Highlights of Light Reading’s White Box Strategies for Communications Service Providers (CSPs)
Abstract:
Network operators (like AT&T, Orange, SK Telecom, etc) and mega-web companies (like Linked In) are moving away from proprietary purpose-built hardware to “white box” solutions that are a mix of purpose-built software, or open source software running on generic compute server and/or Ethernet switch/IP router hardware. A “white box” is to be distinguished from a “bare metal switch” which does not come with any software.
It’s been said that white box networking offers greater flexibility and the potential for faster service delivery, but that’s yet to be proven. The transition from dedicated network equipment to generic white boxes is one part of the transformation process being undertaken by communications service providers and large enterprises as they seek greater efficiencies and new business opportunities.
The path to a white box world is complicated. In the past, the white box approach was only considered viable for enterprise networks, data centers and, in rare instances, the very edge of service provider networks. The latest iterations reach across vast swaths of wide area networks (WANs), right up to the carrier core, and the closer service providers get to an end-to-end, white box “white wash,” the higher the stakes become.
On November 17, 2015, Light Reading sponsored an excellent conference on “White Box Strategies for Communications Service Providers (CSPs).” We report the highlights in this post.
Key Points Made by CSPs:
Next up is the CORD Project for GPON network equipment disaggregation. CORD uses ONOS– an Open Source SDN operating system for service providers. Announced this past June, a CORD field trial will take place in Q1-2016. Mr. Duell described the project as “an open, virtualized service platform that provides cloud economics and agility. Think of it as “FTTH as a Service” consisting of hardware blueprints (schematics?) and open source software modules, Mr. Duell said.
Christos identified the opportunity to “create a marketplace for services and applications” including emerging Internet of Things (IoT) and marketing apps such as trading advertisements for free bandwidth to support video streams, as well as the ability to build customized products to the specifications of the service provider, as Google and others do today. All of that is enabled by separating hardware and software, and moving to more commodity-type, commercial-grade hardware built on merchant silicon that can rapidly scale and support innovation at the software layer. Not that getting to that stage will be easy, Kolias said.
Noting that the CSPs need “disaggregation, not disintegration,” he said there are significant integration challenges to achieving the same level of consistent performance using white boxes that exist today with purpose-built telecom gear.
– Breaking down the network gear
– Systems Integration/packaging options: ODM (h/w or s/w), 3rd party, end-user, or a combination thereof
– Accelerates product development to match evolving requirements
– DevOps ‒ continuous testing & integration
– The rise of the ISVs (Independent Software Vendors)
– White box switches and software switches
– Suitable for Data Centers, Enterprise, Cloud, potentially CSPs
As noted above, there are different approaches that network operators can take to address the systems integration (hardware, open source software, purpose built software, etc) challenge, the Orange executive said: CSPs can rely on hardware or software vendors for help, bring in third-party integrators, do their own integration, or combine those three approaches.
APIs are more critical than ever, Christos said. They are important for plug-n-play, especially for open platforms (Google, FB, Microsoft, eg, WebRTC). APIs provide: the “glue” in an open system, the integration points with existing systems (eg, OSS), the support points for the apps. APIs are essential for building developer communities.
– Standard & open APIs can enable and ensure interoperability and thereby lessen dependency risk
– They can enable plethora of innovative (eg, ad-hoc/customized) services and lead to new business models for the telcos
– Provide monetization opportunities (eg, consumers, enterprise, VNOs, etc)
Ashish Singh, SK Telecom’s GM/VP of products said the South Korean telco is transitioning from an ARPU business model to an Average Revenue Per Service model. SK Telecom is planning to use white box servers as part of a strategy to build “mini-modular data centers” for services at the edge to serve mobile computing needs, rather than sending data to a centralized data center.
The goal is to move intelligence closer to the edge of the network, to enable improved reliability, data protection and end-to-end encryption, Singh said. He added that IoT services via NFV (Network Function Virtualization) must provide: low latency, high reliability, processing that’s close to the user. He cited telemedicine as an example IoT application. At the mobile edge, SK Telecom is using Apache Spark for real time streaming video. Again, the objective is to push decision making to the network edge.
OPEX Savings or Problems?
I continue to believe that OPEX will be a key issue for white box networking because the white boxes won’t be as reliable as typical carrier class network equipmen. Furthermore, the hardware/software are from different vendors leading to a systems integration/fault isolation/finger pointing problem which will increase OPEX.
Key OPEX issues include: hardware/software integration, fault isolation and repair (fail-over and problem resolution), restoration/re-routing around failures or congested network nodes, integration with OSS/BSS, upgrades/updates to software which cause problems with other functions, etc.
Conclusions:
1. The AT&T and SK Telecom panelists said they are using the same infrastructure (network equipment) for both wireline and mobile subscribers via a new wireless access rack (not defined and no details provided).
2. While CAPEX for white boxes will be lower than purpose built networking gear, we think OPEX may be considerably more expensive (see section above). This point can only be proven or disproved several years after white box networks have been deployed in large volumes.
3.. A huge transition is underway for telcos – from a network operator offering a fixed set of services to a “platform service provider,” which permits new companies to build applications and business models that run on top of the network. Such new age CSP’s Comms will open their network and resources and build their own services on the platform, while also letting partners build services as well.
Comment: Haven’t we heard that line before? Like every other day for the last 15 years?
U.S. Wireline Telcos Step Up Gigabit and HIgher Internet Access vs Comcast Xfinity
Development and deployment of ultra-fast broadband is a continuing goal for major telecommunications carriers, responding to the demand for streaming video and other high-intensity bandwidth usage. For example, Verizon announced plans to test new broadband technology that would reportedly (link is external) provide download speeds of 10 gigabits per second. That would be 10 times faster than Google Fiber and 1,000 times the rate of the average U.S. home Internet connection.
As this Verizon video demonstrates, uploading 1,000 photos using this technology would take just two seconds and downloading a feature-length high definition movie would be completed in eight seconds. Verizon’s 10-gigabit Internet leverages next-generation passive optical network technology, known as NG-PON2, was discussed recently in this USTelecom webinar. The technology enables providers to upgrade the networks capacity by adding new colors of light onto the existing fiber, and is capable of ultimately increasing system capacity from 10 Gbps to 40-80 Gbps.
“The advantage of our FiOS network is that it can be upgraded easily by adding electronics onto the fiber network that is already in place,” according to Lee Hicks (link is external), vice president of network technology for Verizon. “Deploying this exciting new technology sets a new standard for the broadband industry and further validates our strategic choice of fiber-to-the-premises,” Hicks said.
AT&T is also is a key broadband provider with its GigaPower offering. The company has pledged to launch 1 Gbps fiber-to-the-home service to 23 new markets.
Fairpoint recently announced the company would launch gigabit Internet service in select New Hampshire markets.
Windstream’s CEO Tony Thomas has said the telco plans to introduce gigabit Internet in one market in 2015, with plans to expand this high-speed broadband offering in every one of its markets.
The capital and commitment of the nation’s telecom providers will continue to enhance and expand high-speed Internet offerings, supporting consumer demand and next-generation innovations.
See more at: http://www.ustelecom.org/blog/building-ultra-high-speed-internet#sthash.qoplPpWy.dpuf
In contrast to the above U.S. telcos, Comcast XFINITY® delivers the fastest Internet, now with download speeds up to 505 Mbps. That service is expensive- it cost $399.95 a month.
This author has AT&T U-verse High Speed Internet Max Turbo, which advertises download speeds of 18.1 Mbps -to- 24 Mbps. Several times, I’ve measured the download speed at the DSL modem which is usually around 23 to 24Mbps. However, the 802.11n WiFi router (which is bundled with the DSL modem) only provides a measured 16 Mbps to 18 Mbps downstream rate.
Hence, one must be very careful in determining what the downstream rate the user actually realizes. Misleading telco/MSO advertising is quite common!
IHS-Infonetics & Dell’Oro Group on Data Center SDN Market
1. SDN Data Center and Enterprise “In-Use” SDN Market Topping $1.4 Billion in 2015, IHS-Infonetics:
Data Center (DC) and enterprise LAN software-defined networking (SDN) deployments began to ramp in the first half of 2015 (1H15), reports IHS in its latest IHS Infonetics Data Center and Enterprise SDN Hardware and Software report. IHS forecasts the market for ‘in-use’ SDN Ethernet switches and controllers to top $1.4 billion this year, nearly doubling from last year.
“New SDN use cases continue to emerge, and the first half of 2015 was no exception with the establishment of the software-defined enterprise WAN (SD-WAN) market. The SD-WAN market is still small, but many startups and traditional WAN optimization appliance vendors and network vendors have jumped in,” said Cliff Grossner, Ph.D., research director for data center, cloud and SDN at IHS.
“The data center and enterprise LAN SDN market will be solidified by the end of 2016 as lab trials give way to live production deployments. And in 2017, SDN will move from early adopters into the hands of mainstream buyers,” Grossner said.
DATA CENTER / ENTERPRISE SDN MARKET HIGHLIGHTS:
· In the first half of 2015 (1H15), bare metal switches accounted for 45 percent of global in-use SDN-capable Ethernet switch revenue
· Looking at the leaders in individual SDN categories:
o White box switch vendors, as a group, are #1 in bare metal switch revenue
o Dell owns 100% of branded bare metal switch revenue
o HP has the largest share of SDN-capable (in-use and not-in-use) branded Ethernet switch ports
· In-use virtual switch (vSwitch) ports are expected to make up 11 percent of SDN (in-use and not-in-use) ports shipped by the end of 2015
· SDN in-use physical Ethernet switches are forecast by IHS to comprise 15 percent of Ethernet switch market revenue in 2017, up from 4 percent today

Data Center and Enterprise SDN Report Synopsis:
The biannual IHS Infonetics Data Center and Enterprise SDN Hardware and Software report provides worldwide and regional vendor market share, market size, forecasts, analysis and trends for SDN controllers, bare metal Ethernet switches and branded Ethernet switches in use for SDN. Notably, the report tracks and forecasts SDN controllers and Ethernet switches in-use for SDN separately from not-in-use SDN-capable Ethernet switches. Vendors tracked: Alcatel-Lucent, Arista, Big Switch, Brocade, Centec, Cisco, Cumulus, Dell, Extreme, HP, Huawei, Juniper, Lenovo, Midokura, NEC, Pica8, Plexxi, PLUMgrid, VMware, White Box, others. This report is part of the IHS Data Center Networks Intelligence Service.
To inquire about Intelligence Service subscriptions, please visit www.infonetics.com/contact.asp
RELATED RESEARCH
-
Operators Expect OPEX Reductions in 2nd Year of Data Center SDN Deployment
-
25GE Ports to Make Up 9% of Converged DC Network Adapter Market by 2019
-
Cloud Service Providers Reveal Preferences for DC Technologies and Vendors
TO PURCHASE RESEARCH, CONTACT:
IHS Sales: +1 844-301-7334
https://www.ihs.com/about/contact-us.html
2. DATA CENTER SDN MARKET FORECAST TO GROW OVER 70% IN 2015, ACCORDING TO DELL’ORO GROUP
Amazon AWS, Google, Microsoft Azure Drive 25 GE and 50 GE
REDWOOD CITY, Calif. – November 10, 2015
According to the new 2015 Data Center SDN Advanced Research Report from Dell’Oro Group, the trusted source for market information about the telecommunications, networks, and data center IT industries, the Software Defined Networking (SDN) Market is forecast to grow more than 70% in 2015, versus 2014. 2015 marked an important milestone in SDN, with many Ethernet Switch architectures ratified and production deployments under way.
“SDN’s impact on the Ethernet Switch market increased significantly in 2015 as deployments expanded beyond the large Cloud Providers,” said Alan Weckel, Vice President at Dell’Oro Group. “It is clear that, by 2020, data centers will look significantly different from today’s. We are already seeing an impact on the overall networking and IT markets as enterprise customer spend stagnates while spend from Cloud Providers such as AWS and Azure explodes. As we look towards next generation 25 GE and 50 GE server access we expect to see significant disruption amongst the vendors with Dell’s planned acquisition of EMC being a prelude to further market consolidation,” Weckel stated.
About the Report:
Dell’Oro Group’s Data Center SDN Advanced Research Report evaluates the data center network and identifies the equipment that will likely be impacted by SDN in the next several years, including Ethernet Switch, Application Delivery Controllers and Network Security Appliances. The Report also outlines the disruptive elements to the Ethernet Switch market in the data center, including SDN, Cloud, Virtualization, and the impact of White Box Switching.
The report also reveals vendor placement in the data center Ethernet Switch market including Arista, Brocade, Cisco, Dell, Hewlett-Packard, Extreme, Huawei, and Juniper.
To purchase this report, please contact Matt Dear at +1.650.622.9400 x223 or email [email protected].
About Dell’Oro Group:
Dell’Oro Group is a market research firm that specializes in strategic competitive analysis in the telecommunications, networks, and data center IT markets. Our firm provides in-depth quantitative data and qualitative analysis to facilitate critical, fact-based business decisions.
For more information, contact Dell’Oro Group at +1.650.622.9400 or visit www.delloro.com
http://www.delloro.com/news/data-center-sdn-market-forecast-to-grow-over…
Sprint's Response to T-Mobile's Free Video Streaming- 50% off Promo! David Dixon of FBR &Co.
On the heels of T-Mobile US’s Un-Carrier X free video streaming announcement last week to drive sales, this afternoon Sprint announced a simplified 50% off promotion to help drive higher sales volume, leveraging the improved network performance post the Network Vision upgrade and optimization.
The previous “Cut Your Bill in Half” promotion was difficult to execute due to grandfathered plans and discount complexities. The new plan is simplified in that it only applies to existing plans and includes a choice to maintain pricing. Management believes over 50% of switching customers will opt for a larger data plan at the same price versus a 50% cut, which should ease profitability concerns.
With LTE Plus now in 77 cities and numerous number one awards in RootMetrics in 2H15 testing (~108 awards),
management is wise to cut price now because perceived network quality remains poor, in our view. Over 50% of the base (and 100% of additions) leverage three spectrum bands (800 MHz, 1.9 GHz, and 2.5 GHz) to deliver higher download speeds. The company is confident the offer will generate sufficient volume to be accretive to earnings.
■ Offer details. The new 50% off promotion will apply to the current base service plan and access charges for any customer who switches from TMUS, T, or VZ and includes payment of up to $650 in early termination fees (which many customers keep despite the credit rating impact).
■ Contractual period. Lower pricing will be for 24 months and run until 2018. Existing Sprint customers can get a free Alcatel ONETOUCH PIXI 7 tablet with one year of free service (either a $15 per month, 1 GB plan or $10 per month Family Share Pack access) with any new two-year contract.
■ Plan exclusions. The promotion excludes the TMUS $90 unlimited plan as the Sprint $70 unlimited plan is already competitive and this would be dilutive.
■ Promotion timing. The promotion starts on November 20 until year end. The “test drive” period will last 28 days, after which the customer can either stay or leave Sprint without incurring restocking fees. ■ Our thoughts. Sprint needs to show greater sales momentum to ease the pace of revenue erosion. We think this should be accretive as incremental growth is high margin. This is a good window to exploit improved network performance post Network Vision upgrade and optimization. Sprint has been slow to pivot to a new network upgrade plan and is cash constrained, so we need to see acceleration in deployment.
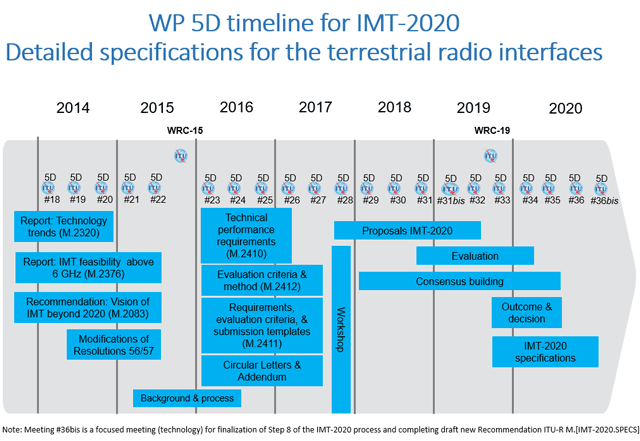
Activities of forums/ standards bodies contributing work to ITU-R 5G (IMT-2020)
Introduction:
1. NGMN
2. Asia-Pacific Telecommunity
3. Telecommunication Technology Committee (TTC)
Recently, TTC FMN-Ad Hoc finalized a “TTC White Paper on Future Mobile Networking” and attached it to this contribution.
TTC recognizes that ITU-R Working Party 5D focuses mainly on radio part, however, TTC hopes our White Paper can provide useful information for developing “5G” mobile network in WP 5D.
4. Industrial Technology Research Institute, Inc. (ITRI)
ITRI has started a 5G project that includes the research and development of mmWave, SDN/NFV, and Ultra-Dense Network technologies. We plan to create a channel model generator and simulator for mmWave. An ultra-dense small cell network will be established at ITRI with the capability to interconnect a remote testbed for joint testing. We will also develop big data analytics for intelligent IoT and mobile broadband on high-speed moving network applications. Recognizing the importance of international collaboration ITRI is cooperating with the European Union on access convergence taking advantage of 5G research results and testbeds at ITRI. An SDO was established recently to enhance our contributions in standardization of “IMT-2020” systems. The above effort is consistent with ITU-R’s vision, capabilities, and technology trends.
5. Fifth Generation Mobile Communications Promotion Forum (5GMF)
5GMF was established in September 2014 to conduct research & development concerning the fifth Generation Mobile Communications Systems, and research and study pertaining to standardization aimed at the early realization of the Fifth Generation Mobile Communications Systems.
This section includes responses that were included in Doc. 5D/991 from the 5G Forum and ETRI. To respond the request of ITU-R WP 5D, TTA circulated the liaison statement to our members and related organizations in Korea. As a result, two replies from 5G Forum & ETRI were received as shown in attachment, which describes the activities update of each organization.
7. Activities Update of 5G Forum
5G Forum was established on 30 May 2013 in Korea as an open forum with a vision of “Global leadership and promotion in 5G mobile communication toward 2020”
Around 30 member organizations from operators, vendors, academia and public organizations from domestic and international players are actively participating in 5G Forum activities.
In 5G Forum, 5 sub committees (Global Strategy, Convergence & Services, Spectrum, Wireless Technology, and Network Technology) are responsible for:
As an outcome of global collaboration, 5G Forum signed MoU with 5GPPP of Europe, IMT-2020 PG of China and 5GMF of Japan and had discussions with other bodies as well.
8. Activities Update of 5G R&D from ETRI
ETRI is leading two important national 5G projects, namely, Quadruple-Thousands (QK) 5G and Giga Korea (GK) 5G projects.
9. Wireless World Research Forum (WWRF)
- 5G PPP is a research program in Horizon 2020 of the EU dedicated to 5G system research
- Research program is addressing all building blocks of a futurecommunication network and a huge number of huge cases fromvertical sectors
- 5G Infrastructure Association vision paper publishedat Mobile World Congress 2015 in Barcelonahttp ://5g-ppp.eu/wp-content/uploads/2015/02/5G-Vision-Brochure-v1.pdf
- First set of projects started on July 1, 2015
- PPP Program that will deliver solutions, architectures,technologies and standards for the ubiquitous 5Gcommunication infrastructures of the next decade
- Providing 1000 times higher wireless area capacity and more variedservice capabilities compared to 2010•
- Saving up to 90% of energy per service provided.
- The main focus willbe in mobile communication networks where the dominating energyconsumption comes from the radio access network• Reducing the average service creation time cycle from 90 hours to 90minutes•
- Creating a secure, reliable and dependable Internet with a “zeroperceived” downtime for services provision
- Facilitating very dense deployments of wireless communication linksto connect over 7 trillion wireless devices serving over 7 billion people
- Enabling advanced User controlled privacy
More info at:
https://5g-ppp.eu/wp-content/uploads/2015/10/Taiwan-EU-Workshop_ICT2015-Lisbon_5G-PPP_Werner-Mohr.pdf
International:
- ITU-R Visions Group
EU
• Framework Program 7, e.g. METIS and 5GNow projects
• 5G PPP in Horizon 2020
Germany – 5G Lab Germany at TU Dresden
UK – 5G Innovation Centre (5GIC) at University of Surrey
US
• Intel Strategic Research Alliance (ISRA)
• NYU Wireless Research Center
• 4G Americas, MoU – signed
China
• 863 Research Program
• Future Forum
• IMT-2020 (5G) Promotion Group, MoU – signed
Japan – The 5G Mobile Communications Promotion Forum, MoU – signed
Korea – 5G Forum, MoU – signed
Taiwan – TAICS, Ministry of Science and Technology, Ministry of Economic Affairs
Russia – 5GRUS by Russia’s Icom-Invest
CJK White Paper
NGMN – White paper on future requirements
Ericsson-Cisco partnership for "networks of the future" stops short of a merger
On Monday, Ericsson and Cisco announced a multi-faceted partnership to create the networks of the future – and through this, shape the direction of the industry. Ericsson, a leader in wireless network equipment, and Cisco, which dominates the market for Internet gear, will work together to integrate existing equipment. They will combine some sales and consulting efforts and, ultimately, may jointly develop entirely new hardware and services.
Both companies have invested a lot of time in designing this partnership over the past year, according to Ericsson’s CEO (see quote below).
Cisco brings their leading position in IP and a strong presence in enterprise. Ericsson brings leadership in mobile networks, strength in global services, and strong relationships with the world’s leading service providers.
Ericsson and Cisco together hold more than 56,000 patents, invest $11 billion annually in research and development, and operate more than 76,000 services professionals serving customers in more than 180 countries.
Hans Vestberg, President & CEO of Ericsson:
“The strength of this partnership lies not just in its scale, but in the depth of the solutions Ericsson and Cisco can now provide to the networking market. It is a market in transition – increasingly mobile, cloud-based, and digital – and customers are seeking end-to-end solutions to reach their full potential. We have evaluated the impact of acquisitions, our own development, and other strategic opportunities – and this partnership is by far the best way forward. We believe that this partnership will create the most value both for our customers and for Ericsson and Cisco.
For Ericsson, this partnership also fortifies the IP strategy we have developed over the past several years, and it is a key step forward in our own transformation. It will start generating revenues for Ericsson as soon as 2016, ramping up to USD 1 billion by 2018 and building from there.”
Both companies are coping with challenges that include a slowdown in the smartphone market, a longtime driver of revenues for the telecom companies that are their biggest customers. They also face heightened competition from Huawei, as well as a new threat created by the pending €15.6 billion ($16.8 billion) takeover of Alcatel-Lucent SA by Nokia Corp. Those rivals have expertise in both wireless and Internet technologies, a combination that Cisco and Ericsson hope to now match, said Pierre Ferragu, an analyst at Sanford C. Bernstein.
At the same time, the deal underscores a widening recognition of the downsides of large mergers, particularly cross-border transactions that can face regulatory scrutiny in many countries.
“Neither Ericsson or Cisco really believe that these large mergers typically work,” Chuck Robbins, Cisco’s chief executive, said in an interview.
Analysts don’t expect formal reviews by antitrust authorities, but politicians on both sides of the Atlantic may take a close look. Governments have been eager to closely monitor suppliers of equipment regarded as highly sensitive for security and privacy reasons. Huawei has been essentially shut out of the U.S. market after a congressional report deemed it a risk to national security.
For Ericsson, the alliance could help retain its position as the world’s biggest telecom-equipment supplier by sales, just as its Nordic rival Nokia regains strength. Nokia’s takeover of Alcatel-Lucent could create a powerful challenger to both Ericsson and Cisco.
To find new revenues, analysts said, Cisco and Ericsson must develop new products to cope with changes in the networks operated by mobile and wireline carriers—as well as exploit a trend called the “Internet of Things,” which will connect more everyday devices to one another.
The other problem is Huawei, which recently overtook Ericsson in the market for mobile infrastructure equipment, according to analysts at Dell’Oro Group. Huawei received 30% of revenues in that market during the first half of 2015, according to the research firm, compared with 27% for Ericsson and 25% for the combination of Nokia and Alcatel-Lucent.
Ericsson’s core business of supplying equipment has suffered from price competition and from the relatively slow rollout of broadband wireless networks, known by the acronym 4G, by its carrier customers.
Cisco also faces pressure from Huawei. Dell’Oro estimates that the Chinese company accounts for 13% of the global router business—Cisco has 49%—but Huawei has displaced Cisco as No. 1 in China.
In the short term, one benefit of the alliance is for Ericsson to resell Cisco networking gear. The Swedish company also has 65,000 service personnel that help advise carriers on how to build networks. Cisco, which has 11,000 service workers, can take advantage of the Ericsson staff, Mr. Robbins said.
Ericsson, which has around 116,240 employees, reported revenue last year of 228 billion Swedish kronor ($26.3 billion). Cisco, which employs 70,000 people, reported revenue of $49.2 billion in its latest fiscal year, which ended in July.
The companies sell some competing equipment, but the overlap is small. Cisco accounted for 1% of the wireless infrastructure market in the first half, while Ericsson accounted for 1% of the routing market, Dell’Oro Group estimates.
An added wrinkle of the partnership concerns patents. Ericsson, a wireless pioneer, claims 37,000 patents to Cisco’s 19,000. The companies said they expected to complete a patent cross-license agreement under which Cisco would pay an unspecified amount to Ericsson for use of its patents.
From Fortune on line magazine:
What exactly the partnership will do is obscured by scores of words of gobbledygook (that’s a technical term) issued by both companies. These refer to a “multifaceted relationship” focused on “networks of the future” that will facilitate the cross-selling of both companies’ “end-to-end product and services portfolio.” (Fortune’s Jonathan Vanian has details here.)
The companies weren’t prepared to discuss much about the commercial nature of their “non-deal deal.” They said neither company is taking an ownership position in the other, but they predict the combination will result in incremental revenues of $1 billion to each company by 2018.
There was one concrete type of reference to money: Cisco is paying Ericsson a licensing fee for the use of its patents. Cisco’s stock declined a bit, and Ericsson’s rose about the same amount, percentage-wise.
Rather than merging and all the headaches that would ensue, they reached multiple agreements, terms undisclosed, to work more closely together. Centerview Partners, an investment bank, advised on the partnership, according to a news release. That means money is involved.
Why be so cryptic? The kinds of equipment Ericsson and Cisco sell tend to make governments nervous. Nervous governments like to bless mergers before they happen. No merger, no blessing, no problem.
Fortune’s Stacey Higginbotham has a different take on this deal.
The partnership comprises a series of agreements spanning everything from reselling and joint sales, to technology cross-licensing, co-innovation and joint professional services, and should it aims at boosting each company’s annual revenues significanly.
“Given Ericsson’s annual revenues of more than USD26 billion and Cisco’s of more than USD49 billion, and opportunities in new enterprise-driven communications and IoT services, we think each company’s goal of driving USD1 billion in new revenues by 2018 based on this strategic partnership is achievable,” said Dana Cooperson, Research Director at global telecoms specialist Analysys Mason
Ericsson’s nearly USD5 billion and Cisco’s over USD 0.7 billion in telecom software professional services is one possible area ripe for growth.
The agreement is described by analysts as an aggressive move positioning Ericsson and Cisco against competitors, like Huawei, HP, and Nokia –Alcatel-Lucent , for dominance as the partners of choice for communication service providers that want to become digital service providers as well.
In fact, the announcement was well received by several high-profile executives of companies like Vodafone , AT&T and Verizon. For Robert Gurnani, Verizon’s Chief Information and Technology Architect, it even “has the potential to reshape the industry.”
However, according to Cooperson, to make the agreement work, the Swedish and American multinationals will have to abide to certain preconditions. Their ability to pre-integrate solutions based on a common, robust, architecture will have to be of sufficient value in time and money to be compelling to customers.
Clients will need to be comfortable that Ericsson and Cisco are not just strengthening their leading positions in mobile infrastructure, professional services and IP infrastructure to create de facto lock-in. Finally, “the companies will need to show that they are not too big to move quickly to create joint solutions,” Cooperson said.
OPEX Reductions Expected in 2nd Year of Data Center SDN Deployment- why not?
Introduction:
IHS-Infonetics conducted in-depth interviews with service providers that have deployed or plan to deploy or evaluate software-defined networking (SDN) by the end of 2016. They discovered that 85% of survey respondents expect data center network operating expenses (OPEX) to decrease significantly by the second year of SDN deployment.
Author’s note: Of course, that was one of the driving forces behind moving to SDN in the first place!
“Service providers expect SDN to deliver a positive return on investment. Our data center SDN study found that providers expect significant OPEX cost reductions within two years of deploying SDN. CAPEX reductions are also expected, and respondents acknowledge they need to invest in equipment and operational processes to get started with SDN,” said Cliff Grossner, Ph.D., research director for data center, cloud and SDN at IHS. “In supplying SDN to service providers, open source vendors have the largest opportunity with orchestration software and applications,” Grossner added.
DATA CENTER SDN SURVEY HIGHLIGHTS:
· Service provider respondents named Cisco, Alcatel-Lucent/Nuage and VMware as top SDN vendors. Note that none of those use the pure SDN/Open Flow model!
· Service providers that are scaling up their data centers—investing significant CAPEX in physical servers and virtualization technology—are most likely to deploy SDN
· Expectations for SDN are clear: simplified network provisioning, network automation, rapid application deployment and interoperability with existing equipment
· The top data center SDN use cases among operators surveyed are a cloud architecture for the data center, automated application deployment and hybrid cloud.

DATA CENTER SDN SURVEY SYNOPSIS:
For the 35-page 2015 IHS Infonetics Data Center SDN Strategies: Global Service Provider Survey, IHS interviewed purchase-decision makers with detailed knowledge of their organization’s data center SDN plans and strategies about plans to evolve their data centers and adoption of new technologies over the next two years. Respondents were asked about SDN deployment drivers, barriers and timing; expected CAPEX and OPEX changes with SDN; use cases; switching technologies; applications; vendors; and more.
To purchase research, please visit:
www.infonetics.com/contact.asp
RELATED RESEARCH
-
Bare Metal Switches a $1 Billion Market by 2019, Software-Defined WAN Rising
-
Storage Area Network Market Declining as Off-Premise Cloud Services Rise
-
Enterprises Plan to Spend 1/3 of IT Budget on Off-Premise Cloud Services by 2016
-
Cloud Services for IT Infrastructure and Applications to Top $230 Billion by 2019
-
Carriers on Track to Spend $5.7B on SDN Hardware, Software & Services by 2019
-
Network Operators Reveal SDN Plans, Timing & Challenges in New Survey
References:
http://press.ihs.com/press-release/technology/operators-expect-opex-reductions-2nd-year-data-center-sdn-deployment
Raj Jain, PhD: The key characteristics of SDN are programmability that allows policies to be changed on the fly. This allows orchestration (ability of manage a large number of devices), automation of operation, dynamic scaling, and service integration. Combined with virtualization, this also allows multi-tenancy and all of the above benefits to individual tenants as well.
It is important to know what SDN is not. SDN is not separation of control and data plane or centralization of control or OpenFlow. These are all one way to do SDN but alternatives are equally good. Networks can be programmed and policies can be changed without separation of data and control plane, without centralization of control, and without OpenFlow.
http://www.jisajournal.com/content/6/1/22
http://www.prnewswire.com/news-releases/sdn-to-drive-down-service-provider-capex–opex-heavy-reading-finds-246142961.html
http://sites.ieee.org/sdn4fns/files/2013/11/SDN4FNS_panel_presentation_Bram_Naudts.pdf
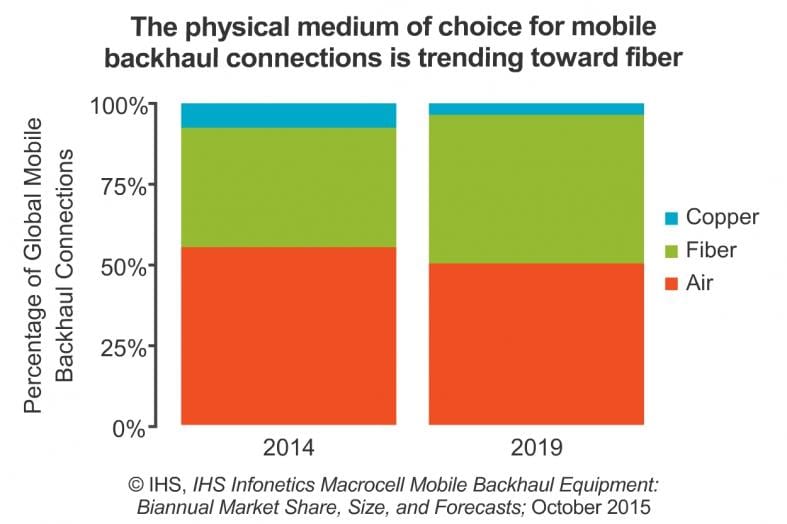
IHS-Infonetics Report: Microwave Radio still dominates Mobile Backhaul but Fiber Increasing
The recently released IHS Infonetics Macrocell Mobile Backhaul Equipment report tracks equipment used to transport mobile traffic. In the report, IHS Technology forecasts a cumulative $45 billion to be spent on macrocell mobile backhaul equipment worldwide over the 5 years from 2015 to 2019.
MOBILE BACKHAUL MARKET HIGHLIGHTS:
· Worldwide macrocell mobile backhaul equipment revenue declined slightly (-0.6 percent) in 2014 from 2013, to $8.5 billion
· Demand remains solid from LTE deployment, 3G network expansion and backhaul capacity enhancement, but increasing pressure on equipment pricing is inhibiting revenue growth
· IP/Ethernet clearly remains the driver of the mobile backhaul equipment market, required to do the heavy lifting for ever-growing mobile bandwidth usage
· Microwave radio was the largest spending category in 2014, at 47 percent of global mobile backhaul gear revenue, though this segment is projected to decline as more fiber and wireline Ethernet come into play
· Toward 2019, 5G backhaul demand starts to drive the market, pushing the microwave segment back to modest year-over-year revenue growth
Analyst Quote:
“While the market has experienced something of a plateau of late as many operators are approaching late-phase LTE deployment having already upgraded their backhaul, renewed growth is definitely on the horizon,” said Richard Webb, research director for mobile backhaul and small cells at IHS. “Developing countries later to the LTE party, such as India, will drive steady growth over the next few years, which will gain extra momentum from early 5G adopters.”
MOBILE BACKHAUL REPORT SYNOPSIS:
The biannual IHS Infonetics Macrocell Mobile Backhaul Equipment report provides worldwide and regional market share, market size, forecasts through 2019, analysis and trends for macrocell mobile backhaul equipment, connections and installed cell sites by technology. Companies tracked: Accedian, Actelis, Adtran, Adva, Alcatel-Lucent, Aviat Networks, Canoga Perkins, Ceragon, Ciena, Cisco, DragonWave, E-band, Ericsson, FibroLan, Huawei, Intracom, Ipitek, Juniper, MRV, NEC, Overture, RAD, SIAE, Telco Systems, Tellabs, ZTE, others. To purchase research, please visit www.infonetics.com/contact.asp.
WEBINAR: SDN AND NFV FOR SMALL CELLS AND BACKHAUL:
Join analyst Richard Webb Oct. 29 at 11:00 AM ET for Leveraging SDN and NFV for Small Cells and Backhaul, an event examining the challenges and opportunities for combining SDN and NFV in the backhaul network. Register here.
RELATED RESEARCH:
- NEC and Alcatel-Lucent Claim Lead in IHS Microwave Equipment Scorecard
- Plateau for Microwave Equipment Market until 5G Gets Underway in 2017
- Operators Forging Ahead with SDN in Macrocell Backhaul Networks
- Mobile Backhaul Market Plateau Will Be Short Lived, IHS Says
- Mobile Operators Turning to Ethernet Microwave for Voice and Data Backhaul
Verizon Petitions FCC to provide Wi-Fi calling with TTY waiver
Verizon is taking steps to enable Wi-Fi voice on its wireless network. The carrier has submitted a petition to the FCC requesting that the regulatory body grant it a waiver identical to the one it gave to AT&T earlier this month for WiFi calling without TTY service.
Enabling Wi-Fi voice calling is problematic for the FCC, because the underlying technology doesn’t reliably support TTY (teletypewriter), a decades-old service used by the hearing impaired. AT&T complained to the FCC last month that competitors T-Mobile and Sprint merely disregarded the rules around TTY support when they launched Wi-Fi calling.
Verizon plans to research and deploy RTT (real-time text) technology, a successor to TTY. However, the company maintains that it’s not ready to roll out the technology across its network just yet. It hopes to do so during the period that its requesting the waiver for—through 2017, or the same length of a waiver that AT&T was granted.
“Verizon plans to meet the same conditions enumerated in the AT&T Waiver Order. Specifically, Verizon agrees to inform its customers through multiple channels that TTY is not supported on these services for calls to 911 and inform customers of alternative means to reach 911 services. Verizon will also inform the Commission and customers of its progress toward the deployment of RTT as described in the AT&T Waiver Order. And Verizon is seeking a waiver for the same duration as that granted to AT&T,” according to Verizon’s petition.
“Because Verizon is seeking a waiver identical to the waiver granted to AT&T and committing to the same conditions that were fully considered by the Commission on a well-developed record, there is no need for the Commission to seek additional public comment here and the Commission should promptly grant this petition.”
If Verizon can get its TTY waiver, then it will be able to support “true” Wi-Fi calling on both iOS and Android devices which would both be able to make calls over Wi-Fi through their native dialers rather than a separate mobile app.
References:
http://www.theverge.com/2015/10/25/9611746/verizon-wi-fi-calling-feature-seeks-fcc-approval
http://www.pcmag.com/article2/0,2817,2493836,00.asp
http://appleinsider.com/articles/15/10/06/att-granted-fcc-waiver-to-activate-wi-fi-calling-amid-tiff-with-t-mobile-sprint
http://apps.fcc.gov/ecfs/document/view?id=60001330537
http://transition.fcc.gov/Daily_Releases/Daily_Business/2015/db1006/DA-15-1141A1.pdf
FCC takes steps to facilitate mobile broadband & nex gen wireless technologies above 24 GHZ
The FCC has issued a Notice of Proposed Rulemaking (NPRM) that proposes new rules for wireless broadband operating in frequencies about 24 GHz. The NPRM proposes to create new flexible use service rules in the 28 GHz, 37 GHz, 39 GHz, and 64-71 GHz bands. It proposes to make these bands available using a variety of authorization schemes, including traditional wide area licensing, unlicensed, and a shared approach that provides access for both local area and wide area networks.
These proposed rules are an opportunity to move forward on creating a regulatory environment in which these emerging next-generation mobile technologies – such as so-called 5G mobile service – can potentially take hold and deliver benefits to consumers, businesses, and the U.S. economy.
“Building off of years of successful spectrum policy, this NPRM proposes to create new flexible use service rules in the 28 GHz, 37 GHz, 39 GHz, and 64-71 GHz bands. The NPRM proposes to make these bands available using a variety of authorization schemes, including traditional wide area licensing, unlicensed, and a shared approach that provides access for both local area and wide area networks.
In addition, the NPRM provides a path for a variety of platforms and uses, including satellite uses, to coexist and expand through market-based mechanisms,” the FCC wrote in a press release.
http://transition.fcc.gov/Daily_Releases/Daily_Business/2015/db1022/DOC-335993A1.pdf
CTIA vice president of Regulatory Affairs Scott Bergmann called the NPRM an “important step” towards clearing additional spectrum. He wrote in a statement:
“Today’s action also reminds us that the diversity of 5G applications will require a broad range of spectrum types, including low and medium band spectrum, below 3 GHz and between 3 – 6 GHz, as well as streamlined infrastructure siting and more backhaul. The move to bring to market high band spectrum in bands above 24 GHz offers the potential for increased capacity and speeds, lower lag time and high density connections to unleash the Internet of Things. We look forward to working with the Commission to address a flexible framework for service in these bands that encourages continued investment and innovation to deliver the next waves of connected wireless applications.“


