SASE
New Findings in Aryaka’s 2022 State of the WAN Report: Cloud Adoption, Hybrid Workplaces, Convergence of Network and Security with SASE
Overview:
Aryaka®, a leader in fully managed Cloud-First WAN solutions, today published its 2022 State of the WAN Report, offering a compendium of insights into global SD-WAN and SASE planning. 1,600 information technology (IT) enterprise decision makers across global enterprises answered the survey, the largest response to the survey since its inception.
Key trends identified in this year’s report include:
- A quarter of the respondents state they have closed 25-50% of their office sites, dovetailing into overall hybrid work initiatives where 75% state that at least a quarter of their employees will remain remote permanently post-pandemic.
- Accelerating digital transformation initiatives also impact legacy data centers, with 51% planning to eliminate their use within the next 24 months as they move to the cloud.
- The surveyed group says Microsoft Teams (58%) and Office 365 (55%) are among the most widely adopted SaaS applications, followed by Zoom and Google Docs (35%).
- A quarter of respondents expect budgets to grow by 25% or more in the next year, with a full three-quarters projecting at least a 10% growth. Investment appears to be accompanied via cost savings.
- A move to simplify, adopting a more cloud-centric and agile approach, is driving convergence. In the context of network and security, trends include the Secure Access Service Edge (SASE), with 64% deploying or planning to deploy over the next year. Over two-thirds will opt for a managed SASE to help address complexity and costs, but challenges include complexity at 40%, a single or dual-vendor approach at 39%, and developing a phased migration strategy at 33%. Observability and control should help with deployments, identified by over two-thirds as a top imperative.
- 29% state that they are already deploying what they consider to be a SASE architecture, with another 56% planning to deploy in the next 12-24 months.
- What capabilities do the respondence require? The top responses are SD-WAN at 34%, a Cloud Secure Web Gateway (SWG) at 30%, and Firewall as a Service (FWaaS) at 17%.
“This year’s Aryaka State of the WAN includes many valuable insights backing up trends we see in the industry. These include the effects of hybrid work, with 75% projecting a quarter of their employees to remain at least part-time remote, and cloud connectivity demands skyrocketing with 51% planning to move away from traditional data centers over the next two years. Both initiatives will require more sophisticated network-as-a-service (NaaS) solutions with integrated security offerings,” said Scott Raynovich founder and chief analyst of Futuriom.
“The sixth edition of the Global State of the WAN (SOTW) is one of the largest such surveys in the world,” said Shashi Kiran, CMO of Aryaka. “It packages an enormous number of insights from decisions makers from all over the world, drawn from CIOs, CISOs as well as network, security and cloud practitioners. The 2022 edition reveals new enterprise trends on workplaces, cloud adoption, convergence and several other areas putting a spotlight on the impact of the Covid-19 pandemic in the process. We hope this resource serves as a handy companion for enterprise architects engaged in planning their WAN, security and cloud infrastructure for years ahead.”
SD-WAN vendors have long touted the technology’s application- and policy-based routing capabilities as the antidote to network performance and complexity. However, customers are increasingly looking for ways to offload that complexity and consolidate services under a single roof. “There’s a fragmented value chain for SD-WAN, which we’ve seen before and now for SASE as well,” Kiran said.
Of those surveyed, 45% said they were considering a consolidated SASE architecture, up from 39% last year. However, enterprises’ desire for managed services doesn’t stop at SD-WAN or SASE. Respondents expressed a desire for managed last-mile and multi-cloud connectivity. “There is inherent complexity in all of these areas and having something that is managed and delivered as a service appears to be important,” Kiran said.
Year-on-Year Trends and Shifting Priorities:
In Aryaka’s 2021 State of the WAN Report, 21% indicated that half of their workforce would be working remote post-pandemic. This year that number increased by 11%, with 32% reporting that at least half of their workforce would be permanently remote.
Collaboration and Productivity suites have gained traction. The Microsoft suite has gained momentum, with Teams identified by respondents as the most deployed application, growing its footprint by over half, from 34% in 2021 to 58% this year. Conversely, Google Docs dropped from 41% last year to 35% today with Microsoft 365 now at 55%.
For China, basic connectivity concerns dropped noticeably from the last report, at 45% in 2021 to 30% today. In contrast, compliance and regulatory issues are now in the lead at 50%.
A renewed interest in ROI was reflected in this year’s report, with 36% of those responding having cost concerns, an increase of 16% compared to last year. Though budgets are expected to increase by 25%, both for networking and security, the focus on ROI implies that these increases must be spent judiciously.
IT professionals were less concerned vs previous years about the newness of the technology (28% vs 31% in 2021), and whether applications will perform properly (29% vs 36% in 2021), speaking to a greater confidence in application support. As change management takes priority, there is an increased focus on observability and control, increasing by 9% (69% vs 60% last year).
Aryaka 6th Annual State of the WAN 2022 – Four Themes:
1. Acceleration of Remote and Hybrid Work: The report looks at challenges in supporting the hybrid workforce, hybrid work trends, and investments planned to support this new environment. 75% state that at least a quarter of their employees will remain hybrid post-pandemic, aligned with the closure of physical facilities, with a quarter stating they have closed 25-50% of their office sites. Effectively managing worker movement between on-premises and remote requires dynamic bandwidth reallocation, identified by 61% as very important.
2. Application Performance and Consumption: In addition, the report dives into the diversity of applications in use and resulting challenges, how enterprises plan to address these, and potential concerns. As noted earlier, collaboration and productivity applications like Microsoft Teams and Office 365 experienced some of the strongest growth, but there was an overall uptick in SaaS application adoption including Zoom (35%), Salesforce (28%), and SAP/HANA (25%). Performance still must improve, with 42% identifying slow performance for remote and mobile users a key issue, followed by 37% calling out slow performance at the branch.
3. Managing Complexity and Managed Services Adoption: The report addresses what managed services enterprises expect, including SD-WAN and SASE implementation plans and budgets, as well as perceived barriers to adoption. This section also looks at MPLS migration. In evaluating managed services, enterprises continue to demand more from their providers, and are looking for a wider set of offers, an all-in-one SD-WAN and SASE that includes the WAN (45%), security (67%), application optimization (40%), last mile management (29%), and multi-cloud connectivity (27%). The movement to SD-WAN and SASE also follows the movement away from MPLS, with 46% planning to terminate some or all contracts over the next year. Enterprises are generally bullish on their budgets, with a quarter expecting it to grow by 25% or more, and a total of three quarters expecting at least 10% growth.
4. Networking and Security Convergence Including a SASE Architecture: SASE represents a promise of a converged Cloud-First architecture, but there are concerns on complexity and adoption. 42% state that lackluster application performance is a time sink, and 34% consider security to be a major priority. This path to SASE adoption includes setting a strategy (35%), phasing out of legacy VPNs (32%), as well as consolidating cloud security with zero-trust (29%).
Top desired capabilities include a SWG (47%), SD-WAN (36%), and FWaaS (28%). Implementation concerns identified earlier are balanced by expected advantages that include time and cost reduction (37%), as well as agility (33%), while decision-making is still mostly distributed across networking and security, 41% state it is now consolidated. Finally, over two-thirds plan to consume SASE as a managed offer.
What are the biggest challenges you’re facing with your WAN?
Total Responses 1,386
- High complexity/difficult to manage or maintain 37%
- Slow access to cloud services & SaaS applications 33%
- Slow performance of on-premises applications 32%
- Long deployment times to bring up new sites 29%
- Lack of adequate security 28%
- Poor voice or video quality 23%
- High cost 20%
- Lack of visibility 20%
*Respondents chose maximum three responses
–>The WAN continues to be a challenge, impacting manageability, performance, security, agility, and cost.
Study Methodology:
The Sixth Annual Global Aryaka 2022 State of the WAN study surveyed over 1600 enterprise decision makers and practitioners including CIOs, CTOs, as well as IT, network, and security managers. Respondents were based in the Americas, EMEA, and APAC, with their companies representing every vertical, led by technology, software, manufacturing, financial, and retail. The survey asked respondents about their networking and performance challenges, priorities, and their plans for 2022 and beyond.
Download the Report:
Download Aryaka’s 6th Annual State of the WAN Report here.
…………………………………………………………………………………………………………………………………………………………………………………………………..
MPLS to SD-WAN Migration (Source: Aryaka):
Aryaka’s fully managed SD-WAN and SASE solution leverages a flexible core architecture, FlexCoreTM, optimized for per-site and per-application performance requirements. It offers full per customer resource reservation, end-to-end, at a global level. The HybridWAN solution also leverages direct MPLS and public internet connectivity options.
Aryaka manages the last-mile internet link performance with patented technology to eliminate packet loss and deliver on superior latency and jitter performance. By leveraging a private global L2 network, Aryaka eliminates the issue of guaranteeing deterministic QoS when multiple service provider administrative domains are involved (which is almost always the case in a global network).
Aryaka customers rely on its architecture to deliver on better-than-MPLS performance at a global level and at reduced cost, either augmenting the existing MPLS infrastructure or replacing it altogether over time.
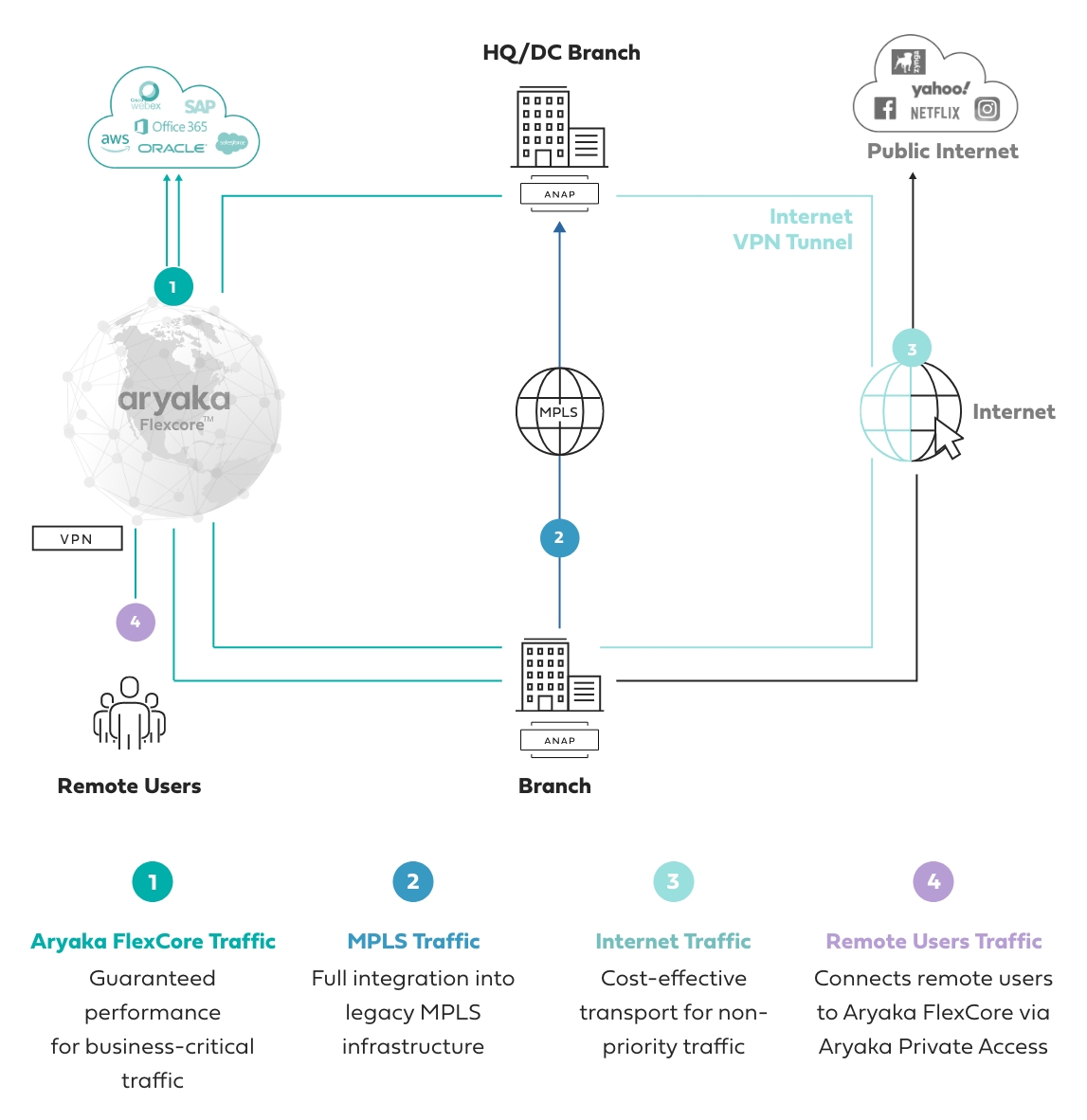
Source: Aryaka
References:
Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role
Dell’Oro: SD-WAN market grew 45% YoY; Frost & Sullivan: Fortinet wins SD-WAN leadership award
Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role
Disclaimer:
The IEEE Techblog has not covered this topic for a very long time, because there are no standards or accepted specifications for any type of SD-WAN or SASE interoperability. Those networks are all supplied by a single vendor, but that hasn’t stopped them from gaining market share, especially from legacy IP-MPLS VPNs. That’s even though functionality differs for each vendor’s SD-WAN or SASE offering and there is no interoperability, especially from one provider’s SD-WAN to another’s.
Explanations:
SD-WANs use Application-aware routing across the WAN, whereas classical SDN used a centralized controller to compute routes at the Network layer for the Control plane with “L2/L3 packet forwarding engines” in the Data Plane. The SDN Control and Data planes are separated with the “OpenFlow” API used to communicate between them.
NFV is not about routing but virtualizing network functions (“virtual appliances”) that would otherwise be implemented in hardware-firmware boxes.
Network virtualization (defined below) has played a key role in the popularity of SD-WAN and SASE, even though that network paradigm was not included in the original definition of SDN in which no overlay networks were permitted. (That was referred to as “SDN Washing” from 2011-2014, by SDN strongman Guru Parulker, now Executive Director of the Open Network Foundation.)
………………………………………………………………………………………….
Discussion:
At many data networking industry conferences and events from 2011 to 2014, participants claimed that Software Defined Networks (SDNs) would usher in a whole new era for networking. One colleague of mine said it would be “a new epoch for networking.” Instead, there were various versions of SDNs, used primarily by hyper-scale cloud service providers (most notably Google and Microsoft) and a few large telcos (e.g. NTT, AT&T). But SDN never spread to enterprise or campus networks.
When SDN fizzled out, the industry’s focus shifted to Software Defined WANs (SD-WANs), which provides user control of a virtual network overlay via the Application layer. There are three components to a SD-WAN:
- SD-WAN edge is where the network endpoints reside. This can be a branch office, a remote data center, or cloud platform.
- SD-WAN Orchestrator is the virtualized manager for network, overseeing traffic and applying policy and protocol set by operators.
- SD-WAN Controller centralizes management, and enables operators to see the network through a single software interface, and set policy for the orchestrator to execute.
In addition, there are three main types of SD-WAN architecture: on-premises, cloud-enabled, and cloud-enabled with a backbone.
SD-WANs continue to roll out in many different shapes, forms and flavors, without any standards for any type of interoperability (e.g no UNI, NNI, Interface to legacy IP-MPLS VPNs, etc). Even the definition and certification by the MEF (Metro Ethernet Forum) has failed to catch on so there is no uniform functionality between one SD-WAN and another.
Because of its virtualized network architecture [1.], SD-WANs don’t require specific hardware for specialized network functions. Instead, the infrastructure is made of commercial off-the-shelf (COTS) equipment, also known as white-boxes. Therefore, all SD-WAN products are 100% software based.
Note 1. Network virtualization is the process of transforming network functions into software and disconnecting them from the hardware they traditionally run on. The software still consumes the hardware’s resources, but is a separate entity that can be changed, moved, and segmented while the hardware remains the same.
The virtualized and software-based version of the network is an overlay on top of the physical network infrastructure. The physical network’s devices like switches and routers still perform tasks like packet forwarding, while how to forward those packets is handled by the software running on the switches and routers.
………………………………………………………………………………………….
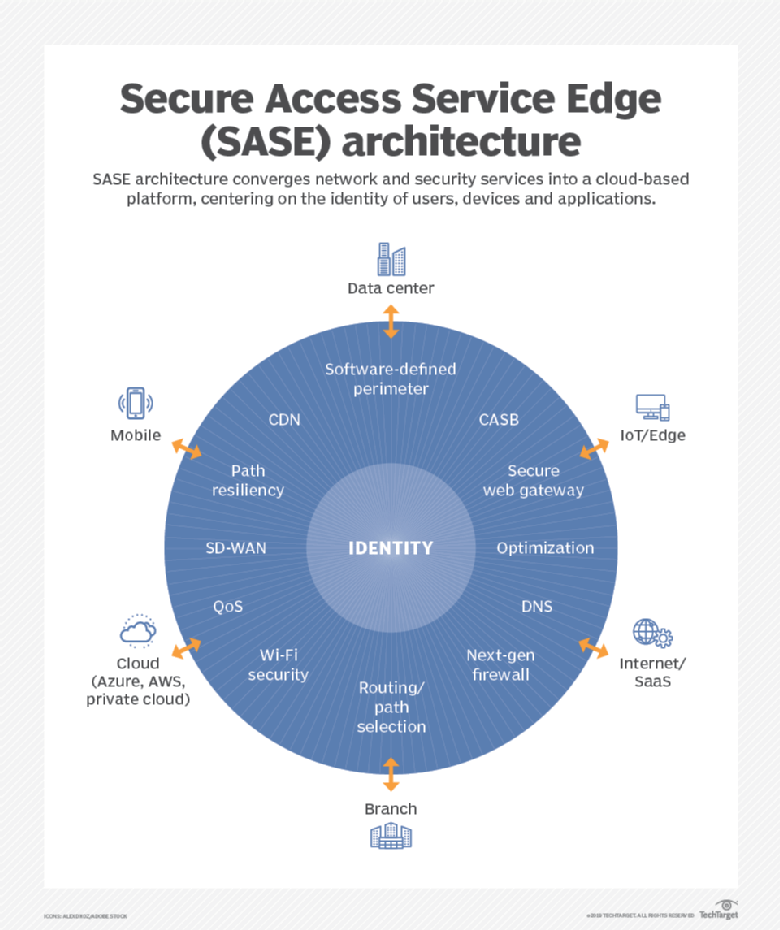
Meanwhile a newer entry known as Secure Access Service Edge (SASE) has garnered a lot of media attention. This Gartner-coined product category, which combines elements of SD-WAN, cloud-based security, and edge computing, has gained significant traction in the two years since its inception.
SASE’s remote access functionality and low barrier to entry made it an attractive option for enterprises trying to cope with the rapid shift to remote work due to the pandemic. Within months of the first lockdown orders going into effect, nearly every SD-WAN and security vendor had announced a SASE security architecture, either through internal development, partnerships, or acquisitions.
SASE is the convergence of wide area networking, or WAN, and network security services like CASB (Cloud Assisted Security Broker), FWaaS (Firewall as a Service) and Zero Trust, into a single, cloud-delivered service model.
According to Gartner, “SASE capabilities are delivered as a service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations.”
Gartner forecasts that, “by 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018.”
A SASE architecture identifies users and devices, applies policy-based security, and delivers secure access to the appropriate application or data. This approach allows organizations to apply secure access no matter where their users, applications or devices are located.
According to Cisco’s latest CISO Survival Guide, almost all (98%) CISOs plan to spend money on secure access service edge (SASE), and 55% of them intend to prioritize 25% to 75% of future IT security budgets on it, according to
Cisco surveyed more than 100 CISOs and security leaders for this report. The biggest shift for CISOs this year is toward SASE, following the pandemic and related trend of working from anywhere in the world, said Dug Song, chief strategy officer at Cisco Secure.
“I think hybrid work is here to stay,” Song told SDxCentral in an interview. Most organizations have decided to maintain flexible work for employees even post-pandemic, which requires changes to their IT security programs.
………………………………………………………………………………………….
Many industry experts say SASE services must be built on a cloud-native architecture (like 5G SA core network) and distributed across multiple edge locations.
While several vendors including Cisco and Fortinet have rejected the cloud native approach, arguing that networking and security appliances still have a role to play both at the branch and the edge, it’s a principle that’s reflected in Gartner’s own literature and wholeheartedly embraced by VMware, CATO and other SASE vendors.
Specifically, VMware offers a cloud-native SASE architecture that has combined multiple solutions in it such as SD-WAN Gateways, VMware Secure Access, ZTNA solution, SWG, CASB, AND VMware NSX Firewall. VMware delivers all these solutions through PoPs. It delivers the network and security services in an intrinsic or sequenced manner.
Cato CMO Yishay Yovel told SDxCentral, “The feeling I have is that a lot of the market is trying to talk about SASE now in a generic way, like everybody has everything, or everybody has the same capabilities, and it doesn’t matter exactly how they’re done.”
Yovel also said that just because a vendor claims to offer the full SASE software stack, doesn’t mean it’s been implemented in a way that’s scalable.
Many of the SASE functions — cloud-based firewalls in particular — are compute-intensive, they usually have to be run in cloud data centers and can’t run on the cloud provider’s more numerous content delivery network edge locations.
This dramatically limits the number of locations a SASE vendor can offer if relying on public cloud infrastructure. For example, Google Cloud claims services in 146 edge locations around the globe, but only operates 21 global data centers, which it refers to as regions.
Scalability and availability are another challenge, Yovel noted. In many cases, these virtual appliances aren’t multi-tenant and have to be assigned to a specific customer account, resulting in additional resources being required should the customer bump up against the limits of a single instance.
Yovel argues that unless a vendor’s SASE software stack is unified, customers may miss out on the ability to share context across multiple security or network functions. He explained that many functions, SD-WAN for example, are only aware of certain contexts like what application is being used, but this context could be used in conjunction with other contextual information like time, location, or identity to inform other parts of the SASE stack.
“We collect all the context elements. It doesn’t matter which part of these engines need them. Everything is built into a unified thing,” Yovel said.
The bottom line for today’s cybersecurity professionals is that both zero trust and SASE networking trends should be watched closely and integrated into forward-looking enterprise network architectural decisions.
…………………………………………………………………………………….
References:
https://www.sdxcentral.com/networking/sd-wan/definitions/software-defined-sdn-wan/
https://start.paloaltonetworks.com/gartner-report-roadmap-for-sase-convergence.html
https://www.paloaltonetworks.com/cyberpedia/what-is-sase
https://www.softwaretestinghelp.com/top-sase-vendors/
https://www.sdxcentral.com/articles/news/cato-ribs-palo-alto-networks-other-sase-imposters/2021/07/
https://www.sdxcentral.com/networking/sd-wan/
https://www.sdxcentral.com/networking/nfv/definitions/network-virtualization-and-how-it-works/
https://searchcloudsecurity.techtarget.com/tip/Why-its-SASE-and-zero-trust-not-SASE-vs-zero-trust

