Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role
Disclaimer:
The IEEE Techblog has not covered this topic for a very long time, because there are no standards or accepted specifications for any type of SD-WAN or SASE interoperability. Those networks are all supplied by a single vendor, but that hasn’t stopped them from gaining market share, especially from legacy IP-MPLS VPNs. That’s even though functionality differs for each vendor’s SD-WAN or SASE offering and there is no interoperability, especially from one provider’s SD-WAN to another’s.
Explanations:
SD-WANs use Application-aware routing across the WAN, whereas classical SDN used a centralized controller to compute routes at the Network layer for the Control plane with “L2/L3 packet forwarding engines” in the Data Plane. The SDN Control and Data planes are separated with the “OpenFlow” API used to communicate between them.
NFV is not about routing but virtualizing network functions (“virtual appliances”) that would otherwise be implemented in hardware-firmware boxes.
Network virtualization (defined below) has played a key role in the popularity of SD-WAN and SASE, even though that network paradigm was not included in the original definition of SDN in which no overlay networks were permitted. (That was referred to as “SDN Washing” from 2011-2014, by SDN strongman Guru Parulker, now Executive Director of the Open Network Foundation.)
………………………………………………………………………………………….
Discussion:
At many data networking industry conferences and events from 2011 to 2014, participants claimed that Software Defined Networks (SDNs) would usher in a whole new era for networking. One colleague of mine said it would be “a new epoch for networking.” Instead, there were various versions of SDNs, used primarily by hyper-scale cloud service providers (most notably Google and Microsoft) and a few large telcos (e.g. NTT, AT&T). But SDN never spread to enterprise or campus networks.
When SDN fizzled out, the industry’s focus shifted to Software Defined WANs (SD-WANs), which provides user control of a virtual network overlay via the Application layer. There are three components to a SD-WAN:
- SD-WAN edge is where the network endpoints reside. This can be a branch office, a remote data center, or cloud platform.
- SD-WAN Orchestrator is the virtualized manager for network, overseeing traffic and applying policy and protocol set by operators.
- SD-WAN Controller centralizes management, and enables operators to see the network through a single software interface, and set policy for the orchestrator to execute.
In addition, there are three main types of SD-WAN architecture: on-premises, cloud-enabled, and cloud-enabled with a backbone.
SD-WANs continue to roll out in many different shapes, forms and flavors, without any standards for any type of interoperability (e.g no UNI, NNI, Interface to legacy IP-MPLS VPNs, etc). Even the definition and certification by the MEF (Metro Ethernet Forum) has failed to catch on so there is no uniform functionality between one SD-WAN and another.
Because of its virtualized network architecture [1.], SD-WANs don’t require specific hardware for specialized network functions. Instead, the infrastructure is made of commercial off-the-shelf (COTS) equipment, also known as white-boxes. Therefore, all SD-WAN products are 100% software based.
Note 1. Network virtualization is the process of transforming network functions into software and disconnecting them from the hardware they traditionally run on. The software still consumes the hardware’s resources, but is a separate entity that can be changed, moved, and segmented while the hardware remains the same.
The virtualized and software-based version of the network is an overlay on top of the physical network infrastructure. The physical network’s devices like switches and routers still perform tasks like packet forwarding, while how to forward those packets is handled by the software running on the switches and routers.
………………………………………………………………………………………….
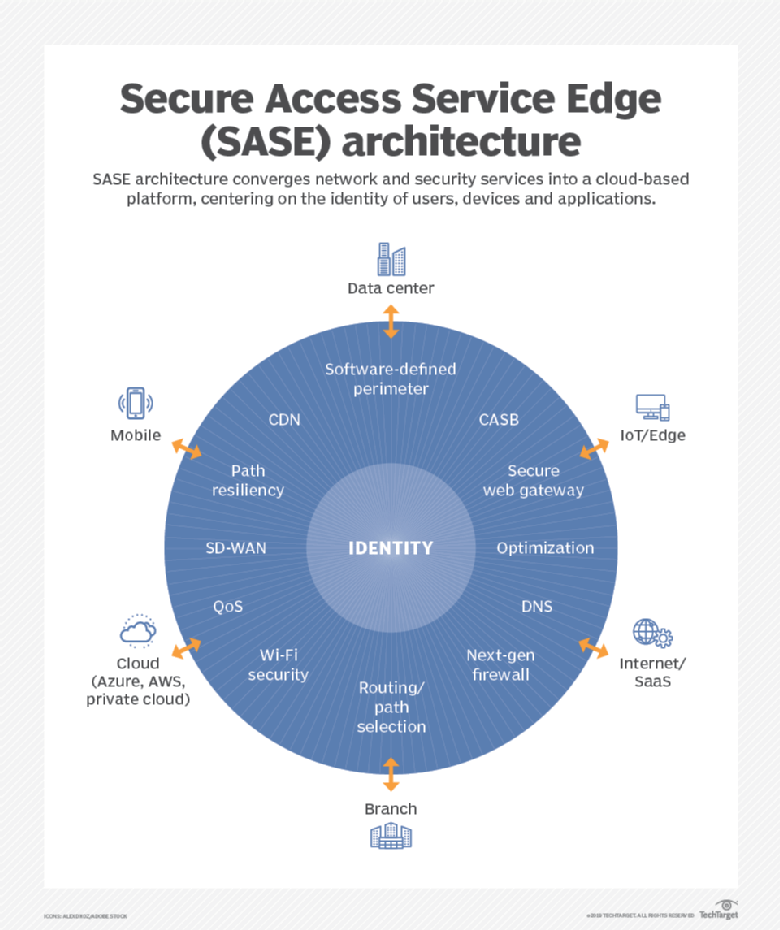
Meanwhile a newer entry known as Secure Access Service Edge (SASE) has garnered a lot of media attention. This Gartner-coined product category, which combines elements of SD-WAN, cloud-based security, and edge computing, has gained significant traction in the two years since its inception.
SASE’s remote access functionality and low barrier to entry made it an attractive option for enterprises trying to cope with the rapid shift to remote work due to the pandemic. Within months of the first lockdown orders going into effect, nearly every SD-WAN and security vendor had announced a SASE security architecture, either through internal development, partnerships, or acquisitions.
SASE is the convergence of wide area networking, or WAN, and network security services like CASB (Cloud Assisted Security Broker), FWaaS (Firewall as a Service) and Zero Trust, into a single, cloud-delivered service model.
According to Gartner, “SASE capabilities are delivered as a service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations.”
Gartner forecasts that, “by 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018.”
A SASE architecture identifies users and devices, applies policy-based security, and delivers secure access to the appropriate application or data. This approach allows organizations to apply secure access no matter where their users, applications or devices are located.
According to Cisco’s latest CISO Survival Guide, almost all (98%) CISOs plan to spend money on secure access service edge (SASE), and 55% of them intend to prioritize 25% to 75% of future IT security budgets on it, according to
Cisco surveyed more than 100 CISOs and security leaders for this report. The biggest shift for CISOs this year is toward SASE, following the pandemic and related trend of working from anywhere in the world, said Dug Song, chief strategy officer at Cisco Secure.
“I think hybrid work is here to stay,” Song told SDxCentral in an interview. Most organizations have decided to maintain flexible work for employees even post-pandemic, which requires changes to their IT security programs.
………………………………………………………………………………………….
Many industry experts say SASE services must be built on a cloud-native architecture (like 5G SA core network) and distributed across multiple edge locations.
While several vendors including Cisco and Fortinet have rejected the cloud native approach, arguing that networking and security appliances still have a role to play both at the branch and the edge, it’s a principle that’s reflected in Gartner’s own literature and wholeheartedly embraced by VMware, CATO and other SASE vendors.
Specifically, VMware offers a cloud-native SASE architecture that has combined multiple solutions in it such as SD-WAN Gateways, VMware Secure Access, ZTNA solution, SWG, CASB, AND VMware NSX Firewall. VMware delivers all these solutions through PoPs. It delivers the network and security services in an intrinsic or sequenced manner.
Cato CMO Yishay Yovel told SDxCentral, “The feeling I have is that a lot of the market is trying to talk about SASE now in a generic way, like everybody has everything, or everybody has the same capabilities, and it doesn’t matter exactly how they’re done.”
Yovel also said that just because a vendor claims to offer the full SASE software stack, doesn’t mean it’s been implemented in a way that’s scalable.
Many of the SASE functions — cloud-based firewalls in particular — are compute-intensive, they usually have to be run in cloud data centers and can’t run on the cloud provider’s more numerous content delivery network edge locations.
This dramatically limits the number of locations a SASE vendor can offer if relying on public cloud infrastructure. For example, Google Cloud claims services in 146 edge locations around the globe, but only operates 21 global data centers, which it refers to as regions.
Scalability and availability are another challenge, Yovel noted. In many cases, these virtual appliances aren’t multi-tenant and have to be assigned to a specific customer account, resulting in additional resources being required should the customer bump up against the limits of a single instance.
Yovel argues that unless a vendor’s SASE software stack is unified, customers may miss out on the ability to share context across multiple security or network functions. He explained that many functions, SD-WAN for example, are only aware of certain contexts like what application is being used, but this context could be used in conjunction with other contextual information like time, location, or identity to inform other parts of the SASE stack.
“We collect all the context elements. It doesn’t matter which part of these engines need them. Everything is built into a unified thing,” Yovel said.
The bottom line for today’s cybersecurity professionals is that both zero trust and SASE networking trends should be watched closely and integrated into forward-looking enterprise network architectural decisions.
…………………………………………………………………………………….
References:
https://www.sdxcentral.com/networking/sd-wan/definitions/software-defined-sdn-wan/
https://start.paloaltonetworks.com/gartner-report-roadmap-for-sase-convergence.html
https://www.paloaltonetworks.com/cyberpedia/what-is-sase
https://www.softwaretestinghelp.com/top-sase-vendors/
https://www.sdxcentral.com/articles/news/cato-ribs-palo-alto-networks-other-sase-imposters/2021/07/
https://www.sdxcentral.com/networking/sd-wan/
https://www.sdxcentral.com/networking/nfv/definitions/network-virtualization-and-how-it-works/
https://searchcloudsecurity.techtarget.com/tip/Why-its-SASE-and-zero-trust-not-SASE-vs-zero-trust
6 thoughts on “Shift from SDN to SD-WANs to SASE Explained; Network Virtualization’s important role”
Comments are closed.



Why SDN never spread to enterprise or campus networks ?
Because of lack of tech support for enterprise/campus networks
“Going forward, multi-cloud is at the center of gravity for everything we do,” said VMware CEO Raghu Raghuram said his opening keynote at VMworld.
And then he announced VMware Cross-Cloud, which is a set of integrated services that the vendor says provides customers the flexibility to build, run, and secure applications across any cloud.
“There are three key advantages you get with VMware Cross-Cloud services,” Raghuram said. “First: Go faster. With Cross-Cloud services, you can accelerate your cloud journey. Second: Spend Less. You get big gains and cost efficiency. And third: Be free. With Cross-Cloud services you get maximum flexibility and choice across any cloud.”
The services include five key pieces:
A platform for building and deploying cloud-native apps;
Cloud infrastructure for operating and running enterprise apps;
Cloud management for monitoring the performance and cost of apps across multiple clouds;
Security and networking that spans customers’ multi-cloud environment to connect and secure apps;
And a digital workspace to accommodate the distributed workforce and manage edge-native apps.
Not coincidentally, VMware also announced new products or updates across all of these five areas.
The vendor originally announced Tanzu Application Platform, its cloud-native app platform currently in beta, at its SpringOne developer event last month. Today, VMware announced new capabilities including more developer tooling and a framework for platform operators to configure policies of deployed workloads to ensure that all workloads follow best practices.
For cloud infrastructure: VMware announced Project Arctic, a tech preview, that natively integrates cloud connectivity into vSphere and allows IT admins to access Cross-Cloud services through vCenter.
Project Ensemble is VMware’s new unified control plane for VMware Cloud. It’s also a tech preview, and it provides a unified view across vRealize Cloud Management Services to monitor app performance and cost.
At VMworld, the vendor added API and Kubernetes security capabilities to cover multi-cloud security and networking.
And finally, VMware announced a new Edge Compute Stack — an integrated virtual machine and container-based stack for edge-native apps.
“What is Cross-Cloud all about at the end of the day? It’s about giving you the power to make your own decisions and control your destiny,” Raghuram said. “I call this enterprise sovereignty.”
Similar to data sovereignty, which involves controlling enterprise data where it resides, “enterprise sovereignty speaks at a higher level about preserving your freedom of choice, both now and in the future,” he said. “At VMware, we give you the freedom and control.”
https://www.sdxcentral.com/articles/news/vmware-ceo-flies-multi-cloud-flag-at-vmworld/2021/10/
SD-WAN provides a secure path from siloed enterprise networks to the public, private and hybrid cloud
SD-WAN is a reset in thinking about how a Wide Area Network (WAN) should work. It’s a virtual WAN architecture, an overlay that can work with different network transport services, including broadband. SD-WAN enables organizations to centrally manage traffic using the principles of Software Defined Networking (SDN), without the limitations imposed by physical network infrastructure.
SD-WAN centralizes network control, management, provisioning and security, despite the continued decentralization of data, as businesses move to the cloud. A few companies stand apart from the rest when it comes to offering SD-WAN solutions. Cisco is the market leader, followed by Fortinet and VMware, according to a report from Dell’Oro Group.
Enterprise spend on SD-WAN has accelerated in recent times. Businesses are upgrading network infrastructure to accommodate changing objectives and shifting workforce demands, as well. Sales of SD-WAN solutions rose 45% year-over-year for the third calendar quarter of 2021, according to Dell’Oro. The research firm noted that Cisco’s quarterly SD-WAN revenue nearly doubled in the quarter, with especially strong growth in North America.
The State of the WAN
For years, the literal backbone of enterprise WAN connectivity has been Multi-Protocol Label Switching (MPLS). MPLS is a routing technique which directs data based on short path labels rather than long network addresses. Those paths labels speed network traffic by identifying virtual links between distant network nodes, eliminating routing delays.
MPLS supports a range of network transport services. And as the acronym implies, it supports multiple networking protocols: Internet Protocol (IP), Asynchronous Transport Mode (ATM) and Frame Relay, for example.
Regardless of protocol, MPLS connections all have one thing in common: They’re dedicated circuits, and require specialized routing hardware at both ends. This complicates provisioning and limits scale. What’s more, traditional WAN topologies typically backhaul all network traffic for security. This creates bottlenecks and complicates network traffic management.
A WAN topology that restricts the flow of network traffic to the cloud is at direct odds with enterprise digitalization strategies. Enterprises depend on more cloud-based services than ever to manage essential business functions. SaaS platforms like Customer Relationship Management (CRM) and Enterprise Resource Planning (ERP) are examples. These platforms provide organizations with agility, flexibility, and scale, but being cloud-native demands a new approach when it comes to practical network management.
SD-WAN modernizes network operations for the cloud
As enterprises and users turn to the cloud, the difference between data center cloud and public cloud can get nebulous. Increasing public cloud-dependence and adjacency introduces complications to network security and compliance. Data sovereignty, compliance and security is top of mind for every IT professional.
Many enterprises leaning into to the cloud are implementing Software-Defined Wide Area Networking (SD-WAN) to manage their networks. SD-WAN abstracts the networks’ transport service altogether. It’s a virtual WAN architecture which enables organizations to leverage whatever transport service they need — broadband, MLPS, 4G LTE, 5G.
By separating the network’s control plane altogether, SD-WAN enables businesses to centralize network management, security, and provisioning. SD-WAN replaces dedicated network hardware with Virtual Network Functions (VNFs) in place of physical networking hardware.
VNFs specifically replace devices like network routers and firewalls. VNFs are implemented as Virtual Machines (VMs) which run as software in the IT cloud, operating on commercial off-the-shelf (COTS) server hardware. Accompanied by Cloud-native Network Functions (CNFs), they provide IT departments with the ability to scale services instantly to meet demand. As software rather than hardware, VNFs and CNFs can be continuous updated and optimized.
While VNFs are nothing new to enterprise IT, what’s new here in the SD-WAN equation is how SDN itself helps IT operations manage network operations and data security for branch and remote locations. There are some key differences, too.
“SDN advocates a central controller to dictate network behaviors. In contrast, SD-WAN generally manages based on central policy control, but decisions may also be made locally while taking into consideration the corporate policies. Or decisions can be made centrally while incorporating knowledge of local conditions reported by remote network nodes,” said VMware.
SD-WAN in the wild
SD-WAN has emerged as an opportunity for carriers and hyperscalers, Over-the-Top (OTT) service providers, and edge services. In December, Amazon introduced AWS Cloud WAN as a way to replace what it called a “patchwork” of services needed to handle private network control and management. AWS Cloud WAN connects on-prem data centers, branch offices and cloud resources together on AWS’ global backbone, consolidating management through a central dashboard.
Verizon features SD-WAN managed by Cisco as an option for its Network as a Service (NaaS). It comprises Cisco Umbrella security framework, manages zero trust application access and provides managed services through Cisco products including Pluggable Interface Modules and Catalyst Cellular Gateways.
https://www.rcrwireless.com/20220113/telco-cloud/what-is-software-defined-wide-area-networking-sd-wan
Verizon said in its guide for the “right approach” to secure access service edge (SASE) – the Gartner-coined infrastructure that combines cloud-native network and security stacks- that managing and securing an increasingly complex environment poses “significant challenges.”
https://www.verizon.com/business/resources/T8d/whitepapers/the-right-approach-to-sase.pdf
In 2021 Verizon Business launched SASE solution with a multi-vendor approach that combines SD-WAN and network security capabilities from Versa Networks and Zscaler into a single managed service. Rival AT&T had rolled out its own solution earlier that year in partnership with Fortinet.
Verizon cites the COVID-19 pandemic, virtualization and the move to the cloud, increased security threats, and a shift away from the network appliance box as the primary factors that drove the “SASE frenzy” in recent years.
By 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018, according to the Verizon guide.
“Getting SASE right may be a complex proposition that presents significant challenges,” the provider said. “For one thing, it is a still-evolving technology target.”
The SASE architecture combines network edge capabilities like SD-WAN and a set of security capabilities Gartner dubbed the security services edge (SSE) – a cloud-delivered suite that includes zero-trust network access (ZTNA), cloud-access security broker (CASB), secure web gateway (SWG), and firewall-as-a-service (FWaaS).
The major elements that make up SASE have been around in some form or another for “at least 10 years,” Verizon pointed out.
For this reason, a critical component of getting SASE right is cross-technology integration. “There’s no one-size-fits-all SASE solution, which means enterprises will need to be comfortable working with a variety of technologies in order to build an effective implementation that solves a given organization’s specific challenges,” the provider said.
Enterprises adopting SASE need to be able to integrate a broad range of network technologies from physical transport – like private IP and MPLS – up through the virtualization SDN layer in order to build an integrated SD-WAN capability with traffic routing, prioritization, and bandwidth optimization.
Another “key ingredient” to SASE is edge computing like content delivery networks, multi-access edge computing (MEC), or an IoT gateway. “Managing security across these complex and distributed systems will be essential and require a deep understanding of how edge computing fits into the SASE model,” Verizon explained.
Orchestrating SASE Infrastructure
How the technology components of SASE come together is critical.
Verizon recommends enterprises implement service chaining as a key component of SASE because it is a “way of automating and optimizing the service delivery experience.”
In an environment where many vendors are still unable to provide a complete end-to-end SASE solution, organizations likely need to combine technologies and products to create their desired solutions. “Being able to optimize new and already-deployed technology components so each is functioning and contributing at its full potential will be important,” Verizon said.
The ability to conduct testing to make sure SASE is properly integrated and performing at necessary levels will also be critical. Verizon indicated this requires the “proper tools to conduct the integration, performance, and stress testing needed to ensure that functions have been deployed in the optimal order and the most efficient configuration.”
Service chaining and other orchestration in a virtual network requires expertise, which has led to challenges for many organizations in the midst of a global skill shortage. However, this can be mitigated in part through organizational restructuring that sees networking and security teams – which have traditionally operated separately – merge their administration and management from the organizational perspective.
Lastly, Verizon suggested that because SASE is still a work in progress, “CIO and CISO groups will need to rethink their respective roles in supporting enterprise infrastructure operations.”
“Proper governance will be key to success as these changes percolate down through the organization, as they will eventually touch the network architects, security architects, application architects and others that need to work together to execute on a company’s SASE strategy,” Verizon added.
https://www.sdxcentral.com/articles/analysis/verizons-critical-components-to-getting-sase-right/2022/11/
Security Service Edge vs. SASE: What Is the Difference?
Secure Access Service Edge (SASE) is a category of networking solutions defined by Gartner in 2019, which combines traditional network security functions with wide area networking (WAN) capabilities. The goal of SASE is to provide secure and reliable connectivity for users and devices, regardless of their location or the type of network they are connected to.
Gartner defines SASE as a cloud-delivered, network security as a service platform that provides secure network connectivity and network security functions in a unified offering, delivered through a common infrastructure and management. SASE combines network security functions, such as zero trust networking, firewalls, and intrusion prevention systems (IPS), with cloud-based networking services like SD-WAN (software-defined wide area networking) and internet connectivity.
……………………………………………………………………..
Secure Services Edge (SSE) is a set of integrated, cloud-delivered secure services that use identities and policies to establish secure connections between authenticated users and business resources. First introduced by Gartner in 2021, SSE is a security category that will secure connectivity in the future of hybrid environments and remote work.
As more employees work outside corporate boundaries, SaaS applications become the norm, and applications move to the public cloud, organizations cannot continue to backhaul user traffic to corporate networks. Many IT organizations are replacing their existing network security appliances, such as firewalls, VPN gateway appliances, and web gateways, with cloud-based options that can better protect data, provide a better user experience, and reduce costs.
SSE platforms provide cloud services that extend secure connectivity to user locations, without connecting users to corporate networks, exposing IT infrastructure to the public internet, or requiring complex network segmentation. Instead, SSE allows IT to provide secure access from anywhere to on-premise applications, secure access to the internet, and fast access to the cloud and SaaS applications.
………………………………………………………………………………………..
Security Service Edge vs. SASE: What Is the Difference?
The main difference between Secure Access Service Edge (SASE) and Security Service Edge (SSE) is the focus of the solutions. SASE combines traditional network security functions with wide area networking (WAN) capabilities, while SSE focuses specifically on security functions.
SASE solutions are designed to provide secure and reliable connectivity for users and devices, regardless of their location or the type of network they are connected to. This can include traditional networking functions like VPNs and SD-WAN (software-defined wide area networking), as well as security functions like firewalls, intrusion prevention systems (IPS), and other controls. SASE solutions are often used by organizations with remote and hybrid workforces to ensure secure access to corporate resources and protect against cyber threats.
https://wire19.com/security-service-edge-vs-sase-difference/