Heavy Reading: “The Journey to Cloud Native” – Will it be a long one?
To gauge how carriers are planning and implementing cloud-native technology, and in collaboration with Juniper, Nokia and Red Hat, Heavy Reading asked 92 global telco service providers about their plans for transition to cloud native. In their report, “The Journey to Cloud Native,” Heavy Reading analyzes the choices service providers are making along the road to cloud native and what challenges they are encountering along the way.
The migration to cloud native brings largescale shifts for the communications service providers (CSPs), including:
- The move to microservices
- Standardized access to these microservices via API exposure
- The integration of multiple operational layers and domains for application management
- Automation across the application lifecycle through the use of DevOps
These are profound changes to the application development and management environment of the CSPs, and will be tackled with dedicated internal resources and expanded partnerships with telecommunication equipment vendors (TEMs), integrators and hyper-scalers (Amazon, Google, Microsoft, Facebook, etc.).
Editor’s Note: There are no standards or implementation specs for “Cloud Native” 5G SA core network or anything else. Rakuten Symphony (Japan) and Reliance Jio (India) claim they are going to implement “Cloud Native” 5G SA core network themselves and sell the specifications and software to other service providers. Good luck! We think it will be a very long journey to cloud native for telecom network operators/5G SA core network service providers.
The prospect of cloud native:
Heavy Reading queried the survey pool about where they were experiencing the greatest challenge in deploying cloud native: the network, operations support systems (OSS), business support systems (BSS), or the enterprise (see Figure 1). Heavy Reading established earlier in the survey that cloud native will be deployed first for network workloads. Respondents plan to transition workloads to the OSS business areas next, then BSS, and lastly, the enterprise.
In almost all cases, respondents ranked the challenges in that same order: first network, then OSS, BSS, and enterprise. The only challenges that were considered more severe in an area other than the network were “in-house development and integration skills” and “development and integration tooling,” where the OSS space was recognized as a greater challenge than the network. This is not surprising given that most Tier 1 carriers have dozens of OSS solutions in operation. They do much of any integration work between systems internally and some OSS systems are stand-alone – dedicated to siloed services.
Figure 1: The network space is seeing the most implementations and the most challenges N=92
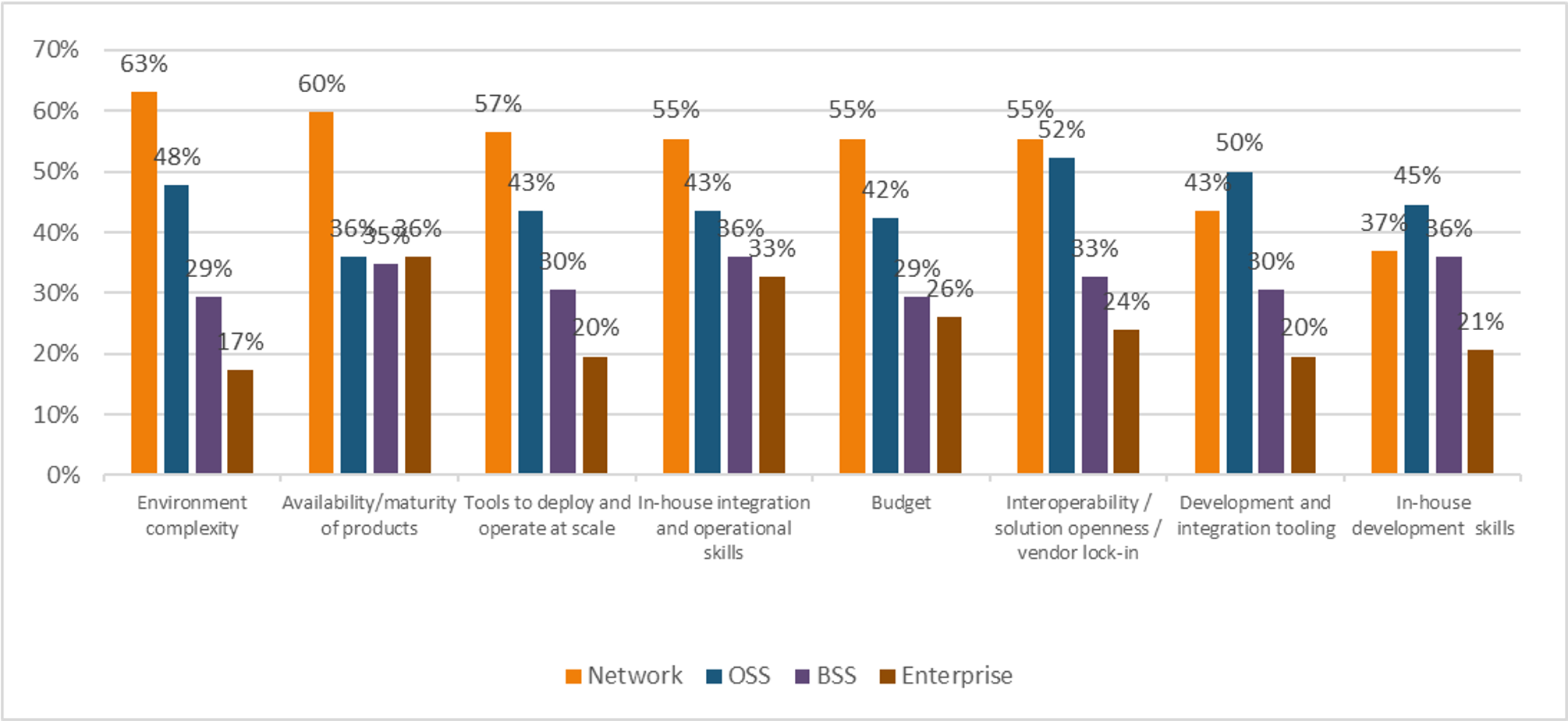
Q: In which business areas are you experiencing significant challenges to going cloud native? Check all that apply. Source: Heavy Reading
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………..
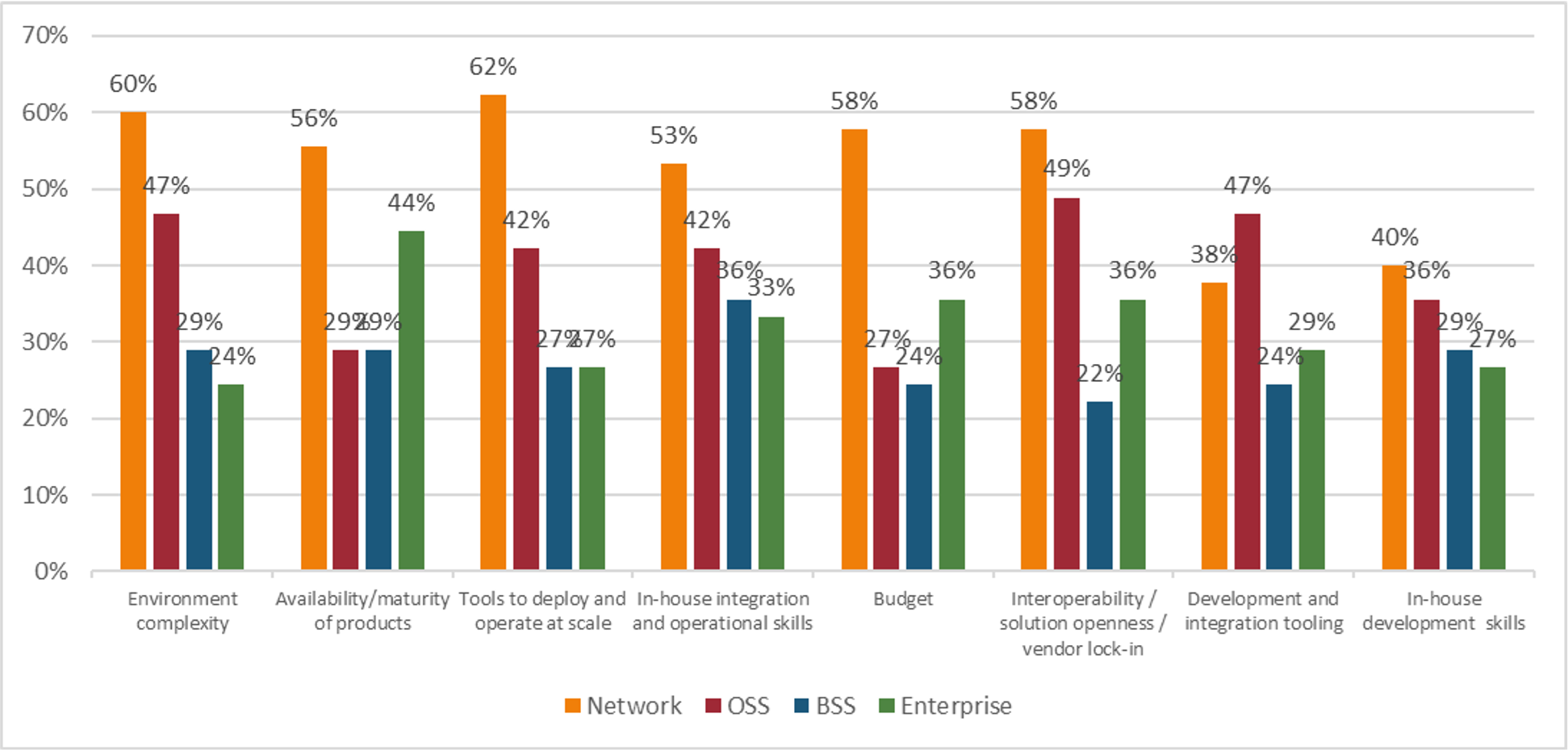
Looking only at the survey results from respondents who have already deployed cloud native, (see figure 2), which is half of the respondent pool, there are significant differences compared to the rest of the survey base. In the network area, “tools to deploy and operate at scale” is a greater challenge by 11 percentage points compared to respondents planning to deploy cloud native in one to two years.
“Budget” in the OSS area plummets between those who have not yet deployed cloud native, (57% of respondents considering it a challenge), and those who have already deployed cloud native, (27% of the respondents finding it to be a concern).
Those who have already deployed cloud native also consider all of the challenges in the enterprise area to be greater than the survey base as a whole and all of the challenges in the BSS area to be less of a challenge. Their firsthand experience with implementing cloud native in the network area has opened their eyes to the challenges that await them in the enterprise space. However, they are more confident that they have the support needed, near term, for BSS tasks which include billing, revenue, and customer management.
n=45: only respondents that have already implemented Cloud Native
Source: Heavy Reading
Heavy Reading’s findings might be a good indication that CSPs today are committed to their journey to cloud native, but face daunting challenges that will require expanded partnerships with the cloud-native ecosystem, including platform vendors, ISVs (Independent Software Vendors), TEMs (Telecom Equipment Manufacturers???) and hyper-scalers.
To gain more in-depth details of service providers’ perspective on cloud-native migration, download and read the full report now.
— Jennifer Clark, Principal Analyst, Cloud Infrastructure and Edge Computing, Heavy Reading
References:
https://www.lightreading.com/new-report-highlights-cloud-native-migration-challenges/a/d-id/774623?
https://www.lightreading.com/lg_redirect.asp?piddl_lgid_docid=773720
4 thoughts on “Heavy Reading: “The Journey to Cloud Native” – Will it be a long one?”
Comments are closed.



9 Ways to Fail at Cloud Native
I’m not the only one that is skeptical, if not negative, about “Cloud Native” anything to do with telcos.
https://www.infoq.com/presentations/fail-cloud-native-migration/
Cloud Native Security:
New trends in cloud security are emerging that help address security concerns for modern, cloud-native applications. Let’s look at some of the critical areas of cloud security that will be important in the coming year.
1. API Security
APIs are an essential component of modern applications. Distributed applications rely on APIs so that different services can interact with each other and perform specific tasks. Modern workloads can have thousands of APIs. However, APIs aren’t inherently secure and can become a liability if teams don’t weave API security into the application development.
APIs are usually documented, and anyone, including malicious actors, can access said documentation. Attackers can then reverse engineer APIs and make their way into critical workloads where they can keep stealing data without detection. API security is emerging as a popular trend in the cloud security space.
API Security cannot be a manual process due to the sheer number of APIs in workloads and the inevitability of human error. Some tools integrate with organizations’ CI/CD pipelines and provide end-to-end visibility and enforce security at every step of the software development lifecycle, so the APIs are not vulnerable to attacks.
2. Supply Chain Security
Modern supply chains tend to be highly complex and nonlinear, making it hard to monitor or secure them. Today, supply chains comprise hundreds of suppliers and third-party vendors. And, most of the supply chains leverage the cloud, making them susceptible to attacks. The large attack surface of today’s supply chains can become a massive problem if security isn’t built into the supply chains.
Several high-profile breaches and leaks have made headlines in the last couple of years. Attackers can simply inject malicious code into software updates or tamper with the hardware to access sensitive data. The biggest challenge with supply chain security is standardizing security across all suppliers. There’s no point securing the supply chain if the suppliers’ systems aren’t secure.
For convenience, many organizations give suppliers access to sensitive data. And, not all the suppliers need access to said data. Attackers can simply use a supplier system to gain access to sensitive data. Organizations should enforce zero-trust security and standardize baseline security across all the suppliers in their supply chain. More organizations will gravitate towards supply chain security strategies and solutions to ensure their supply chains stay secure in the coming year.
Image Source: Pixabay
3. Secrets Management
Modern applications use hundreds of application tools, microservices, and privileged accounts requiring keys and passwords. These keys and passwords are essential for application-to-application and application-to-database communication. However, the sheer volume of secrets means admins and developers will be swimming in them if they don’t have an excellent secret management strategy.
Secret management shouldn’t be done manually because that can lead to human error and gaps in security that attackers can exploit. Some tools and solutions ship with hardcoded secrets that are easy to guess, while sometimes admins might create secrets that are easy to remember. This can all have dire consequences.
Another lapse that can happen while managing secrets, if they’re being managed at all, is the third-party access to secrets. Again, no amount of security will be beneficial if third-party tools aren’t secure, to begin with. DevOps tools can pose a big problem because these tools have access to several resources and orchestration tools. If attackers hack into the DevOps tools, they can easily access sensitive information.
Secrets management is vital, but it’s also complex. Teams should be well versed in best practices while dealing with keys and passwords. At the same time, organizations should employ tools that perform secrets management and provide holistic security to their workloads. There’s quite a lot of innovation happening in this space as organizations look for better and easier ways to manage their secrets.
4. Identity and Access Management
Today’s IT landscape requires a zero-trust security model rather than just firewalls. Developers, customers, suppliers, and partners all need access to certain services or data, and this cannot be done efficiently without proper IAM (Identity and Access Management). IAM allows organizations to store individuals and devices as identities for data governance. This allows IT teams to easily manage and monitor each identity and assign only the relevant access they need to get their work done.
In the age of IoT, devices communicate with each other, and the servers and these devices can easily be hacked into if there is no proper IAM implementation. Rogue actors can misuse their access to steal data which can also land the organization in trouble. Today, organizations are under pressure from regulatory and compliance teams to secure their data properly.
Organizations can implement multifactor and biometric authentication and behavioral analysis using AI to identify unusual behaviors among devices and individuals with IAM. With automated IAM, IT teams can focus on what really matters rather than worrying about compliance.
https://techgenix.com/five-key-areas-of-cloud-native-security-that-will-matter-in-the-upcoming-year/
Sterlite, Robin.io to provide tech for 5G stack for enterprise -Robin.io will provide the cloud-native platform for deploying applications and network functions on the STL Enterprise Marketplace platform.
Robin.io, a Kubernetes data management platform, will collaborate with Sterlite Technologies (STL) to offer Xaas solution for enterprise applications and 5G services effectively.
“Built on the foundation of cloud-native, zero-touch automation and open architectures, the integrated marketplace solution will enable CSPs to deliver new revenue models and accelerate customer onboarding while keeping service delivery costs in check,” said Partha Seetala, founder and CEO of Robin.io.
There is a growing trend among the Communication Service Providers (CSPs) to become an enterprise platform provider to leverage the massive opportunities it provides.
STL Enterprise Marketplace is a new-age, platform-based model that simplifies collaboration and has the potential to open up multi-sided marketplace opportunities. STL offers end-to-end software solutions for creating new-age digital services, building new business models, and opening new revenue streams.
The Platform brings together service providers, partners and enterprise customers from different verticals on the same Platform. Robin CNP provides storage, network management and scheduling to run complex network workloads from application vendors and partners across a wide spectrum of use cases.
Commenting on the collaboration, Saikat Mitra, COO of STL Network Software, said, “Extreme automation and true cloud-native platforms are key to accelerating digital transformation. In its endeavor to bring innovative XaaS
offerings faster to the market, STL has been supporting a hybrid network ecosystem with its 5G Enterprise Marketplace and 5G monetization initiatives.
In this strategic partnership, we are bringing our Enterprise Marketplace Platform enabling Robin.io to achieve seamless cloud infrastructure management for multi-datacenter, multi-cloud and multi-edge ecosystems and actualize their vision on 5G, IoT and WiFi.”
https://www.dqindia.com/sterlite-robin-io-to-provide-tech-for-5g-stack-for-enterprise/
https://www.stl.tech/
Nice post… Keep sharing. For sure it will be a long journey to Cloud Native for every conceivable telecom function. Note that MEC really needs a 5G SA Core network for which there are very few and even fewer that are “cloud native.”