Session Border Controllers
Tutorial: Utilizing Containers for Cloud-Native and Elastic SBCs
by Bhupen Chauhan (edited by Alan J Weissberger)
Introduction:
A recent advancement in Session Border Controllers (SBCs) involves moving them to the cloud and utilizing elasticity. The use of Containers (defined below) intensifies this change even more. SBC solutions are essential for businesses. Service providers depend on Voice over IP (VoIP), because they provide security, interoperability, quality, and compliance in their communication infrastructure. We’ll delve further into the world of Cloud Native/Elastic SBCs using containers in this post.
What is a SBC?
A Session Border Controller (SBC) is a specialized hardware device or software program that controls how phone calls are answered, carried out, and ended as VoIP. They act as gatekeepers between internal and external networks, managing the media streams and signals necessary for establishing, carrying out, and terminating calls.
A SBC establishes and keeps track of each session’s quality of service (QoS) state, guaranteeing calls must be answered correctly, and urgent calls take precedence over all other calls. Additionally, an SBC can act as a firewall for session traffic by enforcing its QoS policies and recognizing particular inbound threats to the communication environment.
SBC’s Significance in Communications:
By providing security, guaranteeing interoperability, and enabling the effective use of network resources, SBCs strengthen communication networks. Here are several reasons to have Session Border Controller in VoIP Phone System and protect IP communications, defending against intrusions and offering essential functions, including:
- Security: An SBC’s most important responsibility is to defend the network against hostile assaults, including fraud, eavesdropping, and denial of service (DoS) attacks. They add a layer of security by concealing the network topology.
- Quality of Service (QoS): SBCs ensure that voice calls have the capacity and resources to remain high-quality by prioritizing voice traffic over other kinds of traffic.
- Interoperability: SBCs provide smooth communication between various devices, protocols, and signaling in IP networks by offering the required protocol translations.
- NAT Traversal: VoIP communication may encounter problems due to Network Address Translation (NAT). By fixing NAT traversal issues, SBCs guarantee reliable and continuous communications.
- Call Routing and Policy Enforcement: SBCs effectively route calls according to rules and specifications. They can also control bandwidth usage and implement various payment methods.
- Regulatory Compliance: Communication service providers are required in some areas to offer the ability to intercept communications legally. SBCs help VoIP service providers in fulfilling these kinds of legal obligations.
- Media services: Comprise functions like tone production, DTMF (dual-tone multi-frequency) interworking, and transcoding (changing one codec to another).
SBCs are essential to today’s communications environment, particularly regarding IP-based voice and video communications. Cloud-based and elastic SBCs will play a more significant role as communications change and more services go to the cloud. Now, we will together understand the concept of Cloud Native and Elastic SBCs.
What are Cloud Native and Elastic SBCs?
A strategy for developing and executing programs that takes advantage of the cloud computing concept is known as cloud-native. Conversely, Elastic SBCs describe a system’s capacity to adjust automatically to variations in workload by allocating and releasing resources.
Traditional SBCs and Cloud Native/Elastic SBCs are different as we now explain.
Traditional SBCs vs. Cloud Native/Elastic SBCs:
Traditional SBCs lack flexibility and are usually hardware-based. They might be expensive and difficult to expand or change. In comparison, Cloud Native/Elastic SBCs are highly adaptable. They provide cost-effectiveness and agility by effortlessly scaling up or down in response to demand.
Elasticity’s Function in Communication Services:
Elasticity guarantees continuous communication services that can adjust to heavy demands, particularly during peak hours. It implies that networks may scale resources without human intervention, ensuring service quality without taxing the infrastructure or adding needless expenses.
………………………………………………………………………………………………………………………………………
What are Containers?
Containers are small, independent, executable software packages containing all the necessary components to run a piece of software, guaranteeing that it performs consistently in various computing settings.
Function of Containers in the Modern Applications Deployment:
Containers offer an unequaled level of consistency and speed, revolutionizing how programs are delivered. They contain an application and all its dependencies, guaranteeing that it functions the same everywhere it is deployed.
Kubernetes and Docker:
Docker technology creates, transports, and operates applications inside containers. Meanwhile, Kubernetes’s container orchestration technology ensures that massive container deployments are effectively scaled and managed.
The Research and Markets predicts the global Kubernetes market is anticipated to expand significantly, rising from USD 1.8 billion in 2022 to USD 7.8 billion by 2030, with a spectacular Compound Annual Growth Rate (CAGR) of 23.4%
Use of Containers in SBCs:
SBCs benefit from unrivaled scalability, flexibility, and agility thanks to containers. They enable rapid deployments, guarantee consistency across many environments, and dramatically cut overall overheads—financially and in terms of time. Using Containers involves:
- Individual micro-services package and deploy using containers such as Docker. It guarantees scalability, isolation, and effective resource use.
- It can easily update services, rolled back, and versioned.
Architectural Considerations for Creating Cloud-Native Applications:
Scalability, Redundancy, Resilience, and Performance considerations are crucial when constructing Cloud Native/Elastic SBCs with containers. Architectures must be modular, and facilities must be made for smooth upgrades and patches that don’t interfere with running services. The following architectural factors should be taken into account while creating and deploying Cloud Native/Elastic SBCs using containers:
Disentanglement of Elements:
- Conventional SBCs frequently integrate several features into a single monolithic system.
- Micro-services design, in which every function (signaling, media processing, transcoding, security, etc.) is a separate, independent service, is the best way to create cloud-native SBCs.
Coordination:
- Containerized SBC micro-services can be managed and orchestrated by tools such as Kubernetes, which guarantees their efficient scheduling, scaling, and maintenance.
- Consider putting service mesh technologies into practice for enhanced traffic management and security.
State Administration:
- Active call sessions require careful management.
- Consider utilizing state full sets in Kubernetes or distributed databases to maintain a session state.
High Redundancy and Availability:
- Should guarantee redundancy over several zones or regions Via cloud-native design.
- Incorporate self-healing procedures and health checks to ensure uninterrupted service availability.
Converting SBCs to a containerized, cloud-native architecture has benefits for maintainability, scalability, and flexibility. However, careful architectural considerations are necessary to guarantee cost-effectiveness, security, and performance.
Containers Networking for Real-Time Communication:
The networking element of containers is essential in the area of real-time communication. It guarantees seamless switching between media streams, satisfies low-latency specifications, and ensures that Quality of Service (QoS) standards.
Elastic and Cloud Native SBC Security and Compliance:
SBCs play a crucial role in addressing security. Strong security measures are required for Cloud Native/Elastic SBCs to thwart threats, prevent unwanted access, and guarantee data privacy. They must also adhere to industry norms and laws to ensure reliable communication connections.
Prospects for the Future and the Changing Scene for Cloud Native SBCs:
SBCs will likely interact more deeply with cloud ecosystems in the future, utilizing AI and machine learning to provide more innovative and adaptive features. To support developing IoT and 5G use cases, edge computing may also play a more significant part in Cloud Native SBCs.
Conclusions:
A significant improvement in the evolution of network security and telecommunications has been realized cloud-native and elastic principles and the power of containers. This new paradigm is poised to completely reshape communication networks in the future since it provides agility, scalability, and efficiency. As we embrace containerization and the cloud, the possibilities are endless, opening the prospect of a more efficient, safe, and networked world.
References:
Session Border Controller (SBC) for Enterprises and VoIP Service Providers
Session Border Controller (SBC) for Enterprises and VoIP Service Providers
by Nellie Marteen
Introduction:
If you are new to Unified Communications (UC), it could be challenging to learn its many components. Some acronyms could be confusing. For example, SBC- Session Border Controller.
SBC is a network element used to protect Session Initiation Protocol (SIP) based VoIP (most enterprises use VoIP as the telephony service over the Internet). SBC may be deployed in the enterprise/customer premises (see Figure below), the VoIP carrier network or in the cloud as discussed later in this article.
SIP is used to initiate, maintain, and pause the working of VoiP and SIP services. The primary purpose of SBC is to enhance connectivity and address safety problems. However, some companies do not use SBC despite knowing its many benefits.
……………………………………………………………………………………………………………………………………………..
SBC in the enterprise/customer premises is shown in this Figure:
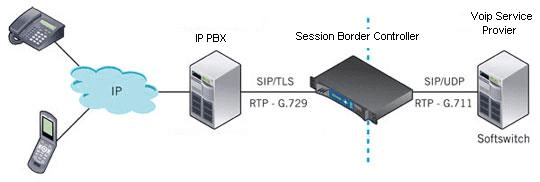
…………………………………………………………………………………………………………
Advantages of using SBC:
1. Quality of Calls
Session Border Controller can enhance call quality and provide ease of use. SBC enables the IP Private Branch Exchange (PBX) to be placed on the LAN among a separate IP address. They can do significant things such as normalizing hosted PBX signaling between the PBX as well as the service provider and providing critical routing capacities.
SBCs also assure interoperability of VoIP and video gadgets, examine VoIP lines, analyze call quality, and many more to name. SBC is a must if you get complaints about dropped or missed calls, reduced call quality, or both.
2. Connectivity
The primary function of SBC is to connect a company’s communications infrastructure to the hosted PBX service providers, private vendor network, and public internet. Additionally, SBCs have various essential roles, such as maintaining and securing networks.
An organization can save time and money by using SBCs. They can easily route their phone traffic via internal IPs rather than conventional circuit switched phone networks. Organizations can route phone calls instantly without paying for individual, traditional phone lines.
3. Safety
This is the benefit that many companies do not recognize. If a SBC recognizes a potential security threat, it can instantly remove/block that problem. After spotting the threat, it will alert the host computer(s) with the threat details and the protocols applied to normalize it. Also, SBCs can send the threat date to other businesses’ branches to look out for the same security breach. IT teams can be aware and utilize the data to look out for future security threats.
4, Mitigation of DoS Attacks and Continuity of Service
SBCs use pattern recognition technology to find unusual activities like a strange traffic surge while a DoS (Denial of Service) attack [1.] is ongoing. DoS strikes can take down entire networks resulting in unexpected downtime. Firewalls are generally not sufficient to prevent DoS attacks.
SBCs decrease threats and defend business communication systems from DoS attacks. DoS strikes can interpret phone and video conferences and steal important information or infect systems with malware and viruses. And if the system gets down due to a DoS attack, the organization may have to suffer for an unknown amount of time.
You can watch a short video on how SBCs detect and defend against DoS attacks.
Note 1. A denial-of-service (DoS) attack occurs when legitimate users are unable to access information systems, devices, or other network resources due to the actions of a malicious cyber threat actor. The most common method of attack occurs when an attacker floods a network server with traffic. In this type of DoS attack, the attacker sends several requests to the target server, overloading it with traffic. These service requests are illegitimate and have fabricated return addresses, which mislead the server when it tries to authenticate the requestor. As the junk requests are processed constantly, the server is overwhelmed, which causes a DoS condition to legitimate requestors.
5. Security
Hackers and other bad actors have found new ways to interrupt business communications services and upgrade their ways to disrupt older security measures. Here, SBCs take care of the protection. It is crucial to have up-to-date methods supported. Additionally, an extra layer of security from SBCs are crucial to safely maintaining VoIP solutions.
SBC Challenges:
SBC can be a complex piece of technology – one that demands a certain amount of expertise to set up and maintain. It is not a set-and-forget technology; as additions, moves and changes of voice service occur, the SBC must be configured to recognize them. Also, the IT department must actively manage SBC devices adding to their workload.
Who controls the session border?
For the enterprise, it is obviously desirable to be able to secure network connections, so their IT department should manage the SBC. Yet the VoIP carrier — whose network is being connected to — is also concerned about such things as QoS, lawful intercept of voice traffic and management of the voice connection.
For these reasons, communications carriers who offer VoIP connectivity often want to manage the session border controller or specify the controller that the enterprise will use. This is clearly at odds with an enterprise that wants to mask its internal networks from external intrusion. SBC, from the standpoint of the carrier, breaks the end-to-end management of call completion and complicates regulatory obligations such as access to 911 services and call intercept.
SBC in two VoIP carrier networks is depicted in this diagram:

Complicating this situation is the introduction of cloud-based session control. In this scenario, the SBC functionality is provided through a cloud service. Advantages are that the enterprise can offload a great deal of the management overhead associated with SBC maintenance. The drawback is that VoIP traffic latency can increase dramatically as it transits a much larger network.
Conclusions:
We have described and detailed all the significant benefits of SBC in this article, along with the challenges an IT department must deal with to effectively use SBCs. The important topic of whether the enterprise or carrier should control the session border was discussed along with cloud based session control.
It should be crystal clear that enterprises using VoIP should integrate SBC within their business communications system – either directly or via their VoIP service provider.
………………………………………………………………………………………………………………….
References:
https://www.voip-info.org/session-border-controller/
https://ribboncommunications.com/company/get-help/glossary/session-border-controller-sbc
https://www.ir.com/guides/a-complete-guide-to-session-border-controllers
https://us-cert.cisa.gov/ncas/tips/ST04-015
https://www.ecosmob.com/session-border-controller/#1
………………………………………………………………………………………………………………………..
About Nellie Marteen:
Nellie is also a blogger who writes about a variety of topics.



