SDN
Broadband Forum SDN/NFV Work Area launches four new projects at Bangkok Q4-2023 meeting
Introduction:
The Broadband Forum says their open standards and open broadband projects continue to deliver vital importance to companies, both small and large, as we focus on the latest industry trends, and extract most value to consumers, and transition to services-led broadband.
Progress on cloud based SDN/NFV was one of many accomplishments at this December’s meeting in Bangkok, Thailand. SDN and NFV are both software components, but they are different. SDN virtualizes the management of networks, while NFV converts network processes into software applications. SDN separates the data and control planes, allowing operators to manage features from a centralized location. NFV virtualizes network infrastructure, separating functions that typically run in hardware and implementing them as software. We believe the Forum’s SDN/NFV activity is very important as neither SDN or NFV have lived up to their potential and promise, primarily because they were premises based, rather than implemented in the cloud.
From a business perspective, the migration to SDN and NFV in the broadband network facilitates agile deployment of new customized distributed broadband services and applications. This enables new revenues and provider differentiation while managing Capex and OpEx both in the access network and in single and multi-tenant residential and business locations by implementing an agile network and enabling autonomous and automated operations.

Project Scope: Includes migration to and deployment of SDN/NFV-enabled implementations across all aspects of the broadband network. The scopes are:
- the definition of a new cloud-based environment with its related requirements, called Cloud-based Central Office (CloudCO)
- the architectural requirements, the interface specification among all the components with their related data models including the control-user plane separation interface for disaggregated access nodes
- the specification of virtual network functions and interface with their related data models
- the definition of requirements, interfaces and data models for autonomous and automated networks
Target: Define the Cloud-based Central Office (CloudCO) architecture using SDN, NFV, and cloud technologies to support network functions fundamentally redefining the architecture of access and aggregation networks. Support the migration of SDN and NFV into all aspects of broadband networks, facilitating the agile deployment of new distributed broadband services and applications for operators with greater operational efficiency and lower cost.
Progress: The SDN/NFV Work Area continues to progress the CloudCO project for virtualized network functions, SDN management and control and domain orchestration capabilities in a broadband network. The main activities currently ongoing are related to the disaggregation of the Access Node and defining the related interfaces. The Cloud Component Project Stream is continuing work on Automated Intelligence Management (AIM), Smart SD-WAN and virtual OMCI.
Three key documents near completion. TR-486 is set to be published in December 2023, WT-477 moves to Final Ballot, and WT-386 Issue 2 is currently resolving Straw Ballot comments.
Outcomes:
A productive quarterly meeting for the SDN/NFV Work Area saw four new projects approved. This was WT-403 Amendment 1 ‘PON Abstraction Interface for Time-Critical Applications’, WT-384 Issue 2 ‘CloudCO 2.0’, WT-436 Issue 2 ‘AIM Framework and Architecture’, and a project on Broadband Network Data Collection (BNDC).
A new Open Broadband proposal on CloudCO App SDK was presented to the Broadband Forum Board of Directors.
WT-477 on access node disaggregation has finished Straw Ballot review for both the baseline document and data model. The project has been approved to move to Final Ballot.
WT-413 Issue 2 on ‘SDN Management and Control Interfaces for CloudCO Network Functions’ is progressing. Previously, the SDN/NFV and Common YANG Work Areas reviewed the approach and agreed to report a detailed list of data models, so that vendors can rapidly discover the data models to be implemented for each access network function. The group will discuss the scope regarding the addition of ONU (Optical Network Unit) management and BAA chapter update before the Spring 2024 Meeting. The document is expected to enter Straw Ballot review once WT-477 and WT-486 are completed.
On the Artificial Intelligence and automation fronts, WT-486, which specifies the interfaces for the Automated Intelligence Management (AIM) framework specified in TR-436, has completed Final Ballot and will be published in December 2023. An AIM Tiger Team has completed gap analysis in WT-436 Issue 2 and WT-486 Issue 2. The Tiger Team discussed the Broadband Network Data Collection new project proposal and received approval from the group.
Straw Ballot comment resolution has been completed and WT-386i2 on Fixed Access Network Sharing.
A Tiger Team has been established to review the document on CloudCO interfaces (WT-411i2/WT-454i2) to include the Access SDN Management and Control northbound interface intent-based interactions addressing access network topology and abstraction, including inventory. An update was presented on the discussions held on the data models. The Metamodel needs further review and will be discussed in future weekly meetings.
Together with the Common YANG, the group held a joint session to discuss a new project for BAA – Access Device Abstraction Manager (BAA-ADAM). The groups will continue the discussions offline to clarify the scope and impact on CloudCO interfaces.
The group took part in this year’s CloudCO Demo at Network X in October. Key projects were involved in the demo, including WT-477 reference Disaggregated – Optical Line Terminal (D-OLT) Virtual Network Function, Northbound interface exposure of a L2-L3 network abstraction, Optical Network Terminal (ONT) telemetry over virtualized ONU Management and Control Interface (vOMCI), automation test-suite for OB-BAA, IPFIX adapter framework, and vOMCI Plugfest delta features.
References:
Shaping the future of Broadband – Broadband Forum (broadband-forum.org)
More information about the SDN/NFV Work Area can be found at: https://wiki.broadband-forum.org/display/BBF/SDN+and+NFV.
Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role
Disclaimer:
The IEEE Techblog has not covered this topic for a very long time, because there are no standards or accepted specifications for any type of SD-WAN or SASE interoperability. Those networks are all supplied by a single vendor, but that hasn’t stopped them from gaining market share, especially from legacy IP-MPLS VPNs. That’s even though functionality differs for each vendor’s SD-WAN or SASE offering and there is no interoperability, especially from one provider’s SD-WAN to another’s.
Explanations:
SD-WANs use Application-aware routing across the WAN, whereas classical SDN used a centralized controller to compute routes at the Network layer for the Control plane with “L2/L3 packet forwarding engines” in the Data Plane. The SDN Control and Data planes are separated with the “OpenFlow” API used to communicate between them.
NFV is not about routing but virtualizing network functions (“virtual appliances”) that would otherwise be implemented in hardware-firmware boxes.
Network virtualization (defined below) has played a key role in the popularity of SD-WAN and SASE, even though that network paradigm was not included in the original definition of SDN in which no overlay networks were permitted. (That was referred to as “SDN Washing” from 2011-2014, by SDN strongman Guru Parulker, now Executive Director of the Open Network Foundation.)
………………………………………………………………………………………….
Discussion:
At many data networking industry conferences and events from 2011 to 2014, participants claimed that Software Defined Networks (SDNs) would usher in a whole new era for networking. One colleague of mine said it would be “a new epoch for networking.” Instead, there were various versions of SDNs, used primarily by hyper-scale cloud service providers (most notably Google and Microsoft) and a few large telcos (e.g. NTT, AT&T). But SDN never spread to enterprise or campus networks.
When SDN fizzled out, the industry’s focus shifted to Software Defined WANs (SD-WANs), which provides user control of a virtual network overlay via the Application layer. There are three components to a SD-WAN:
- SD-WAN edge is where the network endpoints reside. This can be a branch office, a remote data center, or cloud platform.
- SD-WAN Orchestrator is the virtualized manager for network, overseeing traffic and applying policy and protocol set by operators.
- SD-WAN Controller centralizes management, and enables operators to see the network through a single software interface, and set policy for the orchestrator to execute.
In addition, there are three main types of SD-WAN architecture: on-premises, cloud-enabled, and cloud-enabled with a backbone.
SD-WANs continue to roll out in many different shapes, forms and flavors, without any standards for any type of interoperability (e.g no UNI, NNI, Interface to legacy IP-MPLS VPNs, etc). Even the definition and certification by the MEF (Metro Ethernet Forum) has failed to catch on so there is no uniform functionality between one SD-WAN and another.
Because of its virtualized network architecture [1.], SD-WANs don’t require specific hardware for specialized network functions. Instead, the infrastructure is made of commercial off-the-shelf (COTS) equipment, also known as white-boxes. Therefore, all SD-WAN products are 100% software based.
Note 1. Network virtualization is the process of transforming network functions into software and disconnecting them from the hardware they traditionally run on. The software still consumes the hardware’s resources, but is a separate entity that can be changed, moved, and segmented while the hardware remains the same.
The virtualized and software-based version of the network is an overlay on top of the physical network infrastructure. The physical network’s devices like switches and routers still perform tasks like packet forwarding, while how to forward those packets is handled by the software running on the switches and routers.
………………………………………………………………………………………….
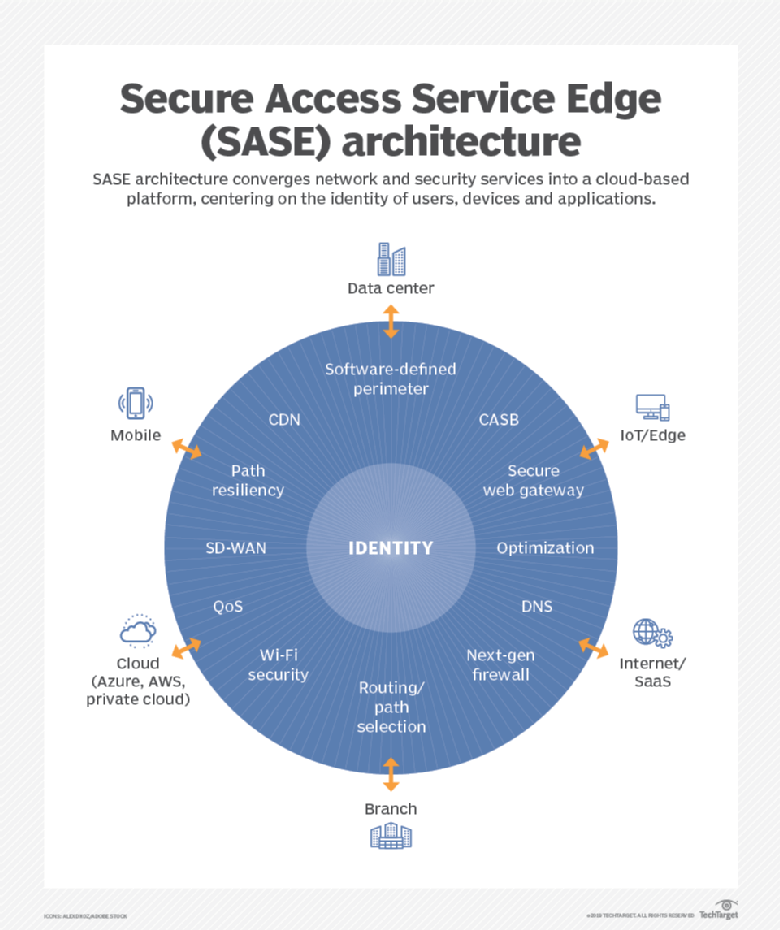
Meanwhile a newer entry known as Secure Access Service Edge (SASE) has garnered a lot of media attention. This Gartner-coined product category, which combines elements of SD-WAN, cloud-based security, and edge computing, has gained significant traction in the two years since its inception.
SASE’s remote access functionality and low barrier to entry made it an attractive option for enterprises trying to cope with the rapid shift to remote work due to the pandemic. Within months of the first lockdown orders going into effect, nearly every SD-WAN and security vendor had announced a SASE security architecture, either through internal development, partnerships, or acquisitions.
SASE is the convergence of wide area networking, or WAN, and network security services like CASB (Cloud Assisted Security Broker), FWaaS (Firewall as a Service) and Zero Trust, into a single, cloud-delivered service model.
According to Gartner, “SASE capabilities are delivered as a service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations.”
Gartner forecasts that, “by 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018.”
A SASE architecture identifies users and devices, applies policy-based security, and delivers secure access to the appropriate application or data. This approach allows organizations to apply secure access no matter where their users, applications or devices are located.
According to Cisco’s latest CISO Survival Guide, almost all (98%) CISOs plan to spend money on secure access service edge (SASE), and 55% of them intend to prioritize 25% to 75% of future IT security budgets on it, according to
Cisco surveyed more than 100 CISOs and security leaders for this report. The biggest shift for CISOs this year is toward SASE, following the pandemic and related trend of working from anywhere in the world, said Dug Song, chief strategy officer at Cisco Secure.
“I think hybrid work is here to stay,” Song told SDxCentral in an interview. Most organizations have decided to maintain flexible work for employees even post-pandemic, which requires changes to their IT security programs.
………………………………………………………………………………………….
Many industry experts say SASE services must be built on a cloud-native architecture (like 5G SA core network) and distributed across multiple edge locations.
While several vendors including Cisco and Fortinet have rejected the cloud native approach, arguing that networking and security appliances still have a role to play both at the branch and the edge, it’s a principle that’s reflected in Gartner’s own literature and wholeheartedly embraced by VMware, CATO and other SASE vendors.
Specifically, VMware offers a cloud-native SASE architecture that has combined multiple solutions in it such as SD-WAN Gateways, VMware Secure Access, ZTNA solution, SWG, CASB, AND VMware NSX Firewall. VMware delivers all these solutions through PoPs. It delivers the network and security services in an intrinsic or sequenced manner.
Cato CMO Yishay Yovel told SDxCentral, “The feeling I have is that a lot of the market is trying to talk about SASE now in a generic way, like everybody has everything, or everybody has the same capabilities, and it doesn’t matter exactly how they’re done.”
Yovel also said that just because a vendor claims to offer the full SASE software stack, doesn’t mean it’s been implemented in a way that’s scalable.
Many of the SASE functions — cloud-based firewalls in particular — are compute-intensive, they usually have to be run in cloud data centers and can’t run on the cloud provider’s more numerous content delivery network edge locations.
This dramatically limits the number of locations a SASE vendor can offer if relying on public cloud infrastructure. For example, Google Cloud claims services in 146 edge locations around the globe, but only operates 21 global data centers, which it refers to as regions.
Scalability and availability are another challenge, Yovel noted. In many cases, these virtual appliances aren’t multi-tenant and have to be assigned to a specific customer account, resulting in additional resources being required should the customer bump up against the limits of a single instance.
Yovel argues that unless a vendor’s SASE software stack is unified, customers may miss out on the ability to share context across multiple security or network functions. He explained that many functions, SD-WAN for example, are only aware of certain contexts like what application is being used, but this context could be used in conjunction with other contextual information like time, location, or identity to inform other parts of the SASE stack.
“We collect all the context elements. It doesn’t matter which part of these engines need them. Everything is built into a unified thing,” Yovel said.
The bottom line for today’s cybersecurity professionals is that both zero trust and SASE networking trends should be watched closely and integrated into forward-looking enterprise network architectural decisions.
…………………………………………………………………………………….
References:
https://www.sdxcentral.com/networking/sd-wan/definitions/software-defined-sdn-wan/
https://start.paloaltonetworks.com/gartner-report-roadmap-for-sase-convergence.html
https://www.paloaltonetworks.com/cyberpedia/what-is-sase
https://www.softwaretestinghelp.com/top-sase-vendors/
https://www.sdxcentral.com/articles/news/cato-ribs-palo-alto-networks-other-sase-imposters/2021/07/
https://www.sdxcentral.com/networking/sd-wan/
https://www.sdxcentral.com/networking/nfv/definitions/network-virtualization-and-how-it-works/
https://searchcloudsecurity.techtarget.com/tip/Why-its-SASE-and-zero-trust-not-SASE-vs-zero-trust
Masergy Performance Edge™ minimizes packet loss over public broadband connections
Masergy, a software-defined network and cloud platform company, today announced its latest patent-pending innovation which is aimed at solving a fundamental problem with broadband internet transport. Masergy Performance EdgeTM, a new SD-WAN and SASE (Secure Access Service Edge) capability, minimizes packet loss over public broadband connections, making them perform more like a private Ethernet circuit.
“Today broadband is being used ubiquitously” in home and business sites, says Ajay Pandya, director of Product Management for Masergy. “We are seeing this over the last year a lot. We used to sell 60-70% of our sites with one of the links as broadband. Now it’s in the 90’s.”
Broadband can be up to 70% cheaper than private access networks, says Pandya, but it’s still a “best effort” technology that doesn’t always provide reliable performance for applications such as voice and video conferencing.
“If I’m a contact center person or a power-user executive delivering my quarterly announcement to analysts, I don’t want the connection to be any less than excellent,” says Pandya. He also said that Masergy aims to improve the quality of last-mile connections with its Performance Edge.
“Masergy Performance EdgeTM is revolutionary because it turns the low-cost, low-performance access methodology into a high-performing service meeting the demands of today’s digital-first businesses,” said Zeus Kerravala, Founder and Principal Analyst, ZK Research. “It saves precious IT dollars and removes the productivity uncertainties of working from home all within a SASE environment.”
Most companies have become more dependent on broadband since the 2020 pandemic, but it hasn’t always served them well — particularly in cases where guaranteed performance is needed. According to an Altman Solon 2021 State of SD-WAN Study, 50% of IT leaders using only public access say their application performance is insufficient, and 48% say the cost savings don’t justify the lower quality of service. Inherently broadband is a “best effort” technology unfit for real-time data applications like voice and video conferencing. Thus, broadband often fails to deliver the performance needed, causing losses in productivity, sales, and revenue.
“Masergy is working to ensure our clients’ new need for broadband doesn’t impact their business continuity. Remote work success shouldn’t hinge on network connectivity types, and we’ve created Masergy Performance EdgeTM to make sure it doesn’t,” said Chris MacFarland, CEO, Masergy. “Masergy pioneered software-defined networking 20 years ago. We were the first to market with AIOps integrated in our SD-WAN and SASE solutions, and we’re already on the path to autonomous networking — so there’s no better company to revolutionize broadband, making it the high-performance, predictable service everyone wants it to be.
The patent-pending Performance Edge is aimed at assisting home workers, SD-WAN, SASE and MPLS customers in improving their broadband performance by reducing packet loss. The feature can be added on to Masergy’s SD-WAN and SASE services, but there is an additional cost to utilize Performance Edge. In addition, it’s currently centrally managed, so customers need to request it directly from Masergy to turn the service on.
Masergy Performance EdgeTM is available with Masergy’s Managed SD-WAN Secure and SASE offerings and uses proprietary network architecture along with industry standard and compatible routing algorithms to enable businesses of all sizes to realize increased efficiency and productivity. It provides these key benefits:
- Better Performance: Minimize packet loss over public broadband connections for more predictable application experiences
- Less Expensive: Save up to 70% compared to the cost of a private line and reduce outages with AI-powered performance visibility
- Fast to Install: Connect new sites in days versus weeks and boost existing broadband circuits for immediate results
 Image Credit: Masergy
Image Credit: Masergy
Zeus Kerravala, founder and principal analyst of ZK Research, told Light Reading that Performance Edge could be useful in delivering the “performance of private IT with broadband” for remote workers, retail and small branch locations. Kerravala says Masergy is “using a multitude of different optimization techniques to make that broadband connection work better” with tools such as WAN optimization, compression and forward-error correction.
“SD-WAN does a good job of load balancing across 2 connections, but there are a number of situations where you only have your broadband connection available … Masergy also has their MPLS backbone, so it’s the combination of two that gives you the end-to-end performance. Performance Edge optimizes the last mile, and Masergy has always been good at the middle mile,” says Kerravala.
References:
Learn more about Masergy Performance Edge
IHS Markit: Enterprise Data Center SDN savings yet to be realized
by Josh Bancroft, IHS Markit Analyst
IHS Markit recently surveyed 100 North American enterprises that are evaluating or implementing software-defined networking (SDN) for the data center by 2020. Respondents currently evaluating SDN expect that it will drive operational- and capital-expenditure decreases at a faster pace than what has been experienced by those already deploying SDN.
“Migrating to SDN means deploying new equipment, upgrading existing equipment, and training IT staff, which requires investment,” said Josh Bancroft, senior analyst, cloud and data center research, IHS Markit. “Those evaluating SDN need to adjust their expectations that savings might not be felt immediately, but instead might happen over a longer period of time.”
The 2018 “Data Center SDN Strategies North American Enterprise Survey” indicated that the transition to live SDN deployment is well underway. By the end of 2019, 74 percent of respondents will be in production trials, and 36 percent will be in live production, up from 38 percent and 20 percent, respectively, in 2018. Enhancements have been made by vendors, including integrating network analytics to improve application performance and security. Doing so will encourage enterprises to deploy SDN, since improved application performance and improved security were two of the top drivers for deploying SDN. Other top deployment drivers for SDN included; decreased operating costs, simplified network provisioning and improved management capability.
In the IHS Markit survey, Cisco, VMware, and Dell EMC were identified as the SDN hardware and software manufacturers with which respondents were most familiar.
Following are some additional highlights from the survey:
- Top deployment barriers among the respondents were the interruption of critical network operations (30 percent), interoperability with existing network equipment (29 percent) and lack of trained staff (29 percent)
- Less than half (48 percent) of respondents expect capital expenditures (capex) to increase again in the second year of deployment. However, capex increased in the second year for 61 percent of those who have deployed SDN, which suggests those evaluating deployment should adjust their expectations.
- Nearly one-third (31 percent) of respondents chose automated disaster recovery as the top use case for capex reduction, while 35 percent selected automated provisioning as the top use case for operating expenditure (opex) reduction, and 30 percent chose automation for application deployment as the top use case for employee productivity.
- By 2020, 83 percent of respondents will be in live production with data center SDN.
Data Center SDN Strategies North American Enterprise Survey
This IHS Markit survey analyzes the trends and assesses the needs of enterprises deploying SDN in their data centers. The study probes issues defining how the enterprise market will evolve with data center SDN, including deployment drivers and barriers, rollout plans, applications, use cases, vendors installed and under evaluation, top rated vendors, and more.
IHS Markit: SDN deployed by 78% of global service providers at end of 2018
By Michael Howard, senior research director, carrier networks, IHS Markit
Highlights
- All of the 23 service providers surveyed reported that they will deploy SDN at some point. More than three-quarters (78 percent) of those providers will deploy or evaluate the architecture by the end of this year, growing to 87 percent by the end of 2019.
- Software-defined wide-area networks (SD-WANs) leads the list of SDN-based services expected to generate new revenue, with 78 percent of respondents identifying it as a key deployment goal, while nearly half (48 percent) plan to implement network slicing for IoT.
- Automation and reduction of capex and operating-expenditure (opex) are among the goals for the top domains for SDN deployments. By the end of 2019, 74 percent of respondents will use SDN to automate the delivery of new services, followed by operations and management at 65 percent.
Our analysis
Service providers are in the early stages of a long-term transition to software-defined networks (SDN), according to the sixth annual “Carrier SDN Strategies Service Provider Survey” in 2018 from IHS Markit. Various barriers and drivers have become more prominent, as operators get closer to commercial deployment, although the barriers remain. These barriers include the problem of products that are not carrier grade and difficulty with integration into existing networks.
Service providers around the globe – representing 44 percent of worldwide telecom capital expenditure (capex) and 44 percent of revenue – are investing in software defined networks (SDNs) as part of a larger move to automate their networks and transform their internal processes, operations, and the way they offer services to their customers. Providers view SDN as a key technology underpinning the fundamental changes in telecom network architecture that delivers benefits in new service agility, quicker time to revenue, automation, operational efficiency, and capex savings.
Many operators have some parts of their networks running under SDN control. The rest are moving from their proof-of-concept (PoC) investigations and evaluations for SDN toward commercial deployments in the tail end of 2018 and 2019.
The top two reasons service providers are investing in and deploying network SDN are the following:
- Simplification and automation of service provisioning, leading to service agility and quicker time to revenue
- End-to-end network management and control as part of increased automation
The majority of service providers are investing in SDN in order to simplify and automate the provisioning of their networks for end-to-end network and service management and control—with the goal of having a global view of network conditions across the various vendors’ equipment, network layers, and technologies. SDN figures in provider plans to generate revenue, with multi-cloud and network slicing for applications and IoT figuring more prominently this year.
Still, carriers will learn that some avenues are not as fruitful as expected, and telecom equipment manufacturers and software suppliers may well invent new approaches that open up new applications.
Carrier SDN Strategies Service Provider Survey – 2018
This sixth annual survey of global service providers explores plans and strategies of 23 operators for evaluating and deploying SDNs. The study identifies the drivers for this fundamental change in service provider network architecture and explores use cases, development stages, barriers, applications, target network areas, and timing of deployment plans.
……………………………………………………………………………………………………………………………………………………………………………………………………………………
Editor’s Note:
But what SDN model or version was implemented by these service providers? That is not stated in Michael Howard’s report.
There’s the classical SDN/Open Flow model from ONF, the overlay or virtual network model, the evolutionary model, hybrid model, DevOps management model, VMWare’s two NSX versions, etc
Also, most versions of SDN use a centralized controller and NOT segment or hop by hop routing. Yet Cisco and Juniper routers can handle segment-routing traffic. Their versions of SDN are ready for segment routing, as well. Moreover, Linux has an open source implementation of segment routing, and Cumulus Networks’ Linux-based network OS also supports it.
With so many different versions of SDN, it appears that network equipment and software built for one SDN based network will not work on ANY other service provider’s SDN unless multiple SDN versions/models are supported in the same equipment/software.
References:
https://www.rcrwireless.com/20170811/three-different-sdn-models-tag27-tag99
https://searchnetworking.techtarget.com/tip/Three-models-of-SDN-explained
https://searchvmware.techtarget.com/opinion/VMwares-two-NSX-versions-are-the-future-of-SDN


