SBC
Session Border Controller (SBC) for Enterprises and VoIP Service Providers
by Nellie Marteen
Introduction:
If you are new to Unified Communications (UC), it could be challenging to learn its many components. Some acronyms could be confusing. For example, SBC- Session Border Controller.
SBC is a network element used to protect Session Initiation Protocol (SIP) based VoIP (most enterprises use VoIP as the telephony service over the Internet). SBC may be deployed in the enterprise/customer premises (see Figure below), the VoIP carrier network or in the cloud as discussed later in this article.
SIP is used to initiate, maintain, and pause the working of VoiP and SIP services. The primary purpose of SBC is to enhance connectivity and address safety problems. However, some companies do not use SBC despite knowing its many benefits.
……………………………………………………………………………………………………………………………………………..
SBC in the enterprise/customer premises is shown in this Figure:
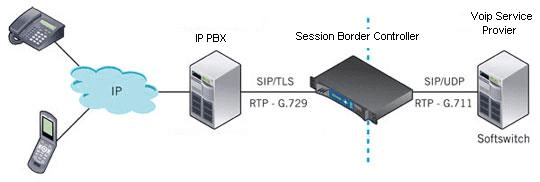
…………………………………………………………………………………………………………
Advantages of using SBC:
1. Quality of Calls
Session Border Controller can enhance call quality and provide ease of use. SBC enables the IP Private Branch Exchange (PBX) to be placed on the LAN among a separate IP address. They can do significant things such as normalizing hosted PBX signaling between the PBX as well as the service provider and providing critical routing capacities.
SBCs also assure interoperability of VoIP and video gadgets, examine VoIP lines, analyze call quality, and many more to name. SBC is a must if you get complaints about dropped or missed calls, reduced call quality, or both.
2. Connectivity
The primary function of SBC is to connect a company’s communications infrastructure to the hosted PBX service providers, private vendor network, and public internet. Additionally, SBCs have various essential roles, such as maintaining and securing networks.
An organization can save time and money by using SBCs. They can easily route their phone traffic via internal IPs rather than conventional circuit switched phone networks. Organizations can route phone calls instantly without paying for individual, traditional phone lines.
3. Safety
This is the benefit that many companies do not recognize. If a SBC recognizes a potential security threat, it can instantly remove/block that problem. After spotting the threat, it will alert the host computer(s) with the threat details and the protocols applied to normalize it. Also, SBCs can send the threat date to other businesses’ branches to look out for the same security breach. IT teams can be aware and utilize the data to look out for future security threats.
4, Mitigation of DoS Attacks and Continuity of Service
SBCs use pattern recognition technology to find unusual activities like a strange traffic surge while a DoS (Denial of Service) attack [1.] is ongoing. DoS strikes can take down entire networks resulting in unexpected downtime. Firewalls are generally not sufficient to prevent DoS attacks.
SBCs decrease threats and defend business communication systems from DoS attacks. DoS strikes can interpret phone and video conferences and steal important information or infect systems with malware and viruses. And if the system gets down due to a DoS attack, the organization may have to suffer for an unknown amount of time.
You can watch a short video on how SBCs detect and defend against DoS attacks.
Note 1. A denial-of-service (DoS) attack occurs when legitimate users are unable to access information systems, devices, or other network resources due to the actions of a malicious cyber threat actor. The most common method of attack occurs when an attacker floods a network server with traffic. In this type of DoS attack, the attacker sends several requests to the target server, overloading it with traffic. These service requests are illegitimate and have fabricated return addresses, which mislead the server when it tries to authenticate the requestor. As the junk requests are processed constantly, the server is overwhelmed, which causes a DoS condition to legitimate requestors.
5. Security
Hackers and other bad actors have found new ways to interrupt business communications services and upgrade their ways to disrupt older security measures. Here, SBCs take care of the protection. It is crucial to have up-to-date methods supported. Additionally, an extra layer of security from SBCs are crucial to safely maintaining VoIP solutions.
SBC Challenges:
SBC can be a complex piece of technology – one that demands a certain amount of expertise to set up and maintain. It is not a set-and-forget technology; as additions, moves and changes of voice service occur, the SBC must be configured to recognize them. Also, the IT department must actively manage SBC devices adding to their workload.
Who controls the session border?
For the enterprise, it is obviously desirable to be able to secure network connections, so their IT department should manage the SBC. Yet the VoIP carrier — whose network is being connected to — is also concerned about such things as QoS, lawful intercept of voice traffic and management of the voice connection.
For these reasons, communications carriers who offer VoIP connectivity often want to manage the session border controller or specify the controller that the enterprise will use. This is clearly at odds with an enterprise that wants to mask its internal networks from external intrusion. SBC, from the standpoint of the carrier, breaks the end-to-end management of call completion and complicates regulatory obligations such as access to 911 services and call intercept.
SBC in two VoIP carrier networks is depicted in this diagram:

Complicating this situation is the introduction of cloud-based session control. In this scenario, the SBC functionality is provided through a cloud service. Advantages are that the enterprise can offload a great deal of the management overhead associated with SBC maintenance. The drawback is that VoIP traffic latency can increase dramatically as it transits a much larger network.
Conclusions:
We have described and detailed all the significant benefits of SBC in this article, along with the challenges an IT department must deal with to effectively use SBCs. The important topic of whether the enterprise or carrier should control the session border was discussed along with cloud based session control.
It should be crystal clear that enterprises using VoIP should integrate SBC within their business communications system – either directly or via their VoIP service provider.
………………………………………………………………………………………………………………….
References:
https://www.voip-info.org/session-border-controller/
https://ribboncommunications.com/company/get-help/glossary/session-border-controller-sbc
https://www.ir.com/guides/a-complete-guide-to-session-border-controllers
https://us-cert.cisa.gov/ncas/tips/ST04-015
https://www.ecosmob.com/session-border-controller/#1
………………………………………………………………………………………………………………………..
About Nellie Marteen:
Nellie is also a blogger who writes about a variety of topics.


