with the safety management system.
In addition to drone-based cell tower inspections, the telecom company is actively applying AI to other areas of its network, including equipment error/anomaly detection, power cost reduction, and work completion inspection.
Park Myung-soon, SKT’s vice president and head of Infra DT Office, said: “By building an intelligent safety inspection system that can complement the existing visual inspection, we have secured greater safety for workers. We will continue to make efforts to achieve AI transformation of our telecommunication networks, while focusing on developing our field workers into experts who can develop and operate AI.”
References:
http://koreabizwire.com/sk-telecom-inspects-cell-towers-using-drones-and-ai/239441
South Korean telecom giant innovates safety inspection with drones
Nordic Semiconductor announces ICs & development kits for low power Wi-Fi 6 IoT applications
Nordic Semiconductor today announced the availability of the nRF7002™ Wi-Fi 6 companion IC and its associated nRF7002 Development Kit (DK). The IC is the first in Nordic’s Wi-Fi product family and is a low power Wi-Fi 6 companion IC providing seamless dual band (2.4 and 5 GHz) connectivity. The nRF7002 IC can be used together with Nordic’s award-winning nRF52® and nRF53® Series multiprotocol Systems-on-Chip (SoCs) and the nRF9160™ cellular IoT (LTE-M/NB-IoT) System-in-Package (SiP), but can equally be used in conjunction with non-Nordic host devices. The DK makes it easy for developers to get started on nRF7002-based IoT projects.
The nRF7002 complements Nordic’s cellular IoT and multiprotocol wireless solutions. By using the new IC, developers can leverage Wi-Fi 6’s higher throughput and ubiquitous domestic and industrial infrastructure when developing IoT applications. Design support through Nordic’s unified software development kit, nRF Connect SDK, and the nRF7002 DK make it easier and quicker to launch new products.
Wi-Fi 6 brings significant benefits to IoT applications—such as smart-home products, industrial sensors, asset trackers, and wearables—including power efficiency gains for battery powered Wi-Fi operation, and management of large IoT networks comprising hundreds of devices.
“The nRF7002 Wi-Fi 6 companion IC is a testament to Nordic Semiconductor’s leadership in low-power wireless technology,” says Svein-Egil Nielsen, CTO/EVP of R&D and Strategy at Nordic. “This highly integrated and flexible solution will empower developers to create new, innovative Wi-Fi 6-enabled products. Supported with the nRF7002 DK and the award-winning nRF Connect SDK, combined with Nordic’s best in class technical support, I believe it has never been easier to develop great Wi-Fi products.”
“The nRF7002 is designed to work alongside Nordic’s nRF52 and nRF53 Series making it a perfect fit for Matter, a smart-home standard backed by Amazon, Apple, Google, Nordic, Samsung, and hundreds of other companies,” says Finn Boetius, Product Marketing Engineer with Nordic. “The introduction of the IC and the nRF7002 DK now makes it easy for developers to get started on Matter and any other Wi-Fi based applications.” Matter uses Thread and Wi-Fi for data transport, and Bluetooth LE for commissioning.
The nRF7002 brings low power and secure Wi-Fi to the IoT. The dual-band IC complies with Station (STA), Soft Access Point (AP), and Wi-Fi Direct operation, and meets the IEEE 802.11b, a, g, n (“Wi-Fi 4”), ac (“5”), and ax (“6”) Wi-Fi standards. The product also offers excellent coexistence with Bluetooth LE, Thread, and Zigbee. The nRF7002 supports Target Wake Time (TWT) a key Wi-Fi 6 power saving feature. Interfacing with a host processor is done via Serial Peripheral Interface (SPI) or Quad SPI (QSPI). The IC offers a single spatial stream, 20 MHz channel bandwidth, 64 QAM (MCS7), OFDMA, up to 86 Mbps PHY throughput, and BSS coloring.
In addition to its suitability for general IoT applications and Matter, the nRF7002 is the ideal choice for implementing low power SSID-based Wi-Fi locationing when used together with Nordic’s nRF9160 SiP and the company’s nRF Cloud Location Services. SSID-based Wi-Fi locationing supplements GNSS- or cell-based locationing by providing accurate positioning indoors and in places with a high density of Wi-Fi access points.
nRF7002 DK supports development of low power Wi-Fi applications:
The introduction of the nRF7002 is accompanied by the launch of the nRF7002 DK, a development kit for the Wi-Fi 6 companion IC. The DK includes an nRF7002 IC and features an nRF5340 multiprotocol SoC as a host processor for the nRF7002. The nRF5340 embeds a 128 MHz Arm Cortex-M33 application processor and a 64 MHz high efficiency network processor. The DK supports the development of low-power Wi-Fi applications and enables Wi-Fi 6 features like OFDMA, Beamforming, and TWT. The DK includes: Arduino connectors; two programmable buttons; a Wi-Fi dual-band antenna and a Bluetooth LE antenna, and current measurement pins.
nRF7002 DK – Development Kit for nRF7002 Wi-Fi 6 IC:
.png?h=754&iar=0&mw=350&w=350&hash=1DF0EC6A97E1329DCCD435B7FDBF0B90)
Source Nordic Semiconductor
Together with the DK, developing nRF7002-based designs is made simpler by the support for the IC in the nRF Connect SDK, Nordic’s scalable and unified software development kit for building products based on the company’s wireless devices. With the nRF7002 IC, nRF7002 DK, and nRF Connect SDK, developers can quickly and easily add Wi-Fi connectivity to their products, allowing them to connect to the Internet and communicate with other devices over a Wi-Fi network. Example applications for the nRF7002 DK are included with nRF Connect SDK.
The nRF7002 companion IC and nRF7002 DK are available now from Nordic’s distribution partners.
……………………………………………………………………………………………………………………………………………………….
References:
https://www.nordicsemi.com/Products/nRF7002
https://www.nordicsemi.com/Products/Development-hardware/nRF7002-DK
Frontier Communications offers first network-wide symmetrical 5 Gig fiber internet service
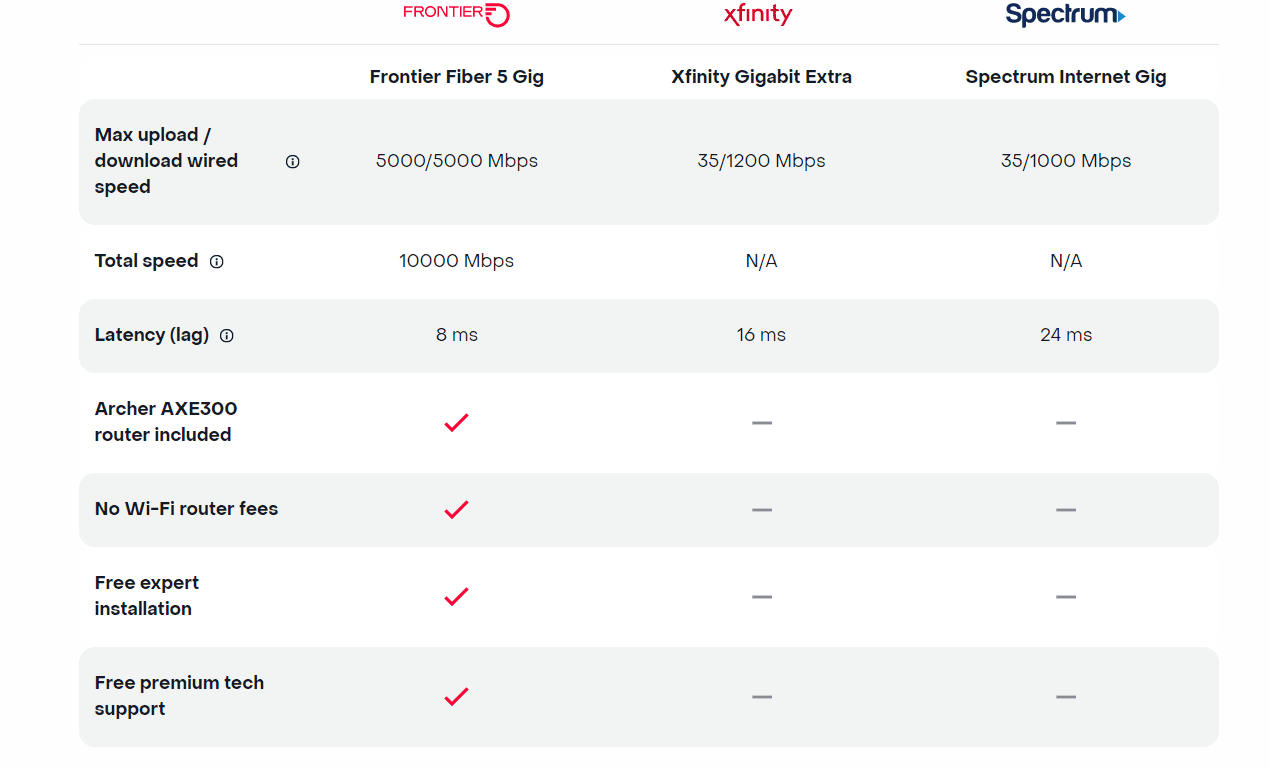
Today, Frontier Communications launched the nation’s only network-wide 5 Gig fiber internet service. With the launch of 5 Gig, Frontier will provide customers across its 25 state fiber network – not just select markets – the opportunity to sign up for the new premium service with blazing-fast speeds. The company says that 5 Gig internet has 125x faster upload speeds, 5x faster download speeds and 2.5x less latency than cablecos [1.], but they don’t specify the cable network speeds or latency.
Note 1. Comcast currently offers 1 and 2 Gig Internet. The company announced a successful trial of the world’s first live, multigigabit symmetrical Internet connection powered by 10 Gbps and Full Duplex DOCSIS 4.0 last December. Charter Communications is also planning a DOCSIS 4.0 upgrade to deliver download speeds of 5 Gbps and 10 Gbps over the coming years, but isn’t currently planning to bring symmetrical service offerings to market.
Frontier’s 5 Gig fiber internet service enables customers to run multiple connected devices at their fastest possible speeds. This means:
- Symmetrical download and upload speeds at up to 5 gigabits per second
- 125x faster upload speed than cable
- 1.6 seconds to download Adobe Photoshop on PC (1GB)
- <36 seconds to download a House of Dragons episode in 4K (22 GB)
- <2 minutes to download a 100-minute 8K movie (67 GB)
- 99.9% network reliability
The 5 Gig internet offer starts at $154.99 a month with autopay and includes uncapped data + Wi-Fi router + free installation + premium tech support. There are no additional Wi-Fi or router fees, no data caps or overage charges. The inclusion of a Archer AXE300 Wi-Fi 6E router is a major advantage, because most installed WiFi routers are WiFi 5= IEEE 802.11ac which won’t support giga bit speeds.
Frontier also dropped the price of its 2-gig internet service, which debuted in February 2022 at a cost of $149.99 per month. That service is now priced at $109.99 per month.
New Street Research stated that Frontier’s 5-gig rollout will “help establish Frontier as a leader in network capabilities and drive the message that this is a new Frontier.” The analysts added, “It also helps drive the message that they are delivering a product that Cable can’t.” Furthermore, New Street noted the move could contribute to growth in average revenue per user (ARPU) given the price drop for the 2-gig plan could “drive some incremental demand for that too.”
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
On Frontier’s Q3 2022 earnings call, CEO Nick Jeffrey noted 45% to 50% of new customers were taking its 1 Gbps and 2 Gbps plans. Among its installed base, uptake of 1-gig or faster speeds stood at 15% to 20%. That was up sequentially from 10% to 15% in Q2, Jeffrey said at the time.
Frontier is set to report Q4 2022 earnings on February 24th. In a 4Q 2022 earnings preview, the ISP disclosed it added 75,000 new fiber customers and 8,000 total broadband subscribers in the quarter. That was 17% more fiber broadband customers than it had at the end of 2021. For the fifth consecutive quarter, fiber broadband customer additions outpaced copper broadband customer losses, resulting in 8,000 total broadband customer net additions in the fourth quarter of 2022.
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
Other Competition:
AT&T, Altice USA, Lumen Technologies and Ziply Fiber all already provide symmetrical speeds of 5 Gbps or faster. And Google Fiber has announced plans to debut 5-gig and 8-gig plans early this year. But Frontier claimed it is the only operator thus far to roll out such speeds networkwide.
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
About Frontier Communications:
Frontier is a leading communications provider offering gigabit speeds to empower and connect millions of consumers and businesses in 25 states. It is building critical digital infrastructure across the country with its fiber-optic network and cloud-based solutions, enabling connections today and future proofing for tomorrow. Rallied around a single purpose, Building Gigabit America™, the company is focused on supporting a digital society, closing the digital divide, and working toward a more sustainable environment. Frontier is preparing today for a better tomorrow. Visit frontier.com.
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
Media Contact:
Chrissy Murray, VP, Corporate Communications
+1 504-952-4225 [email protected]
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
References:
https://frontier.com/shop/internet/fiber-internet/5-gig
Frontier Communications adds record fiber broadband customers in Q4 2022
Frontier Communications sets another fiber buildout record; raises FTTP buildout target for 2022
Juniper Research: CPaaS Gobal Market to Reach $29 Billion by 2025
A new study from Juniper Research has found the value of the CPaaS (Communications Platform-as-a-Service) [1.] market will reach $29 billion globally by 2025; rising from $16 billion in 2022. To capitalise on this substantial growth of 80% over the next three years, the report, CPaaS: Market Outlook, Emerging Opportunities & Forecasts 2023-2027, urges CPaaS vendors to focus on the development of managed services over their platforms. These services must enable the creation and management of rich media content over channels such as OTT business messaging, email and social media.
Note 1. Communications Platform as a Service is a cloud-based delivery model that allows organizations to add real-time communications capabilities, such as voice, video and messaging, to business applications by deploying application program interfaces (APIs).
…………………………………………………………………………………………………………………………………………………………
As markets become increasingly saturated with CPaaS service provision, CPaaS vendors must expand deeper into the SME (Small-to-Medium Enterprise) sector. In addition, the report predicts CPaaS vendors will further focus on the provision of value-added features that enable platform users to fully maximise the benefits of rich media channels though the inclusion of tools, including workflow builders and AI-based chatbot solutions.
Research author Sam Barker commented: “CPaaS vendors now compete on the capabilities of managed services to attract SMEs. As many of these smaller enterprises lack in-house development facilities, they will choose the CPaaS platform that provides the most comprehensive managed services for rich media channels.”
Emerging Channels to Disrupt CPaaS in 2023
SMS has historically been the cornerstone of CPaaS revenue. The report predicts SMS traffic revenue will still account for over 50% of all CPaaS revenue by 2025; owing to its established reliability in termination for traffic such as MFA (Multi-factor Authentication).
However, the report forecasts that rich media channels, such as email and social media, will continue to expand, and account for over $10 billion of revenue by 2025; representing over 40% of the CPaaS market value. As a result, platforms that fail to include managed services for rich media services in their three-year plans risk missing out on the substantial growth predicted for the CPaaS market.
Resources:
View the CPaaS market research: https://www.juniperresearch.com/researchstore/operators-providers/cpaas-research-report
Download the whitepaper: https://www.juniperresearch.com/whitepapers/how-cpaas-will-evolve-in-2023
Juniper Research provides research and analytical services to the global hi-tech communications sector; providing consultancy, analyst reports and industry commentary.
Cybersecurity threats in telecoms require protection of network infrastructure and availability
Telecommunications companies have become an attractive target for attackers, as their networks can be used as a back door to other organizations, thereby making it attractive for cybercriminals to gain unauthorized access. These telecoms networks are also used to build, control and operate other critical infrastructure sectors, including energy, information technology, and transportation systems. Given the interconnected nature of telecom networks between critical infrastructure sectors, organizations need to focus on safeguarding network infrastructure and enabling network availability for critical infrastructure communication.
Telecoms face mounting threats due to various factors, such as the absence of technical knowledge, use of legacy systems, presence of sensitive information, inadequate password security, and increasing threat landscape. Operators are also transforming themselves from network infrastructure companies to cloud service companies to improve efficiencies in business operations, roll out new services and applications, and store and distribute content. As telcos are often a gateway into multiple businesses, threats can either target a specific telecom company, its third-party providers, or the subscribers of a telecom service. These attacks can come in various forms.

Trend Micro disclosed that telecoms have a larger cyber-attack surface than most enterprises, often stretching from their base station infrastructure to call centers and home workers’ laptops. The surface area provides ample opportunity for threat actors looking for customer or organizational data, trying to hijack customer accounts, or seeking to disrupt services via DDoS (distributed denial of service) and ransomware. Furthermore, supply chain providers, cloud services, IoT systems and new infrastructure needed to support 5G and network slicing create additional risk.
Industrial Cyber reached out to experts in the telecoms sector to examine the key factors that make the communications sector vulnerable to cyber attacks. They also weigh in on the unique challenges that the communications sector faces when it comes to securing and safeguarding its OT/ICS environments.
Teresa Cottam, the chief analyst at Omnisperience, told Industrial Cyber that in the past, where security was considered in telecoms the focus tended to be how it affected performance – such as minimizing DDoS traffic and attacks. “More recently, as everything has become more interconnected and the threat landscape has evolved, cyberattacks specifically against telecoms firms have increased,” she added.
Cottam pointed out that ultimately four challenges stand out – complexity, exposure, volume and variety, and cost.
On complexity, Cottam said that each individual ‘network’ actually comprises several generations of technology with some of it being decades old, and it might include fixed, mobile, and even satellite infrastructure. “Moving data from one side of the world to another requires multiple networks, each owned by a different company with a different risk profile. The move from 4G to 5G introduces even more complexity. In the 5G era, cloud, data, and IoT are combined – increasing security risks. Breaches now have a company-wide impact from production through supply chains and logistics to corporate systems,” she added.
Cottam also added that “when you consider how much equipment is in public places it’s actually surprising it’s not attacked more often. Malign actors don’t even need to mount a cyberattack, they can simply vandalise equipment to target specific regions or industries.”
Elaborating on volume and variety, Cottam said that the sheer volume of endpoints is staggering and continually increasing. “IoT has already massively increased the number of endpoints and will continue to do so. Many of these so-called smart objects aren’t very smart and are highly vulnerable. Many of the most vulnerable devices are in the home, but wherever they are, each device has the potential to inject malign traffic into the network,” she added.
On cost, Cottam said that the cost of securing a network end-to-end is significant and the reality is that telecoms firms and their customers are having to continually juggle risk versus security.
Turning the question around, Grant Lenahan, partner and principal analyst at Appledore Research, said that one of the huge transitions underway is from fundamentally private data centers and networks to outsourced or managed, secure networks that interconnect distributed enterprise to their digital partners, remote employees, public cloud, and SaaS facilities. Therefore, there is a blurring of public and private targets.
“We certainly can look at those who attack public networks because of the private data and traffic. We can also look at those who attack not an underlying enterprise target per se, but the network infrastructure itself,” Lenahan told Industrial Cyber. “These attacks, rather than going after specific data, or intended either to disrupt, for example, terrorism or to gain control that can later be used to target intellectual property the transit to the network. The very fact that public networks are public, complicates securing them.”
On the other hand, Lenahan added that there is scale and scope, allowing for concentrations of security expertise and automated protections, that might not be possible or affordable by individual enterprises. “We have spent hundreds of pages covering this seismic shift in our security research stream. Some readers might be interested in consulting it,” it added.
Andrei Elefant, CEO of EdgeHawk Security told Industrial Cyber that the key factors that make the communication sector vulnerable to cyber attacks are that the CSPs (communication service providers) face multiple and large attack surfaces. They also have a limited security budget and have to prioritize the security measures they take compared to the cost and priorities.
He also added that security expertise in CSPs is limited. “The various types of attack scenarios, attack methods, the type of data and systems that need to be protected are huge. CSPs cannot build expertise in all the required security domains and have to prioritize focus areas. The CSPs are defined as critical infrastructure and are frequently a target of Nation State Actors, which means higher expertise and more budget on the attackers’ side.”
Elefant added that these challenges are even more noticeable when it comes to protecting the OT/ICS environment. “Attack surfaces grow exponentially with the growth in the number and variety of the endpoints. Many of the OT endpoints have limited inherent protection capabilities (due to resources limitation, legacy devices, etc.,), which means they can be a perfect attack surface to harm CSPs or penetrate their networks. In many cases, these devices are being exploited for DDoS attacks, as they are available in masses with limited protection.”
Addressing the essential components that make cybersecurity in telecoms a vital and fundamental part of protecting the telecommunications landscape, as it also serves much of/all the other critical infrastructure sectors, Cottam said that not having complete visibility of the complexity of the telecoms landscape is one of the biggest challenges. “For example, there could be vulnerabilities in equipment and devices – which is often the focus of analyst reports – but equally there can be vulnerabilities in core processes which were put in place decades ago and haven’t been updated,” she added.
Cottam identified that a typical attack occurs by a criminal convincing the telecoms firm they are the customer and want to move to a new provider. “The telecoms firm – often with only minimal checking – provides the ‘customer’ with the means to do so. In the UK the system is designed to make it as easy as possible for the customer to do this, which also makes it easy for criminals. Such an attack against employees is bad; now consider it targeted at IoT devices. This is a great example of how cybersecurity often focuses on securing equipment (endpoints) but ignores vulnerable processes,” she added.
“Many countries have acted to secure number portability and in this respect, the UK is particularly vulnerable as its current system is so old-fashioned and inefficient,” according to Cottam. “Another problem this causes for IIOT is that the UK system also struggles to port large volumes of numbers such as would need to happen with a large corporate or IoT customer. This has the potential of decreasing competition in the connectivity part of the market since it’s a blocker to switching operators.”
Lenahan said that he doesn’t “believe we need to emphasize how important telecom infrastructure is. Not only is it critical infrastructure and it’s all right, but it is often the control plane for other infrastructure such as water, gas, electricity, emergency services, and many other essential components of both private public, and industrial life. It is, what’s on call, a target rich environment. That said, let’s look at what success looks like,” he added.
Elefant said that the CSPs are becoming a part of the critical infrastructures in any state. “National defense strongly relies on communication availability on the state level, in addition to the fact that these networks provide essential communication infrastructure to many other critical infrastructure facilities,” he added.
The essential components needed to keep CSPs networks available and reliable focus on two main aspects, according to Elefant. “Protecting the network infrastructure from unauthorized access and malicious attacks. This includes implementing firewalls, intrusion detection and prevention systems, and other security measures to prevent unauthorized access.”
He also pointed to protecting network availability for critical infrastructure communication by identifying and blocking attempts to saturate the network and accessibility to specific applications/devices using DDoS attacks.
The telecoms industry has had to reconsider its cybersecurity protocols in light of the digitization and incorporation of Industrial Internet of Things (IIoT) technologies. The executives looked into the main threats posed by increased connectivity techniques and how this shift affects the cybersecurity posture of these communication companies.
Cottam said that often today’s IIoT devices use the same networks as other systems, which presents a double-edged risk. “If a criminal can compromise an IIoT device they could use this as an access point to corporate systems; if they compromise corporate systems or user devices they can hijack IIoT devices. Again, this speaks to the interconnectedness of networks and often the poor understanding of how criminals can utilise connections and access points to compromise industrial customers.”
“The main concerns from customers include exposure of their data, compromised network equipment, attacks on devices and network signaling, as well as creating a gateway for further attacks. Network segmentation is a useful technique to limit the scope of such attacks,” according to Cottam. “Reliable security frameworks are built into 3GPP standards to ensure 4G and 5G cellular connections are secure. But as we move to 5G a range of new exciting techniques are also delivered.”
Another technique is to utilize private networks – effectively campus networks within a factory or industrial complex with limited connections to the public network but complex connections within the private network, Cottam said. “Connectivity is only provided to authorised devices (more secure than WiFi, as it can be based on SIM authentication) and data is processed on-site,” she added.
“The simplest way to look at this is that complexity is increasing dramatically in enterprise networks. There will be an order of magnitude more endpoints; applications and data will reside in various clouds; and dynamically changing ecosystems of digital trading partners will continuously evolve,” Lenahan said. “This implies a complex network that crosses ownership boundaries, and is constantly changing.”
Lenahan noted that the only apparent constant throughout this ‘web’ is the telecom CSP that undertakes end-to-end connectivity, orchestration, and in our view, security. “This is a huge opportunity for our industry. However, it also means we need to think completely differently about security. It cannot be a separate island; it must be integrated into network automation. Furthermore, it must be automated, something tacos in security professionals have long been uncomfortable with,” he added.
Elefant identified some of the threats brought by these increased connectivity techniques, including increased attack surface, unsecured devices, protocol vulnerabilities, and DDoS attacks. With “the exponential increase in the number of connected devices, the attack surface of the network has increased, creating more opportunities for malicious actors to gain unauthorized access to the network. Many IoT devices are not designed with security in mind, and may have weak passwords, unpatched vulnerabilities, or lack encryption, making them easy targets for attackers.”
He also pointed out that IoT devices often use proprietary protocols, which may have vulnerabilities that are not well understood and are difficult to patch. IoT devices can be easily compromised and used to launch DDoS attacks, overwhelming the network with traffic and causing availability issues.
Elefant highlighted that the new threats have led to a shift in the cybersecurity posture of CSPs. “Implementing more strict network segmentation, both on their infrastructure and also as a service to their customers. Specifically for the IIoT environment, access control services, delivered by the CSPs, are being applied on a larger scale. Protecting the network from DDoS attacks on the edge and access points became a mandatory consideration. Additionally, there is a need to continuously monitor and assess the security of the network edge and access as more attacks may come from exploited devices connected to the network.”
Like other critical infrastructure sectors, the communications sector has also faced mounting cybersecurity rules and regulations in recent times. The executives address how the communication sector responded to the increase in cybersecurity regulations for critical infrastructure owners and operators, as well as analyze the impact these initiatives have had in enhancing reporting procedures and improving the cybersecurity posture of the telecoms sector.
Cottam said that one of the biggest challenges stems from the ‘democratisation’ of IoT. “As it becomes the norm in manufacturing supply chains, smaller and newer industrial firms are drawn in or adopt IoT to increase their efficiency. These firms often don’t fully understand the importance or complexity of securing their IoT devices and lack the budget and expertise in-house,” she added.
Another challenge is that many enterprises deploy and secure IoT from an IT perspective, according to Cottam. “Traditional IT security largely focuses on end-point and perimeter security. But with hundreds of thousands of IoT endpoints and more permeable boundaries, the emphasis has to shift to securing and managing the network rather than trying to put security into every device – not all of which are designed to be secured,” she added.
“Likewise, while cellular IoT is reasonably secure – and that based on 5G even more so – it is not unhackable. IoT network security isn’t just about securing the network either, it’s about network-based security that can monitor all the connected objects, processes, and applications,” Cottam said. “Neither is it just about hackers anymore. Nation states, protestors, and terrorists are just as likely to want to attack critical infrastructure and their objectives are different and their budgets and expertise are huge. While there has been much talk of bringing together IT/OT/IoT into a single process to make it more manageable and auditable, the risk is that the complexity and volume become overwhelming.”
Lenahan said that details on how telcos are handling critical infrastructure security are hard to get, and in my opinion, rightly so. “That said, we can see many trends in the industry to prepare telecoms to not only be more secure on its own but to be in a good position to secure infrastructure for others. Some things are as simple as the collaborative work in the MEF, on secure transport services — or the transport service in security or considered as one. Similarly, the managed services, with security at their core, that many leading telcos are offering to their enterprise clients, can be applied to protecting public and shared infrastructure as well,” he added.
“One thing we believe they must change is that these ‘managed’ services, which, by definition, are semi-custom, must become more standardized products,” according to Lenahan. “We say this because that is the only way telcos can afford to invest in the level of automation that will truly illuminate errors and omissions and stay ahead of the bad actors. It’s simply a matter of operating a process at scale and concentrating one’s fire, so to speak.”
The CSPs responded in various methods to address the increase in cybersecurity regulations for critical infrastructure, Elefant said. “Increase in network segmentation to protect critical infrastructure, the CSPs designed their networks in a way they can segment their network based on the type of service they need to deliver. Applying more protection capabilities at the edge of the network to protect the network from threats that may come from the access side, in addition to more traditional protection methods they apply on the network core,” he added.
Elefant also suggested adding more secure communication channels, like segmentation and encryption for critical elements, such as the control plane, and adding more monitoring tools to identify security risks in real time. “These initiatives help CSPs to identify security threats in real-time and apply faster response and mitigation, leveraging the new control points, mainly at the edge of the network,” he concluded.
References:
https://www.trendmicro.com/en_se/research/22/b/the-telecoms-cyber-threat-landscape-in-2021.html
Cybersecurity to be a top priority for telcos in 2023
IEEE/SCU SoE Virtual Event: May 26, 2022- Critical Cybersecurity Issues for Cellular Networks (3G/4G, 5G), IoT, and Cloud Resident Data Centers
IMT Vision – Framework and overall objectives of the future development of IMT for 2030 and beyond
This ITU-R recommendation in progress will be the main focus of next week’s ITU-R WP5D meeting #43 in Geneva. It defines the framework and overall objectives for the development of International Mobile Telecommunications (IMT) for 2030 and beyond. There are contributions related to this recommendation from: Apple, Nokia, Ericsson, Wireless World Research Forum, Motorola Mobility, Orange, United Kingdom of Great Britain and Northern Ireland, Finland, Germany, GSOA, China, Qualcomm, Electronics and Telecommunications Research Institute (ETRI), Brazil, Samsung, ZTE, Huawei, InterDigital, Intel and India, with several being multi-company contributions.
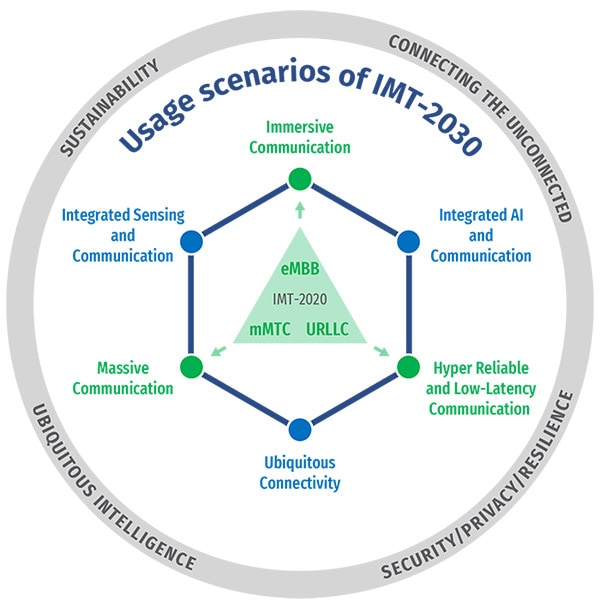
The objective is to reach a consensus on the global vision for IMT-2030 (aka 6G), including identifying the potential user application trends and emerging technology trends, defining enhanced and brand-new usage scenarios and corresponding capabilities, as well as understanding the new spectrum needs.
IMT will continue to better serve the needs of the networked society, for both developed and developing countries in the future and this Recommendation outlines how that will be accomplished. This Recommendation also intends to drive the industries and administrations for encouraging further development of IMT for 2030 and beyond.
The framework of the development of IMT for 2030 and beyond, including a broad variety of capabilities associated with envisaged usage scenarios, is described in detail in this Recommendation.
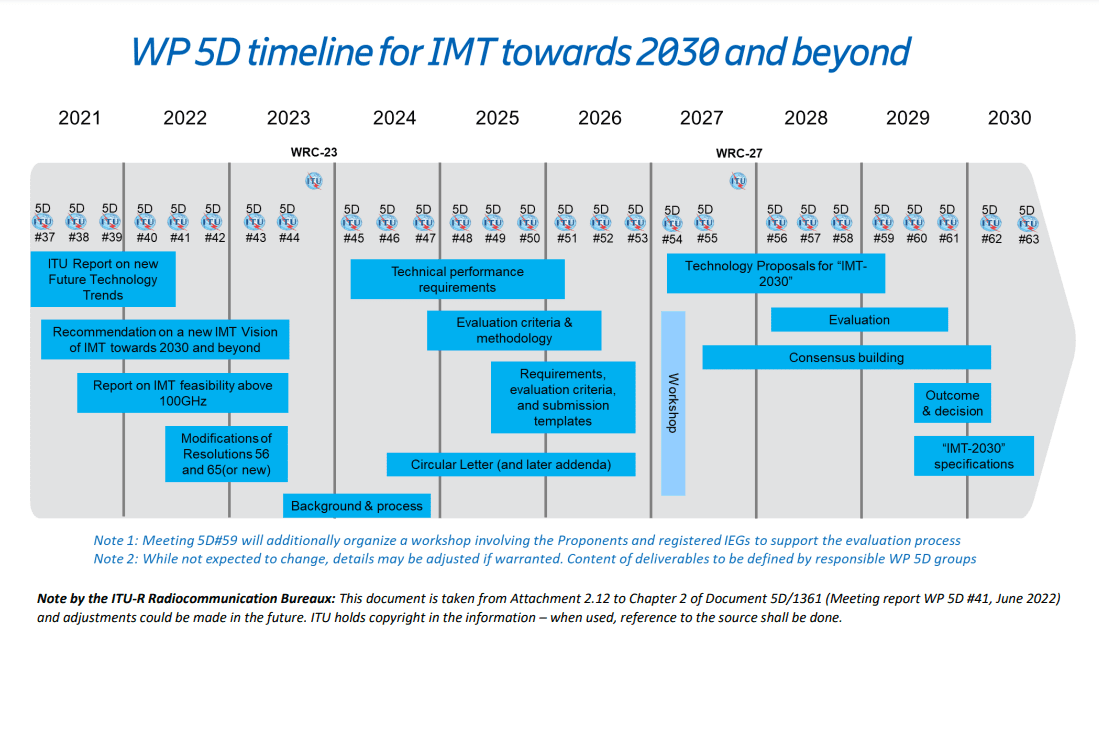
In June 2022, ITU-R decided on the overall timeline for 6G with three major stages:
- Stage 1 – vision definition to be completed in June 2023 before the World Radiocommunication Conference 2023 (WRC-23),
- Stage 2 – requirements and evaluation methodology to be completed in 2026, and
- Stage 3 – specifications to be completed in 2030. The 3-stage timeline and the tasks for each stage are summarized in Figure below.
This draft Recommendation defines a [potential] framework and overall objectives for the development of the terrestrial component of International Mobile Telecommunications (IMT) for 2030 and beyond. IMT will continue to better serve the needs of the [networked] society, for both developed and developing countries in the future and this [Recommendation/document] outlines how [possibly] that could be accomplished. This [Recommendation/document] also intends to encourage further development of IMT-2030. In this [Recommendation/document], the [potential] framework of the development of IMT-2030, including a broad variety of capabilities associated with [some possible] envisaged usage scenarios[, and those yet to be developed and] described in detail. Furthermore, this [Recommendation/document] addresses the objectives for the development of IMT-2030, which includes further enhancement and evolution of existing IMT and the development of IMT-2030.
It should be noted that this Recommendation is defined considering the development of IMT to date based on Recommendation ITU-R M.2083 (approved in September 2015).
Technology Trends:
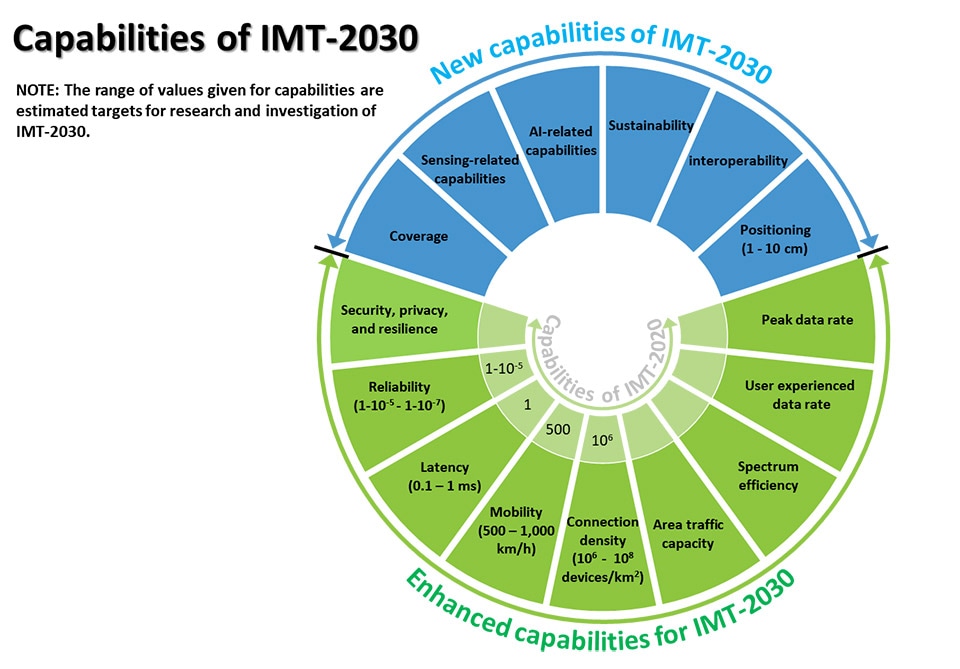
Report ITU-R M.2516 provides a broad view of future technical aspects of terrestrial IMT systems considering the timeframe up to 2030 and beyond, characterized with respect to key emerging services, applications trends, and relevant driving factors. It comprises a toolbox of technological enablers for terrestrial IMT systems, including the evolution of IMT through advances in technology, and their deployment. In the following sections a brief overview of emerging technology trends, technologies to enhance the radio interface, and technologies to enhance the radio network are presented.
An important breakthrough in 3GPP Rel-17, Technical Specifications for Non-Terrestrial Networks (NTN) were established & defined for satellite direct access to device for both 5G and IoT services. This development reflects a trend that satellite & space technologies can offer many benefits for development & operation of future IMT-2030 networks, to enable 5G & 6G available everywhere, accessible to enterprises and citizens across the globe.
IMT-2030 will consider an AI-native new air interface that refers to the use of AI to enhance radio interface performance such as symbol detection/decoding, channel estimation etc. An AI-native radio network will enable automated and intelligent networking services such as intelligent data perception, supply of on-demand capability etc. Radio network to support AI services is the design of IMT technologies to serve various AI applications, and the proposed directions include on-demand uplink/sidelink-centric, deep edge and distributed machine learning. The integration of sensing and communication functions in future wireless systems will provide beyond-communication capabilities by utilizing wireless communication systems more effectively resulting in mutual benefit to both functions. Integrated sensing and communication (ISAC) systems will also enable innovative services and applications such as intelligent transportation, gesture and sign language recognition, automatic security, healthcare, air quality monitoring, and solutions with higher degree of accuracy. Combined with technologies such as AI, network cooperation and multi-nodes cooperative sensing, the ISAC system will lead to benefits in enhanced mutual performance, overall cost, size and power consumption of the whole system.
Computing services and data services are expected to become an integral component of the future IMT system. Emerging technology trends include processing data at the network edge close to the data source for real-time response, low data transport costs, energy efficiency and privacy protection, as well as scaling out device computing capability for advanced application computing workloads.
Device-to-device (D2D) wireless communication with extremely high throughput, ultra-accuracy positioning and low latency will be an important communication paradigm for the future IMT. Technologies such as THz technology, ultra-accuracy sidelink positioning and enhance terminal power reduction technology can be considered to satisfy requirements of new applications.
Energy efficiency and low power consumption comprises both the user device and the network’s perspectives. The promising technologies include energy harvesting, backscattering communications, on-demand access technologies, etc.
To achieve real-time communications with extremely low latency communications, two essential technology components are considered: accurate time and frequency information shared in the network and fine-grained and proactive just-in-time radio access.
There is a need to ensure security, privacy, and resilient solutions allowing for the legitimate exchange of sensitive information through network entities. Potential technologies to enhance trustworthiness include those for RAN privacy, such as distributed ledger technologies, differential privacy and federated learning, quantum technology with respect to the RAN and physical-layer security technologies.
UPDATE: https://techblog.comsoc.org/2023/07/09/draft-new-itu-r-recommendation-not-yet-approved-m-imt-framework-for-2030-and-beyond/
References:
Summary of ITU-R Workshop on “IMT for 2030 and beyond” (aka “6G”)
https://www.itu.int/en/ITU-R/study-groups/rsg5/rwp5d/Pages/wsp-imt-vision-2030-and-beyond.aspx
Excerpts of ITU-R preliminary draft new Report: FUTURE TECHNOLOGY TRENDS OF TERRESTRIAL IMT SYSTEMS TOWARDS 2030 AND BEYOND
Development of “IMT Vision for 2030 and beyond” from ITU-R WP 5D
ITU-R: Future Technology Trends for the evolution of IMT towards 2030 and beyond (including 6G)
China’s MIIT to prioritize 6G project, accelerate 5G and gigabit optical network deployments in 2023
ITU-R WP5D: Studies on technical feasibility of IMT in bands above 100 GHz
https://www.itu.int/rec/R-REC-M.2083 (Sept 2015)
Canalys: Cloud marketplace sales to be > $45 billion by 2025
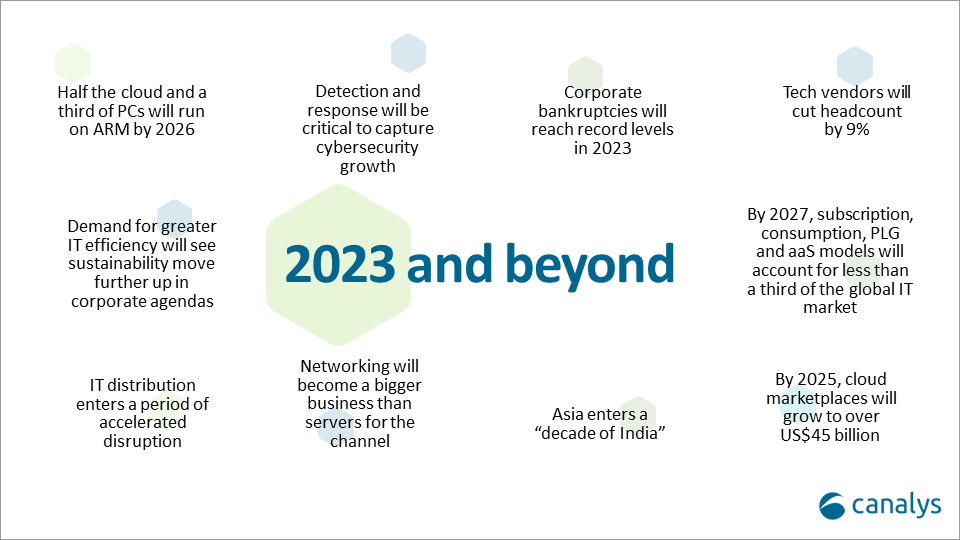
Canalys now expects that by 2025, cloud marketplaces will grow to more than $45 billion, representing an 84% CAGR. That was one of the market research firm’s predictions for 2023 and beyond (see chart below).
Cloud marketplaces [1.] are accelerating as a route to market for technology, led by hyperscale cloud vendors such as Alibaba, Amazon Web Services, Microsoft, Google and Salesforce, which are pouring billions of development dollars into the sector.
Note 1. A cloud marketplace is an online storefront operated by a cloud service provider. A cloud marketplace provides customers with access to software applications and services that are built on, integrate with or complement the cloud service provider’s offerings. A marketplace typically provides customers with native cloud applications and approved apps created by third-party developers. Applications from third-party developers not only help the cloud provider fill niche gaps in its portfolio and meet the needs of more customers, but they also provide the customer with peace of mind by knowing that all purchases from the vendor’s marketplace will integrate with each other smoothly.
…………………………………………………………………………………………………………………………………………………………………….
“The marketplace route to market is on fire and cannot be ignored by any channel leader,” said Canalys Chief Analyst, Jay McBain. “Marketplaces grew more in the first three months of the pandemic than in the previous decade and have just kept growing,” he added.
“We under-called it,” explained Steven Kiernan, vice president at Canalys. “Cloud marketplaces are accelerating at such a dizzying speed that we’ve doubled our pre-pandemic forecast.
Some software vendors that are active on marketplaces, in particular cybersecurity vendors, are publicly reporting as much as 600% year-on-year growth via this channel, according to McBain.
In addition, the hyperscalers are now reporting growing numbers of billion-dollar customer commitments through enterprise cloud consumption credits, which cover more than just software.
The large cloud marketplaces have lowered fees from upwards of 20% down to 3%, enabling vendors to fund multi-partner offers inside the transaction.
Private equity is funding billions more into marketplace development firms such as AppDirect, Mirakl, Vendasta and CloudBlue to enable hundreds of niche marketplaces across different buyers, industries, geographies, customer segments, product areas and business models.

Canalys Chief Analyst, Alastair Edwards:
“The rise of this route to market represents a threat to both resellers and two-tier distribution. But as more complex technologies are consumed via marketplaces, end customers are also turning to trusted partners to help them discover, procure and manage marketplace purchases. The hyperscalers are increasingly recognizing the value of channel partners, allowing them to create customized vendor offers for end-customers, and supporting the flow of channel margins through their marketplaces. Hyperscalers’ cloud marketplaces are becoming a growing force in global IT distribution as a result.”
By 2025, Canalys conservatively forecasts that almost a third of marketplace procurement will be done via channel partners on behalf of their end customers.
Canalys key predictions for 2023 and beyond:
About Canalys:
Canalys is an independent analyst company that strives to guide clients on the future of the technology industry and to think beyond the business models of the past. We deliver smart market insights to IT, channel and service provider professionals around the world. We stake our reputation on the quality of our data, our innovative use of technology and our high level of customer service.
References:
https://canalys.com/newsroom/cloud-marketplace-forecast-2023
https://www.canalys.com/resources/Canalys-outlook-2023-predictions-for-the-technology-industry
https://www.techtarget.com/searchitchannel/definition/cloud-marketplace
Canalys: Global cloud services spending +33% in Q2 2022 to $62.3B
AWS, Microsoft Azure, Google Cloud account for 62% – 66% of cloud spending in 1Q-2022
IDC: Cloud Infrastructure Spending +13.5% YoY in 4Q-2021 to $21.1 billion; Forecast CAGR of 12.6% from 2021-2026
Synergy Research: Growth in Hyperscale and Enterprise IT Infrastructure Spending; Telcos Remain in the Doldrums
Hyperscale cloud companies are spending more and more money on Capex IT infrastructure compared with the largest telecommunication companies as overall IT infrastructure spending in 2022 reached $700 billion. In 2022, hyperscale operators spent roughly $200 billion on Capex IT infrastructure such as network switches and data center hardware and software, representing a 9 percent increase annually and led by Amazon, Google and Microsoft, according to new data from IT market research firm Synergy Research Group.
Comparatively, telecom spending on IT infrastructure by companies like Verizon, AT&T and China Mobile dropped 4 percent in 2022 to approximately $290 billion, Synergy Research Group reported.
Hyperscale operator share of total spending has continued to rise steadily over the last few years, as continued growth in cloud and other digital services drive ever-higher spending levels. Telco spending remains heavily crimped by lack of meaningful growth in their revenue streams. Enterprise spending has also bounced back in the last two years after a soft spell in 2019 and 2020. The main drivers in the enterprise have been the continued long-term growth of hosted and cloud collaboration solutions, increased spending on network security, and a post-pandemic bounce back for both enterprise data centers and switches. In some segments, higher ASPs have also contributed, as cost increases due to supply chain issues are passed on to the customers of tech vendors.
Telcos remain locked in a low-to-no-growth world and their Capex reflects that. For hyperscale operators, the boom in cloud services and continued growth in other digital services is driving ongoing growth in spending. Telecom companies’ share of Capex IT infrastructure spending was 42 percent in 2022, down from 58 percent share in 2016. The largest telco spenders on technology infrastructure last year were China Mobile, Deutsche Telekom, Verizon, AT&T, NTT and China Telecom.
In 2022, hyperscale operators accounted for 29 percent share of the total Capex infrastructure spending market, up significantly from 13 percent share in 2016. Some of the biggest spenders in 2022 were Amazon, Apple, Google, Microsoft and Alibaba.
Overall spending by both fixed and mobile telco operators has been relatively flat over the past eight years, with annual spending levels for infrastructure hovering around $290 billion each year. Synergy market data covers total capital expenditure for telco and hyperscale operators mostly around networking and data center hardware and software.
The final market segment covered in Synergy’s new data is enterprise spending on IT infrastructure, which grew 9 percent year over year in 2022 to roughly $210 billion. The enterprise spend accounted for 29 percent of the total Capex infrastructure market in 2022.
“Enterprise spending has also bounced back a bit in the last two years after a soft spell in 2019 and 2020,” said Dinsdale. ince 2016, enterprise IT spending has grown by an average of over 6 percent annually. Synergy said to make the market data numbers more comparable, enterprise spending covers data center hardware and software, networking and collaboration tools. It excludes enterprise spending on communication and IT services, devices and business software.
“There has also been something of a post-pandemic bounce back for both enterprise data centers and switches, the former being helped by higher costs due to supply chain issues that are being passed on in the form of higher ASPs [average selling price],” said Dinsdale. “For equipment and software vendors, the good news is that overall IT infrastructure spending will continue to grow steadily over the next five years,” he added.
…………………………………………………………………………………………………………………………………………………………………………………………………..
About Synergy Research Group:
Synergy provides quarterly market tracking and segmentation data on IT and Cloud related markets, including vendor revenues by segment and by region. Market shares and forecasts are provided via Synergy’s uniquely designed online database SIA ™, which enables easy access to complex data sets. Synergy’s Competitive Matrix ™ and CustomView ™ take this research capability one step further, enabling our clients to receive on-going quantitative market research that matches their internal, executive view of the market segments they compete in.
Synergy Research Group helps marketing and strategic decision makers around the world via its syndicated market research programs and custom consulting projects. For nearly two decades, Synergy has been a trusted source for quantitative research and market intelligence.
To speak to an analyst or to find out how to receive a copy of a Synergy report, please contact [email protected] or 775-852-3330 extension 101.
…………………………………………………………………………………………………………………………………………………………………………………………………..
References:
https://www.crn.com/news/cloud/cloud-provider-spend-on-it-capex-climbs-as-telecom-falls
Synergy Research: public cloud service and infrastructure market hit $126B in 1Q-2022
Synergy Research: Microsoft and Amazon (AWS) Dominate IT Vendor Revenue & Growth; Popularity of Multi-cloud in 2021
Synergy Research: Hyperscale Operator Capex at New Record in Q3-2020
Synergy Research: Strong demand for Colocation with Equinix, Digital Realty and NTT top providers
AT&T Highlights: 5G mid-band spectrum, AT&T Fiber, Gigapower joint venture with BlackRock/disaggregation traffic milestone
On AT&T’s earnings call this week, CEO John Stankey provided these highlights:
- AT&T network teams have also consistently outpaced our mid-band 5G spectrum rollout objective. In fact, we now reach 150 million mid-band 5G POPs, more than double our initial 2022 year-end target. Our goal remains to deploy our spectrum efficiently and in a manner that supports traffic growth. In the markets where we have broadly deployed mid-band 5G, 25% of our traffic in these areas already takes advantage of our mid-band spectrum.
- We also expect to continue our 5G expansion, reaching more than 200 million people with mid-band 5G by the end of 2023.
- AT&T had more than 1.2 million AT&T Fiber net adds last year. The fifth straight year we’ve totaled more than 1 million AT&T Fiber net adds. And after 2.9 million AT&T Fiber net adds over the last 2.5 years, we’ve now reached an inflection point where our fiber subscribers outnumber are non-fiber DSL subscribers. The financial benefits of our fiber focus are also becoming increasingly apparent as full year fiber revenue growth of nearly 29% has led to sustainable revenue and profit growth in our Consumer Wireline business. As we scale our fiber footprint, we also expect to drive margin expansion.
- AT&T has the nation’s largest and fastest-growing fiber Internet, and we expect continued healthy subscriber growth as we grow our fiber footprint. As we keep expanding our subscriber base will drive efficiencies in everything we do. AT&T considers fiber a multiyear opportunity that will transform the way consumers’ and businesses’ growing connectivity needs are met in the ensuing decade and beyond.
- AT&T Fiber will be passing 30 million-plus consumer and business locations within our existing wireline footprint by the end of 2025. We finished last year with approximately 24 million fiber locations passed, including businesses, of which more than 22 million locations are sellable, which we define as our ability to serve. We remain on track to reach our target of 30 million plus passed locations by the end of 2025. The simple math would suggest 2 million to 2.5 million consumer and business locations passed annually moving forward. As we previously shared, build targets will vary quarter-to-quarter in any given year based on how the market is evolving.
- AT&T’s Gigapower joint venture announcement with a BlackRock infrastructure fund has not yet closed, we’re very excited about the expected benefit. Through this endeavor, Gigapower plans to use a best-in-class operating team to deploy fiber to an initial 1.5 million locations, and I would expect that number to grow over time. This innovative risk-sharing collaboration will allow us to prove out the viability of a different investment thesis that expanding our fiber reach not only benefits our fiber business, but also our mobile penetration rates. But what makes me most enthusiastic about this endeavor is that we believe Gigapower provides us long-term financial flexibility and strategic optionality and what we believe is the definitive access technology for decades to come, all while sustaining near-term financial and shareholder commitments.
- AT&T sees huge opportunities to connect people who previously did not have access to best-in-class technologies through broadband stimulus and Broadband Equity, Access, and Deployment (BEAD) funding. As I shared before, we truly believe that connectivity is a bridge to possibility in helping close the digital divide by focusing on access to affordable high-speed Internet is a top priority of AT&T. The intent of these government programs is to provide the necessary funding and support to allow both AT&T and the broader service provider community that means to invest alongside the government at the levels needed to achieve the end state of a better connected America.
- Our commitment to fiber is at the core of our strategy. In footprint, we’re on track to deliver our 30 million plus location commitment and we’re building the strategic and financial capabilities to take advantage of further opportunities as they emerge.
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………..
…………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………..
AT&T’s open disaggregated core routing platform was carrying 52% of the network operators traffic at the end of 2022, according to Mike Satterlee, VP of AT&T’s Network Core Infrastructure Services in an interview with SDxCentral. Satterlee described this platform as the carrier’s “common” or “core backbone,” which supports about 594 petabytes of data traffic per day. This core backbone is a multi-part architecture spanning from AT&T’s nationwide network switch and cloud provider connections to its consumer- and enterprise-facing broadband and mobility services.
AT&T’s core platform uses Broadcom’s Jericho2 hardware design and Ramon switching chips, the carrier’s distributed disaggregated chassis (DCC) white box router architecture, and Israel based DriveNets Network Cloud (DNOS) software. It’s fed by AT&T’s edge router platform that sits in regional connection points. It uses the Broadcom silicon, Cisco software platform, and hardware from UfiSpace.
Satterlee said AT&T is running a nearly identical architecture in its core and edge environments, though the edge system runs Cisco’s disaggregates software. Cisco and DriveNets have been active parts of AT&T’s disaggregation process, though DriveNets’ earlier push provided it with more maturity compared to Cisco.
“DriveNets really came in as a disruptor in the space,” Satterlee said. “They don’t sell hardware platforms. They are a software-based company and they were really the first to do this right.”
AT&T began running some of its network backbone on DriveNets core routing software beginning in September 2020. The vendor at that time said it expected to be supporting all of AT&T’s traffic through its system by the end of 2022.
“It’s completely open in the sense that either vendor software could run in either places of the network,” Satterlee explained, adding that this was very helpful during the COVID-19 pandemic. “By having a common platform it’s just a matter of switching out the [network operating system] so we were able to very quickly redirect equipment for different use cases within AT&T and it was just a simple software change controlled by SDN.”
AT&T is targeting 65% of its traffic running on the disaggregated architecture by the end of this year. This will be important to support AT&T’s fiber and 5G push, which was enhanced late last year through a deal the carrier struck with BlackRock to expand its fiber footprint.
John Gibbons, assistant VP for AT&T’s Network Infrastructure Services, added that this also paves the way for the carrier to roll out 800-gigabit support for its backbone. “We don’t have to swap out the core router to get to 800-gig,” Gibbons said. “We can actually add to the current chassis. … We can add the new box to start growing it out from there. That’s the flexibility. It’s like the building-block model.
“Pretty much everything we spoke about supports our two biggest initiatives, which is growing the AT&T fiber broadband as well as 5G, and it’s all the underpinnings of those services,” Gibbons said.
References:
AT&T and BlackRock’s Gigapower fiber JV may alter the U.S. broadband landscape
AT&T Deploys Dis-Aggregated Core Router White Box with DriveNets Network Cloud software
Dell’Oro: Optical Transport market to hit $17B by 2027; Lumen Technologies 400G wavelength market
According to a recent forecast report by Dell’Oro Group, the Optical Transport equipment demand is forecast to increase at a 3 percent compounded annual growth rate (CAGR) for the next five years, reaching $17 billion by 2027. The cumulative revenue during that five year period is expected to be $81 billion.
“We expect annual growth rates to fluctuate in the near term before stabilizing to a more typical 3 percent growth rate,” said Jimmy Yu, Vice President at Dell’Oro Group. “There is still a large amount of market uncertainty this year due to the economic backdrop—economists are predicting a high chance of a recession in North America and Europe. However, at the same time, most optical systems equipment manufacturers are reporting record levels of order backlog entering the year, and we expect that most of this backlog could convert to revenue when component supply improves this year,” added Yu.
Additional highlights from the Optical Transport 5-Year January 2023 Forecast Report:
- Optical Transport market expected to increase in 2023 due to improving component supply.
- WDM Metro market growth rates in next five years are projected to be lower than historic averages due to the growing use of IP-over-DWDM.
- DWDM Long Haul market is forecast to grow at a five-year CAGR of 5 percent.
- Coherent wavelength shipments on WDM systems forecast to grow at 11 percent CAGR, reaching 1.2 million annual shipments by 2027.
- Installation of 400 Gbps wavelengths expected to dominate for most of forecast period.
About the Report
The Dell’Oro Group Optical Transport 5-Year Forecast Report offers a complete overview of the Optical Transport industry with tables covering manufacturers’ revenue, average selling prices, unit shipments, wavelength shipments (by speed up to 1.2+ Tbps). The report tracks DWDM long haul, WDM metro, multiservice multiplexers, optical switch, Disaggregated WDM, DCI, and ZR Optics.
……………………………………………………………………………………………………………………………………………………
Separately, Lumen Technologies is expanding its 400G wavelength network across North America. Lumen said it has now deployed the network in 70 markets. More than 240 data centers have access to Lumen’s 400G Wavelength Services, and the network has over 800 Tbit/s of capacity.
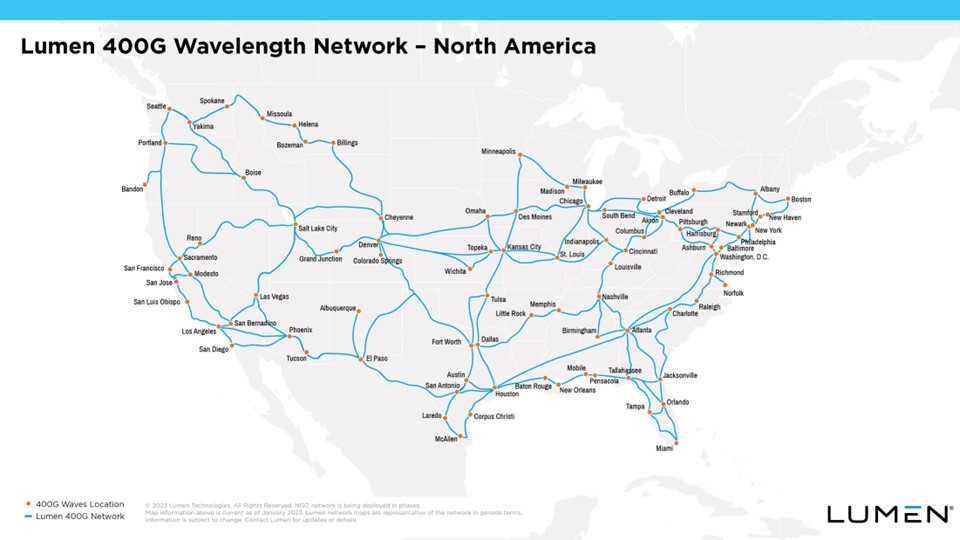
Lumen said it plans to continue its intercity 400G expansion this year, pushing the network “deeper into the metro edge.” The company noted that wavelength services will assist customers in moving workloads to the cloud, and provide private, dedicated connections.
Enterprise customers can also examine network options, plan out their wavelengths and get cost estimates with Lumen’s Topology Viewer.
References:
https://www.prnewswire.com/news-releases/lumen-kicks-up-its-400g-offering-across-the-us-301730126.html