5G Security Vulnerabilities detailed by Positive Technologies; ITU-T and 3GPP 5G Security specs
Introduction:
Mobile network operators are mostly running 5G non-standalone networks (NSA), which are based on 4G LTE infrastructure. Positive Technologies said these 5G NSA networks are at risk of attack because of long-standing vulnerabilities in the Diameter and GTP protocols, which were reported on by Positive Technologies earlier this year.
“… true 5G security must go beyond the features built into standalone architecture,” said Pavel Novikov, head of the Positive Technologies’ telecom security research team. “Cost efficiencies can be gained by building a hybrid network that supports both 4G LTE and 5G which will enable a future-proofed next generation network in the longer term,” he added.
What will be the 5G security issues/vulnerabilities when mobile network operators move to deploy 5G stand alone networks with a 5G core (rather than 4G EPC used in 5G NSA)?
Background:
Cellular network operators are gradually migrating to 5G standalone infrastructure [T-Mobile US has deployed 5G SA]. but this also has security considerations of its own. Gartner expects 5G investment to exceed LTE/4G in 2022 and that communications service providers will gradually add 5G standalone capabilities to their non-standalone 5G networks.

Source: Positive Technologies’ Standalone 5G core security research
………………………………………………………………………………………………………………………
Discussion:
Vulnerabilities and threats for subscribers and mobile network operators stem from the use of new standalone 5G network cores. The vulnerabilities in protocols HTTP/2 and PFCP, used by standalone 5G networks, include the theft of subscriber profile data, impersonation attacks and faking subscriber authentication.
The stack of 5G technologies potentially leaves the door open to attacks on subscribers and the operator’s network. Such attacks can be performed from the international roaming network, the operator’s network, or partner networks that provide access to services.
For example, the Packet Forwarding Control Protocol (PFCP) that is used to make subscriber connections has several potential vulnerabilities such as denial of service, cutting subscriber access to the internet and redirecting traffic to an attacker, allowing them to downlink the data of a subscriber. Correct configuration of the architecture as highlighted in Positive Technologies GTP protocol research can stop these types of attacks.
The HTTP/2 protocol, which is responsible for vital network functions (NFs) that register and store profiles on 5G networks, also contains several vulnerabilities. Using these vulnerabilities, attackers could obtain the NF profile and impersonate any network service using details such as authentication status, current location, and subscriber settings for network access. Attackers can also delete NF profiles potentially causing financial losses and damaging subscriber trust.
In these cases, subscribers will be unable to take action against threats that lurk on the network, so operators need to have sufficient visibility to safeguard against these attacks.
Dmitry Kurbatov, CTO at Positive Technologies commented: “There is a risk that attackers will take advantage of standalone 5G networks while they are being established and operators are getting to grips with potential vulnerabilities. Therefore, security considerations must be addressed by operators from the offset. Subscriber attacks can be both financially and reputationally damaging – especially when vendors are in high competition to launch their 5G networks. With such a diverse surface of attack, robust core network security architecture is by far the safest way to protect users.
“5G standalone network security issues will be much further reaching when it comes to CNI, IoT and connected cities – putting critical infrastructure such as hospitals, transport and utilities at risk. In order to achieve full visibility over traffic and messaging, operators need to perform regular security audits to detect errors in the configuration of network core components to protect themselves and their subscribers,”
Jimmy Jones, telecoms cybersecurity expert at Positive Technologies, said 5G users will need to increase their lines of communication with mobile operators, analysts and customers as 5G presents new threats and attack surfaces.
“They’re going to need to start speaking to the mobile operators as much as possible, because the mobile operators can secure things and will do everything to secure things. They just need to know what they’re securing,” Jones added.
[This author has spoken at length with Jimmy Jones and can attest to his vast knowledge and experience in cellular network security/vulnerabilities]

Jimmy Jones, Positive Technologies Network Security Expert
Positive Technologies has published a new report titled “5G standalone core security assessment,” which details the vulnerabilities of those networks.
The report focuses on the SA (Standalone) mode of 5G network deployment. “The implementation is based on Rel 15 3GPP with the OpenAPI Specification providing detailed descriptions of each interface,” the researchers explain.
Again, almost all deployed 5G networks are based on NSA which depend on a “4G LTE anchor for all non radio functions, including the 4G EPC (Evolved Packet Core) technology. The 5G core network architecture (but not implementation details) is specified by 3GPP and includes the following Technical Specifications:
| TS 23.501 | System architecture for the 5G System (5GS) |
| TS 23.502 | Procedures for the 5G System (5GS) |
| TS 23.503 | Policy and charging control framework for the 5G System (5GS); Stage 2 |
The 5G mobile network consists of nine network functions (NFs) responsible for registering subscribers, managing sessions and subscriber profiles, storing subscriber data, and connecting user equipment to the Internet using a base station. These technologies create a liability for attackers to carry out man-in-the-middle and DoS attacks against subscribers.
One of the main issues in the system architecture is the interface responsible for session management, known as SMF (Session Management Function). SMF is possible due to a protocol known as PFCP (Packet Forwarding Protocol):
To manage subscriber connections, three procedures are available in the PFCP protocol (Session Establishment, Modification, and Deletion), which establish, modify, and delete GTP-U tunnels on the N3 interface between the UPF and gNB. […] We will focus on the N4 interface. Testing of this interface revealed potential attack scenarios against an established subscriber session.
Other problems Positive Technologies discovered are based on subscriber authentication vulnerabilities. The researchers demonstrated that “subscriber authentication becomes insecure if the NRF does not perform authentication and authori-zation of 5G core network functions.”
In conclusion, this report only covers “a few examples” of how vulnerabilities in G5 can be exploited. “Just as with previous-generation networks, attackers still can penetrate operator networks by means of the international roaming network or partner networks. Therefore, it is vital to ensure comprehensive protection of 5G networks,” the report concludes.
For more information on vulnerabilities of standalone 5G networks, please download the Positive Technologies report here –after filling out a form. …………………………………………………………………………………………………………………..
Editor’s Note: 5G Security Standards (?) and Specifications
Most 5G “professionals” don’t realize that there are no standards for 5G security– either in the radio access network (RAN) or the core network. As ITU is the official standards body for 5G (e.g. IMT 2020.SPECS for the RAN) you’d think the work would be done there. There is some high level 5G security work being done in ITU-T SG 17/Q6, but the corresponding ITU recommendations won’t be completed till late 2021- 2o22 timeframe.
The real work on 5G security is being done by 3GPP with technical specification (TS) 33.501 Security architecture and procedures for 5G system being the foundation 5G security document. That 3GPP spec was first published in Release 16, but the latest version dated 16 December 2020 is targeted at Release 17. You can see all versions of that spec here.
3GPP’s 5G security architecture is designed to integrate 4G equivalent security. In addition, the reassessment of other security threats such as attacks on radio interfaces, signaling plane, user plane, masquerading, privacy, replay, bidding down, man-in-the-middle and inter-operator security issues have also been taken in to account for 5G and will lead to further security enhancements.
Another important 3GPP Security spec is TS 33.51 Security Assurance Specification (SCAS) for the next generation Node B (gNodeB) network product class, which is part of Release 16. The latest version is dated Sept 25, 2020.
Here’s a chart on 3GPP and GSMA specs on 5G Security, courtesy of Heavy Reading:
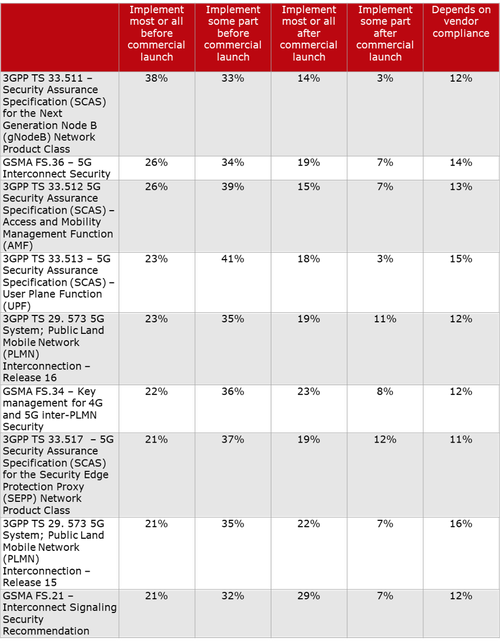
Question to 5G network operators: When do you plan to implement the following 5G security specifications? Source: Heavy Reading
“While 3GPP TS 33.511 had the greatest level of commitment to implementing before commercial launch (38% + 33%), the support for all nine specifications in the list is strong enough to confirm each one is relevant on some level for ensuring the security of 5G networks,” according to Heavy Readings’ Jim Hodges.
………………………………………………………………………………………………………………………
References:
https://sensorstechforum.com/new-5g-vulnerabilities-dos-mitm-attacks/
https://www.ericsson.com/en/blog/2020/6/security-standards-role-in-5g
https://www.itu.int/ITU-T/workprog/wp_search.aspx?&isn_sg=3935&isn_wp=6682&isn_qu=4216&details=0
https://www.3gpp.org/news-events/1975-sec_5g
https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3169
https://www.3gpp.org/ftp//Specs/archive/33_series/33.501/
https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3444
2 thoughts on “5G Security Vulnerabilities detailed by Positive Technologies; ITU-T and 3GPP 5G Security specs”
Comments are closed.



I love this excellent IEEE Techblog post on 5G security vulnerabilities and 5G security standards or lack of same. For cloud native 5G core networks (5G SA), effective 5G security strategies will hinge on the ability to seamlessly run security capabilities anywhere in the cloud. That will be a huge challenge for 5G SA vendors and network operators.
Thanks for this great overview of this huge challenge that clearly needs addressing before 5G becomes entrenched.
To date, licensed wireless networks could be trusted as being secure. This is a big differentiator over WiFi hotspots. It seems like it would be prudent for the big 3 wireless carriers (e.g. AT&T, T-Mobile, Verizon) to lead with security.
That is, they should make sure that 5G security is their common goal before rolling out their respective 5G stand-alone cores. They should work to ensure that the roaming use-case is secure as well. Like safety is with autonomous vehicles, security should be table stakes and something that isn’t a competitive advantage between the wireless carriers.