IEEE/SCU SoE Event
IEEE SCV March 28th Event: A Conversation with IEEE President and IEEE Region 6 Director Elect
A Conversation with IEEE President and IEEE Region 6 Director Elect
Time/Date: 5pm-7:30pm March 28, 2024
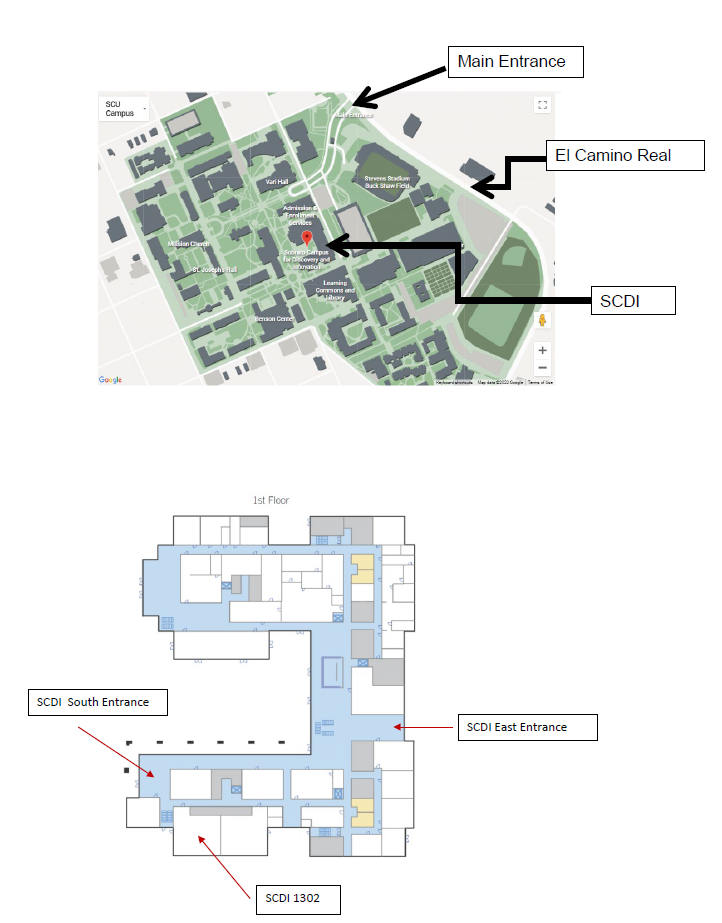
Venue: Santa Clara University Room SCDI 1302 & 1308 (see map for room location)
Register at: https://events.vtools.ieee.org/m/410534
Abstract:
Please join us for a lively and enlightening conversation with IEEE President Tom Coughlin and IEEE Region 6 Director Elect Joseph Wei, moderated by Alan J Weissberger. We will discuss and debate how to make IEEE more relevant to its members, explore volunteer opportunities, ways to elevate the awareness and perception of IEEE as the world’s largest tech non-profit organization.
In the past decade, IEEE membership has significantly declined, there are fewer volunteers, and many IEEE initiatives (e.g. 5G, cloud computing, IoT and smart grid) have fizzled. IEEE Conferences and Journals are now dominated by academia and for the most part are not of interest to industry as the content is not realizable and has little or no practical value. Many engineers, sales and marketing people think that IEEE is irrelevant and won’t help them advance their careers. Clearly, IEEE has been in a severe decline for several years.
How can we turn that around? Can IEEE provide better tools and support for the active volunteers and to grow its professional membership while encouraging student members to upgrade to full membership? How can we retain, encourage and train younger members to volunteer for officer positions and provide fresh leadership? Can we find a more equitable balance between industry and academia for IEEE conferences, publications, and local chapters? What are the important, high priority tech initiatives that IEEE should focus on to ensure success? Finally, can we orchestrate a leadership transition to ensure high priority projects are progressed?

Timeline:
5pm-5:30pm: Registration and Networking
5:30pm-7pm: Opening statements by each participant followed by a conversation/debate about IEEE key issues and initiatives.
7pm-7:25pm: Audience Q & A
7:25pm-7:30pm: Closing remarks and thanks from the participants
……………………………………………………………………………………………………………….
Addendum:
Hope everyone was satisfied with yesterday’s stimulating panel discussion and conversation at SCU. The 3 of us went back & forth discussing critical issues and needed improvements for IEEE to regain credibility & respect. Nothing was rehearsed.
We followed the mutually agreed list of discussion topics (see Comment below) and mixed them up a bit to ensure continuity of various themes.
- Thanks to Behnam, his students, Ed and Joseph for buying the refreshments.
- Thanks to Shoba for securing the SCU room for us.
- Thanks to Kim and Glenn for their cogent comments & remarks
- And many thanks to our two outstanding panelists- Tom and Joseph!!
March 28th video recording of our conversation:
References:
https://techblog.comsoc.org/2024/02/05/ieee-presidents-priorities-and-strategic-direction-for-2024/
https://events.vtools.ieee.org/m/410534
IEEE President Elect: IEEE Overview, 2024 Priorities and Strategic Plan
IEEE/SCU SoE Virtual Event: May 26, 2022- Critical Cybersecurity Issues for Cellular Networks (3G/4G, 5G), IoT, and Cloud Resident Data Centers
This virtual event on ZOOM will be from 10am-12pm PDT on May 26, 2022.
Session Abstract:
IEEE ComSoc and SCU School of Engineering (SoE) are thrilled to have three world class experts discuss the cybersecurity threats, mitigation methods and lessons learned from a data center attack. One speaker will also propose a new IT Security Architecture where control flips from the network core to the edge.
Each participant will provide a 15 to 20 minute talk which will be followed by a lively panel session with both pre-planned and ad hoc/ extemporaneous questions. Audience members are encouraged to submit their questions in the chat and also to send them in advance to [email protected].
Below are descriptions of each talk along with the speaker’s bio:
Cybersecurity for Cellular Networks (3G/4G, 5G NSA and SA) and the IoT
Jimmy Jones, ZARIOT
Abstract:
Everyone agrees there is an urgent need for improved security in today’s cellular networks (3G/4G, 5G) and the Internet of Things (IoT). Jimmy will discuss the legacy problems of 3G/4G, migration to 5G and issues in roaming between cellular carriers as well as the impact of networks transitioning to support IoT.
Note: It’s important to know that 5G security, as specified by 3GPP (there are no ITU recommendations on 5G security), requires a 5G Stand Alone (SA) core network, very few of which have been deployed. 5G Non Stand Alone (NSA) networks are the norm, but they depend on a 4G-LTE infrastructure, including 4G security.
Cellular network security naturally leads into IoT security, since cellular networks (e.g. NB IoT, LTE-M, 5G) are often used for IoT connectivity.
It is estimated that by 2025 we will interact with an IoT device every 18 seconds, meaning our online experiences and physical lives will become indistinguishable. With this in mind it is as critical to improve IoT security as fastening a child’s seatbelt.
The real cost of a security breach or loss of service for a critical IoT device could be disastrous for a business of any size, yet it’s a cost seldom accurately calculated or forecasted by most enterprises at any stage of IoT deployment. Gartner predicts Operational Technologies might be weaponized to cause physical harm or even kill within three years.
Jimmy will stress the importance of secure connectivity, but also explain the need to protect the full DNA of IoT (Device, Network and Applications) to truly secure the entire system.
Connectivity providers are a core component of IoT and have a responsibility to become part of the solution. A secure connectivity solution is essential, with strong cellular network standards/specifications and licensed spectrum the obvious starting point.
With cellular LPWANs (Low Power Wide Area Networks) outpacing unlicensed spectrum options (e.g. LoRa WAN, Sigfox) for the first time, Jimmy will stress the importance of secure connectivity and active collaboration across the entire IoT ecosystem. The premise is that the enterprise must know and protect its IoT DNA (Device, Network & Application) to truly be secure.
Questions from the audience:
I am open to try and answer anything you are interested in. Your questions will surely push me, so if you can let me know in advance (via email to Alan) that would be great! It’s nice to be challenged a bit and have to think about something new.
One item of interest might be new specific IoT legislation that could protect devices and data in Europe, Asia, and the US ?
End Quote:
“For IoT to realize its potential it must secure and reliable making connectivity and secure by design policies the foundation of and successful project. Success in digital transformation (especially where mission and business critical devices are concerned) requires not only optimal connectivity and maximal uptime, but also a secure channel and protection against all manner of cybersecurity threats. I’m excited to be part of the team bringing these two crucial pillars of IoT to enterprise. I hope we can demonstrate that security is an opportunity for business – not a burden.”
Biography:
Jimmy Jones is a telecoms cybersecurity expert and Head of Security at ZARIOT. His experience in telecoms spans over twenty years, during which time he has built a thorough understanding of the industry working in diverse roles but all building from early engineering positions within major operators, such as WorldCom (now Verizon), and vendors including Nortel, Genband & Positive Technologies.
In 2005 Jimmy started to focus on telecom security, eventually transitioning completely in 2017 to work for a specialist cyber security vendor. He regularly presents at global telecom and IoT events, is often quoted by the tech media, and now brings all his industry experience to deliver agile and secure digital transformation with ZARIOT.
…………………………………………………………………………………………………………………………………………………………………………………………………………………….
Title: Flip the Security Control of the Internet
Colin Constable, The @ Company
The PROBLEM:
With the explosion of Internet connected devices and services carrying user data, do current IT architectures remain secure as they scale? The simple and scary answer is absolutely no, we need to rethink the whole stack. Data breaches are not acceptable and those who experience them pay a steep price.
Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to see the actual data being transmitted. However, the Router needs meta data (the IP and Port) to make it work. What meta data does the Data level Router have access to?
We need to discuss how to approach the problem and selectively discard, but learn from previous IT architectures so that we can build a more solid, secure IT infrastructure for the future.
Proposition:
I will provide a glimpse of a future security focused IT architecture.
- We need to move most security control functionality to the edge of the network.
- Cloud data center storage should be positioned as an encrypted cache with encryption keys at the edge.
- No one set of keys or system admin can open all the encrypted data.
When data is shared edge to edge we need to be able to specify and authenticate the person, entity or thing that is sharing the data. No one in the middle should be able to see data in the clear.
Issues with Encryption Keys:
- IT and Data security increasingly rely on encryption; encryption relies on keys; who has them?
- Is there really any point to VPN’s Firewalls and Network segmentation if data is encrypted?
- We use keys for so many things TLS, SSH, IM, Email, but we never tend to think about the keys.
- Do you own your keys? If not someone else can see your data!
- What do we need to flip the way IT is architected?
Recommendations for Keys:
- Keys should be cut at the edge and never go anywhere else.
- You should be able to securely share keys along with the data being transmitted/received.
- There needs to be a new way to think about identity on the Internet.
The above description should stimulate many questions from attendees during the panel discussion.
Biography:
Colin Constable’s passion is networking and security. He was one of the founding members of the Jericho Forum in the 2000s. In 2007 at Credit Suisse, he published “Network Vision 2020,” which was seen by some as somewhat crazy at the time, but most of it is very relevant now. While at Juniper, Colin worked on network virtualization and modeling that blurred the boundaries between network and compute. Colin is now the CTO of The @ Company, which has invented a new Internet protocol and built a platform that they believe will change not just networking and security, but society itself for the better.
……………………………………………………………………………………………………………………….
The Anatomy of a Cloud Data Center Attack
Thomas Foerster, Nokia
Abstract:
Critical infrastructure (like a telecommunications network) is becoming more complex and reliant on networks of inter-connected devices. With the advent of 5G mobile networks, security threat vectors will expand. In particular, the exposure of new connected industries (Industry 4.0) and critical services (connected vehicular, smart cities etc.) widens the cybersecurity attack surface.
The telecommunication network is one of the targets of cyber-attacks against critical infrastructure, but it is not the only one. Transport, public sector services, energy sector and critical manufacturing industries are also vulnerable.
Cloud data centers provide the required computing resources, thus forming the backbone of a telecommunications network and becoming more important than ever. We will discuss the anatomy of a recent cybersecurity attack at a cloud data center, review what happened and the lessons learned.
Questions:
- What are possible mitigation’s against social engineering cyber- attacks?
-Multifactor authentication (MFA)
-Education, awareness and training campaigns
- How to build trust using Operational Technology (OT) in a cloud data center?
Examples:
- Access monitoring
- Audits to international standards and benchmarks
- Security monitoring
- Playbooks with mitigation and response actions
- Business continuity planning and testing
Recommendations to prevent or mitigate DC attacks:
- Privileged Access Management across DC entities
- Individual credentials for all user / device entities
- MFA: One-Time Password (OTP) via text message or phone call considered being not secure 2-Factor Authentication anymore
- Network and configuration audits considering NIST/ CIS/ GSMA NESAS
- Regular vulnerability scans and keep network entities up to date
- Tested playbooks to mitigate security emergencies
- Business continuity planning and establish tested procedures
Biography:
Thomas Foerster is a senior product manager for Cybersecurity at Nokia. He has more than 25 years experiences in the telecommunications industry, has held various management positions within engineering and loves driving innovations. Thomas has dedicated his professional work for many years in product security and cybersecurity solutions.
Thomas holds a Master of Telecommunications Engineering from Beuth University of Applied Sciences, Berlin/ Germany.
……………………………………………………………………………………………………………………………………………………………………………………………………………………………..
Video recording of this event: Critical Cybersecurity Issues for Cellular Networks, IoT, and Cloud-Resident Data Centers – YouTube
Previous IEEE ComSoc/SCU SoE March 22, 2022 event: OpenRAN and Private 5G – New Opportunities and Challenges
Video recording: https://www.youtube.com/watch?v=i7QUyhjxpzE