5G Security
Strong Growth Forecast for 5G Security Market; Market Differentiator for Carriers
Some key findings from ResearchAndMarkets.com’s “5G Security Market by Technology, Solution, Category, Software, Services, and Industry Vertical Support 2021 – 2026” new report:
- The overall global 5G security market will reach $9.2 billion by 2026 [1.]
- The fastest-growing segment will be communications security at 49.2% CAGR
- North America [2.] will be the leading region projected to reach $4.1 billion by 2026
- Integrated 5G security and blockchain solutions will reach $183.1 million by 2026
- AI-based solutions for edge computing infrastructure will reach $253.2 million by 2026
- Distributed denial of service (DDoS) protection for 5G networks will reach $583 million by 2026
- Major drivers for carrier 5G security include 5G core network implementation and support of private wireless networks
- Leading carriers will transform 5G security from a cost of doing business into a major market differentiator for business customers
Note 1. In February 2021 report, Markets and Markets said that 5G security market size is projected to grow from $580 million in 2020 to $5.226 billion by 2026, at a compound annual growth rate (CAGR) of 44.3%. The market research firm believes the major drivers for the 5G security market include rising security concerns in the 5G networks, increasing ransomware attacks on IoT devices, rising attacks on critical infrastructure, and increasing IoT connections paved way for mMTC with enhanced security requirement.
The “cloud native mode” of 5G core/SA deployment is expected to exhibit a higher CAGR during the forecast period. By deploying 5G security solutions and services on the cloud, organizations can avoid spending on hardware, software, storage, and technical staff.
The cloud deployment type is often used for both private and public clouds and may vary from case to case, depending on the requirement of the client.
Additionally, organizations can scale up or down, depending on their use of cloud-based 5G security services. The cloud deployment segment has witnessed strong demand in the early phase of the 5G standalone network. It offers a wide range of benefits, such as scalability, accessibility, flexibility, and cost-effectiveness.
Note 2. Markets and Markets expects the APAC region to hold the largest market share during the forecast period. China, Australia, and Japan are the prime APAC countries that have started several 5G-related activities; which would provide growth opportunities for 5G security vendors in the region.
Asian telecom service providers, vendors, and government firms are determined to take the lead in 5G R&D. The infrastructural growth in APAC, especially in Japan, South Korea, Australia, Singapore, China, and India, and the increasing deployment of 4G and 5G networks present huge opportunities for the implementation of the 5G security solutions.
……………………………………………………………………………………………………………………………………………
The ResearchAndMarkets.com report evaluates the 5G threat landscape as well as technologies and solutions to secure networks, platforms, devices, data, and applications [3.]. The report also assesses the 5G security market outlook and potential for many solutions, services, and support. It also evaluates the impact of security functions across various technologies including Mobile Edge Computing (MEC), IoT networks, and mobility infrastructure. The report includes market forecasts for all major technologies, industry verticals, solutions, and service types from 2021 to 2026.
The 5G security market must be robust as solutions need to be deployed on multiple levels including devices, air interface equipment, cloud RAN infrastructure, mobile backhaul facilities, and more.
Note 3. There’s likely to be an increasing adoption of 5G security solutions by carriers. It will be used for identity management, differentiated security protection, privacy protection and growing demand for data protection worldwide. 5G security technology offers various benefits such as diversified system level protection of IT-aware infrastructure, security as service, and rapid detection and response.
The growing demand for a security monitoring and threat analysis to help the business to protect the integrity of systems and data is expected to create a huge opportunity for the global 5G Security market.
In addition, the need for E2E security for vertical industries from protection to detection and increasing importance of a unified security view across enterprise, are anticipated to drive the 5G Security market growth.
Reference: https://www.futuremarketinsights.com/reports/5g-security-market
![]()
……………………………………………………………………………………………………………………………………..
Among other areas, the 3GPP Security architecture and procedures for 5G System (Specification #: 33.501) specifies requirements for E1 and f1 interfaces as well as requirements for an overall secure environment. The organization specified many areas necessary for 5G security including subscription authentication, UE authorization, access and serving network authorization and more. Other areas include user and signaling data integrity to ensure seamlessness and interoperability between network elements.
Note that there are no ITU-T recommendations on 5G/IMT 2020 security.
One of the import areas emerging with 5G security that is a greater concern than ever before is data security and private. Much more so than LTE, 5G networks must be concerned with the confidentiality and integrity of user and signaling data. The 5G gNB must support encryption as per security policies for various potential vulnerability areas such as user data in transit as well as signaling for radio resource control. Access control is equally important as well as ensuring that serving networks are authorized by home networks.
5G mobile network operators need to expedite implementation of a more integrated 5G security approach, one of the primary areas of focus will be support of 5G-based private wireless networks for enterprise and industrial customers. While today’s private networks take a more old-school approach to security, more security-minded enterprise, industrial and government sector customers will realize greater cybersecurity through interconnection and managed services with leading carrier 5G security solutions.
Leading carriers will transform 5G security from a cost of doing business into a major market differentiator for business customers including direct to enterprise/industrial/government customers and via hybrid models involving neutral hosts and/or direct interconnect with private wireless networks. The challenging task for mobile network operators is to simultaneously convince business customers that they are more secure with them than without them, while not causing alarm about security holes that existed prior to implementation of 5G security solutions.
For more information about this report please visit: https://www.researchandmarkets.com/r/vqa21q
………………………………………………………………………………………………………………………………………….
In a recent IEEE Future Networks presentation titled, Security Considerations for Evolving RAN Architectures, Scott Poretsky and Jason Boswell of Ericsson wrote about “the trust stack in 5G Cloud RAN.” Here’s what they said (emphasis added):
Network security is built upon a trust stack of trusted hardware, trusted software, trusted deployment, trusted applications, and trusted operations. Cloud deployments have an expanded attack surface due to decoupling of the software from the hardware, multiple organizations sharing the same hardware, a third-party organization managing the cloud infrastructure, and use of open source software components.
The chain of trust between these disparate components is not standardized and is implementation dependent, making it challenging to determine the level of risk, such as defined by the NIST Risk Management Framework (RMF). In a cloud environment an external attacker could gain access to a compromised container and from there escalate privilege to gain access to services and infrastructure. Likewise, an attacker that gains access to a service can use it as platform to gain access to containers and infrastructure.
Reference:
https://www.ericsson.com/en/reports-and-papers/white-papers/security-in-5g-ran-and-core-deployments
………………………………………………………………………………………………………………………………
Report Linker: 5G Security Market to experience rapid growth through 2026
Report Linker forecasts that the global 5G security market will grow from USD 580 million in 2020 to USD 5,226 million by 2026, at a Compound Annual Growth Rate (CAGR) of 44.3% during the forecast period.
The 5G security market is gaining traction due to rising security concerns in the 5G networks, increasing ransomware attacks on IoT devices, rising attacks on critical infrastructure, and increasing IoT connections paved way for mMTC with enhanced security requirement. However, high cost of 5G security solutions will restrain the adoption by SMEs.
The implied negative flipside for operators and enterprises, of course, is that more money will have to be spent on tackling 5G vulnerabilities. The report pointedly notes that the high cost of 5G security solutions will limit adoption by SMEs.
Based on solution type, the DDoS protection solution segment is expected to grow with the fastest growth rate during the forecast period
The DDoS protection segment is projected to grow with the most rapid growth rate in 2020 to 2026.Enterprises use DDoS protection and mitigation solutions and services for adaptive defense against DDoS attacks.
These attacks further affect the confidentiality, integrity, and availability of resources, which may result in billion-dollar losses for enterprises.
Enterprises segment to grow at the highest CAGR during the forecast period
Enterprises are undergoing digital transformation across different industries. Businesses are in various stages of implementing new technologies to develop new solutions, improve service delivery, increase operational efficiency, reduce cost, gain competitive advantage, and meet rising customer expectations. 5G will soon make it into the list of technologies enterprise will consider, with standalone 5G solutions that will enable various new industrial applications, such as robotics, big data analytics, IIoT and AR/VR in engineering and design, as well as new ways to provide remote support and training. As a result, enterprises will need 5G security mechanism to secure the entire network, applications, and devices.
Asia Pacific (APAC) region to record the highest growth and also account for largest markety share in the 5G security market
APAC region is set to dominate 5G, edge computing, blockchain, and 5G security technology, due to its size, diversity, and the strategic lead taken by countries, including Singapore, South Korea, China, Australia, and Japan.These countries have always supported and promoted industrial and technological growth.
Also, they possess a developed technological infrastructure, which is promoting the adoption of 5G security solutions across all industry verticals. Moreover, the region has become the center of attraction for major investments and business expansion opportunities.
While Reportlinker.com praises APAC for leading in 5G security, Europe is way behind if a recent report according to a report from the European Court of Auditors (ECA).
A year-long ECA probe into how European Union (EU) member states are dealing with 5G security found that while “member states have started to develop and implement necessary security measures to mitigate risks, they seem to be progressing at a different pace.”
More worryingly, Annemie Turtelboom, the ECA member leading the audit, indicated that some EU countries were bypassing supplier security checks in order to speed up 5G rollout.
………………………………………………………………………………………..
Companies such as ZTE (China), Samsung (South Korea), and Huawei (China) are heavily investing in the upcoming 5G technology and are initiating field trials together with some of the leading mobile service carriers, such as China Telecom (China), KT (South Korea), SK Telecom (South Korea), China Mobile (China), SoftBank (Japan), and China Unicom (China).
• By Company Type: Tier 1 – 62%, Tier 2 – 23%, and Tier 3 – 15%
• By Designation: C-level – 38%, Directors – 30%, and Others – 32%
• By Region: North America – 40%, Europe – 15%, APAC – 35%, and Rest of the World (RoW)– 10%
This research study outlines the market potential, market dynamics, and major vendors operating in the 5G security market. Key and innovative vendors in the 5G security market include A10 Networks (US), Akamai (US), Allot (Israel), AT&T (US), Avast (Czech Republic), Check Point (US), Cisco (US), Clavister (Sweden), Colt Technology (UK), Ericsson (Sweden), F5 Networks (US), ForgeRock (US), Fortinet (US), G+D Mobile Security (Germany), Huawei (China), Juniper Networks (US), Mobileum (US), Nokia (Finland), Palo Alto Networks (US), Positive Technologies (UK), Radware (Israel), Riscure (The Netherlands), Spirent (US), Trend Micro (Japan), and ZTE (China).
Research coverage
The market study covers the 5G security market across different segments. It aims at estimating the market size and the growth potential of this market across different segments based on component (solutions and services), network component security, architecture, end user, deployment type, vertical, and region.
The study also includes an in-depth competitive analysis of the key market players, along with their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
References:
https://www.lightreading.com/security/5g-security-market-set-to-boom-report/d/d-id/767415?
European Court of Auditors Concern: EU’s Divergent Approach to Security of 5G Networks
EU nations are ‘progressing at different paces’ in terms of cyber security protocols introduced by the European Commission in order to ensure the safety of next-generation telecommunications networks, the European Court of Auditors has said.
The news comes at the beginning of a year-long probe into the EU’s security of 5G networks by auditors, while the European Commission has also confirmed to EURACTIV that nations across the bloc have missed deadlines set out in law, which had bound countries to assign 5G spectrum frequencies by the end of 2020.
Auditors say their research has already unearthed evidence of a divergent approach to 5G security across member states [1.], as well as differences in deployment timelines for the technology across the continent. As part of a series of measures unveiled by the Commission in their 2020 5G Toolbox, member states were tasked with assessing the risk profile of telecom providers, with a view to applying restrictions for those vendors considered to be high-risk.
Note 1. Of course, there is an inconsistent approach to 5G security as there are no standards for same from ITU and the 3GPP Release 16 specs for 5G Security are incomplete (delayed to Release 17). That was all described in this IEEE Techblog post.
The toolbox highlighted that “a particular threat stems from cyber offensive initiatives of non-EU countries,” in a veiled reference to Chinese telecommunications providers Huawei and ZTE.
![]()
“Several member states have identified that certain non-EU countries (China?) represent a particular cyber threat to their national interests based on previous modus operandi of attacks by certain entities or on the existence of an offensive cyber program of a given third state against them,” the toolbox adds.
A progress report on the plans in July pressed member states to make ‘urgent progress’ on mitigating the risks to 5G telecommunications networks posed by certain high-risk suppliers.
Speaking on Thursday (7 January 2021), the European Court of Auditors’ Paolo Pesce, part of the team conducting the 12-month review, said harmonization across the bloc on such security standards had not happened yet. “Member states have developed and started implementing necessary security measures to mitigate risks,” Pesce said. “But from the information gathered so far, member states seem to be progressing at a different pace as we implement this measure.”
Annemie Turtelboom, the ECA member leading the audit, added that the report will seek to probe the trade-off EU nations seem to be making with regards to security and speed of deployment.
“The coronavirus crisis has made electronic communications including mobile communications even more vital for the citizens and businesses while making it more difficult to timely prepare authorization procedures so that several member states have recently expressed their intention to delay their national spectrum auction procedures,” a spokesperson told EURACTIV.
“The Commission will follow the matter closely and take any difficulty into consideration considering the impact of the current public health crisis.”
However, it appears that the security concerns of contracting various suppliers have been just as relevant in the delays as has the coronavirus pandemic.
In one recent example, Sweden had to sideline auctions for its 3.4-3.6 GHz and 3.6-3.8 GHz bands, after telecoms regulators PTS prohibited the use of equipment from Chinese firms Huawei and ZTE. Earlier this week, Huawei announced that it had lodged an appeal to the supreme administrative court for being frozen out of the auctions.
By mid-December, member states, including the UK, had assigned on average only 36.1% of the 5G pioneer bands, the European Commission informed EURACTIV. Under the 2018 Electronic Communications Code, all spectrum in the 700MHz band should have been awarded by June 30, 2020, with allocations of 3.6GHz and 26GHz airwaves wrapped up by December 31, 2020.
References:
Commission presses member states to take action on high-risk 5G vendors
5G Security Vulnerabilities detailed by Positive Technologies; ITU-T and 3GPP 5G Security specs
5G Security Vulnerabilities detailed by Positive Technologies; ITU-T and 3GPP 5G Security specs
Introduction:
Mobile network operators are mostly running 5G non-standalone networks (NSA), which are based on 4G LTE infrastructure. Positive Technologies said these 5G NSA networks are at risk of attack because of long-standing vulnerabilities in the Diameter and GTP protocols, which were reported on by Positive Technologies earlier this year.
“… true 5G security must go beyond the features built into standalone architecture,” said Pavel Novikov, head of the Positive Technologies’ telecom security research team. “Cost efficiencies can be gained by building a hybrid network that supports both 4G LTE and 5G which will enable a future-proofed next generation network in the longer term,” he added.
What will be the 5G security issues/vulnerabilities when mobile network operators move to deploy 5G stand alone networks with a 5G core (rather than 4G EPC used in 5G NSA)?
Background:
Cellular network operators are gradually migrating to 5G standalone infrastructure [T-Mobile US has deployed 5G SA]. but this also has security considerations of its own. Gartner expects 5G investment to exceed LTE/4G in 2022 and that communications service providers will gradually add 5G standalone capabilities to their non-standalone 5G networks.

Source: Positive Technologies’ Standalone 5G core security research
………………………………………………………………………………………………………………………
Discussion:
Vulnerabilities and threats for subscribers and mobile network operators stem from the use of new standalone 5G network cores. The vulnerabilities in protocols HTTP/2 and PFCP, used by standalone 5G networks, include the theft of subscriber profile data, impersonation attacks and faking subscriber authentication.
The stack of 5G technologies potentially leaves the door open to attacks on subscribers and the operator’s network. Such attacks can be performed from the international roaming network, the operator’s network, or partner networks that provide access to services.
For example, the Packet Forwarding Control Protocol (PFCP) that is used to make subscriber connections has several potential vulnerabilities such as denial of service, cutting subscriber access to the internet and redirecting traffic to an attacker, allowing them to downlink the data of a subscriber. Correct configuration of the architecture as highlighted in Positive Technologies GTP protocol research can stop these types of attacks.
The HTTP/2 protocol, which is responsible for vital network functions (NFs) that register and store profiles on 5G networks, also contains several vulnerabilities. Using these vulnerabilities, attackers could obtain the NF profile and impersonate any network service using details such as authentication status, current location, and subscriber settings for network access. Attackers can also delete NF profiles potentially causing financial losses and damaging subscriber trust.
In these cases, subscribers will be unable to take action against threats that lurk on the network, so operators need to have sufficient visibility to safeguard against these attacks.
Dmitry Kurbatov, CTO at Positive Technologies commented: “There is a risk that attackers will take advantage of standalone 5G networks while they are being established and operators are getting to grips with potential vulnerabilities. Therefore, security considerations must be addressed by operators from the offset. Subscriber attacks can be both financially and reputationally damaging – especially when vendors are in high competition to launch their 5G networks. With such a diverse surface of attack, robust core network security architecture is by far the safest way to protect users.
“5G standalone network security issues will be much further reaching when it comes to CNI, IoT and connected cities – putting critical infrastructure such as hospitals, transport and utilities at risk. In order to achieve full visibility over traffic and messaging, operators need to perform regular security audits to detect errors in the configuration of network core components to protect themselves and their subscribers,”
Jimmy Jones, telecoms cybersecurity expert at Positive Technologies, said 5G users will need to increase their lines of communication with mobile operators, analysts and customers as 5G presents new threats and attack surfaces.
“They’re going to need to start speaking to the mobile operators as much as possible, because the mobile operators can secure things and will do everything to secure things. They just need to know what they’re securing,” Jones added.
[This author has spoken at length with Jimmy Jones and can attest to his vast knowledge and experience in cellular network security/vulnerabilities]

Jimmy Jones, Positive Technologies Network Security Expert
Positive Technologies has published a new report titled “5G standalone core security assessment,” which details the vulnerabilities of those networks.
The report focuses on the SA (Standalone) mode of 5G network deployment. “The implementation is based on Rel 15 3GPP with the OpenAPI Specification providing detailed descriptions of each interface,” the researchers explain.
Again, almost all deployed 5G networks are based on NSA which depend on a “4G LTE anchor for all non radio functions, including the 4G EPC (Evolved Packet Core) technology. The 5G core network architecture (but not implementation details) is specified by 3GPP and includes the following Technical Specifications:
| TS 23.501 | System architecture for the 5G System (5GS) |
| TS 23.502 | Procedures for the 5G System (5GS) |
| TS 23.503 | Policy and charging control framework for the 5G System (5GS); Stage 2 |
The 5G mobile network consists of nine network functions (NFs) responsible for registering subscribers, managing sessions and subscriber profiles, storing subscriber data, and connecting user equipment to the Internet using a base station. These technologies create a liability for attackers to carry out man-in-the-middle and DoS attacks against subscribers.
One of the main issues in the system architecture is the interface responsible for session management, known as SMF (Session Management Function). SMF is possible due to a protocol known as PFCP (Packet Forwarding Protocol):
To manage subscriber connections, three procedures are available in the PFCP protocol (Session Establishment, Modification, and Deletion), which establish, modify, and delete GTP-U tunnels on the N3 interface between the UPF and gNB. […] We will focus on the N4 interface. Testing of this interface revealed potential attack scenarios against an established subscriber session.
Other problems Positive Technologies discovered are based on subscriber authentication vulnerabilities. The researchers demonstrated that “subscriber authentication becomes insecure if the NRF does not perform authentication and authori-zation of 5G core network functions.”
In conclusion, this report only covers “a few examples” of how vulnerabilities in G5 can be exploited. “Just as with previous-generation networks, attackers still can penetrate operator networks by means of the international roaming network or partner networks. Therefore, it is vital to ensure comprehensive protection of 5G networks,” the report concludes.
For more information on vulnerabilities of standalone 5G networks, please download the Positive Technologies report here –after filling out a form. …………………………………………………………………………………………………………………..
Editor’s Note: 5G Security Standards (?) and Specifications
Most 5G “professionals” don’t realize that there are no standards for 5G security– either in the radio access network (RAN) or the core network. As ITU is the official standards body for 5G (e.g. IMT 2020.SPECS for the RAN) you’d think the work would be done there. There is some high level 5G security work being done in ITU-T SG 17/Q6, but the corresponding ITU recommendations won’t be completed till late 2021- 2o22 timeframe.
The real work on 5G security is being done by 3GPP with technical specification (TS) 33.501 Security architecture and procedures for 5G system being the foundation 5G security document. That 3GPP spec was first published in Release 16, but the latest version dated 16 December 2020 is targeted at Release 17. You can see all versions of that spec here.
3GPP’s 5G security architecture is designed to integrate 4G equivalent security. In addition, the reassessment of other security threats such as attacks on radio interfaces, signaling plane, user plane, masquerading, privacy, replay, bidding down, man-in-the-middle and inter-operator security issues have also been taken in to account for 5G and will lead to further security enhancements.
Another important 3GPP Security spec is TS 33.51 Security Assurance Specification (SCAS) for the next generation Node B (gNodeB) network product class, which is part of Release 16. The latest version is dated Sept 25, 2020.
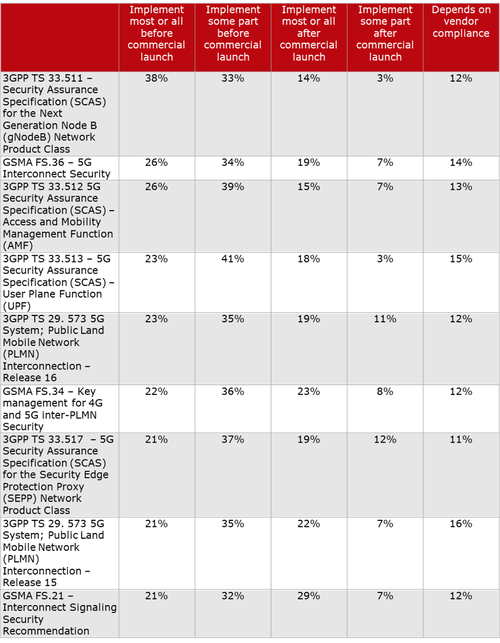
Here’s a chart on 3GPP and GSMA specs on 5G Security, courtesy of Heavy Reading:
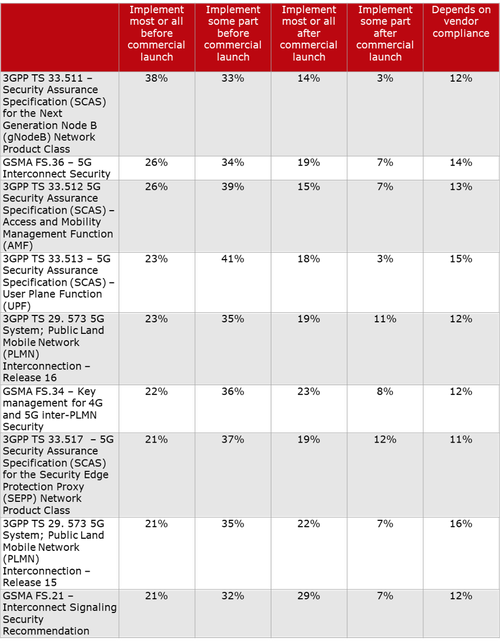
Question to 5G network operators: When do you plan to implement the following 5G security specifications? Source: Heavy Reading
“While 3GPP TS 33.511 had the greatest level of commitment to implementing before commercial launch (38% + 33%), the support for all nine specifications in the list is strong enough to confirm each one is relevant on some level for ensuring the security of 5G networks,” according to Heavy Readings’ Jim Hodges.
………………………………………………………………………………………………………………………
References:
https://sensorstechforum.com/new-5g-vulnerabilities-dos-mitm-attacks/
https://www.ericsson.com/en/blog/2020/6/security-standards-role-in-5g
https://www.itu.int/ITU-T/workprog/wp_search.aspx?&isn_sg=3935&isn_wp=6682&isn_qu=4216&details=0
https://www.3gpp.org/news-events/1975-sec_5g
https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3169
https://www.3gpp.org/ftp//Specs/archive/33_series/33.501/
https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3444
5G Security Issues Raise Mission Critical Questions & Issues
The type of AKA associated with 5G (via 3GPP- not ITU-R) should ensure that a device and a 5G network can authenticate each other while maintaining a confidential data exchange and keeping the user’s identity and location private. However, the researchers say, in its current state, the AKA could not fulfill those security aims because the requirements it sets forth are not sufficiently precise.
The team of researchers emphasized their belief that the AKA security for 5G would be superior to the AKA used in 3G and 4G network protocols. It still has gaps, though, including one that shows a phone’s presence in the vicinity without disclosing its owner’s identity. Moreover, this vulnerable version of the AKA could result in a person getting wrongfully charged for a third party’s usage of the 5G network.
The published paper about these findings recommends fixes. They include explicitly requiring intended security properties currently missing from the AKA and modifying the key-confirmation component so it offers a provably secure solution. Overall, the researchers say the AKA does not adequately protect privacy from active attackers but admit remedying that problem would not be straightforward.
In an attempt to implement more security in the AKA, the researchers have reached out to 3GPP and hope to engage in a joint effort to improve the protocol before 5G’s widespread rollout. Also, the European Union Agency for Network and Information Security, or ENISA, released a different report warning that identified flaws with signaling protocols on the 2G, 3G and 4G networks could appear in the 5G network.
Ericsson show there could be 3.5 billion Internet of Things units by 2023 — equalling five times the number of connected devices used now. Additionally, the company forecasts that 5G networks will spur the growth of Internet-connected devices.
People became familiar with the security weaknesses of IoT devices when cybercriminals first targeted them with distributed denial of service attacks several years ago.
An insecure 5G network sets the stage for increasingly widespread attacks due to 5G’s high-speed bandwidth, which increases the available attack points. It’s not difficult to imagine a business using IoT sensors within a factory setting and getting shut down due to a DDoS attack.
Chip architecture company Arm is working on a software stack that would let IoT devices run with SIM card chips, thereby making them similar to smartphones with mobile data plans. Then, it would not be necessary to connect IoT devices via Wi-Fi. However, hackers can attack SIM cards and make them unusable. They can also distribute malware through text messages during SIM card attacks.
It’s too soon to say whether hackers will exploit SIM vulnerabilities in IoT devices that may eventually include them, but the possibility is there. In any case, it’s evident that the opportunities 5G offers could spur hackers’ efforts to launch increasingly devastating attacks using methods people already know, as well as wholly new techniques.
“5G doesn’t necessarily changes the risk factors we have today,” said Tom Lally, vice president of sales for data storage and management company, DataSpan, Inc. “But it is going to exponentially increase the threat vectors and opportunities for attackers to exploit.”
“5G is going to enable businesses to connect more and more devices at higher speeds so more data can be consumed at much faster rates,” he says. “Thus, increasing the capacity and data flows in and out of the datacenter. So if you have more devices connected and more traffic flows, then you have more potential vulnerabilities derived from the increase in new vectors.”
“It’s going to become more important than ever to have proper monitoring, be able to identify attacks once inside, and have the capability to respond effectively, to remediate any potential issue,” says Lally. “At the end of the day, you’re still looking for anomalies, you’re just going to have more. So the ability to swiftly identify and respond will be critical to minimizing risk.”
It is both valuable and admirable that researchers endeavored to bring the security concerns mentioned here to light. However, it’s crucial for people to remember that 5G is a pioneering technology. Besides these potential problems, there are inevitable risks not anticipated yet in these early stages.
Conversely, there are unforeseen benefits that are more specific than the advantages so often highlighted in media coverage of the 5G network. For example, some of the inventions people rely on soon might not have been possible to develop on older networks. In order to enjoy all those advantages to the fullest, it’s necessary to continually prioritize 5G network security.
References:
UPDATE:
The real work on 5G security is being done by 3GPP with technical specification (TS) 33.501 Security architecture and procedures for 5G system being the foundation 5G security document. That 3GPP spec was first published in Release 16, but the latest version dated 16 December 2020 is targeted at Release 17. You can see all versions of that spec here.
3GPP’s 5G security architecture is designed to integrate 4G equivalent security. In addition, the reassessment of other security threats such as attacks on radio interfaces, signaling plane, user plane, masquerading, privacy, replay, bidding down, man-in-the-middle and inter-operator security issues have also been taken in to account for 5G and will lead to further security enhancements.
Another important 3GPP Security spec is TS 33.51 Security Assurance Specification (SCAS) for the next generation Node B (gNodeB) network product class, which is part of Release 16. The latest version is dated Sept 25, 2020.
Here’s a chart on 3GPP and GSMA specs on 5G Security, courtesy of Heavy Reading: