Dell’Oro: Secure Access Service Edge (SASE) market to hit $13B by 2026; Gartner forecasts $14.7B by 2025; Omdia bullish on security
The secure access service edge (SASE) market is expected to triple by 2026, exceeding $13 billion, representing a very healthy CAGR, according to a new forecast by Mauricio Sanchez, Research Director at the Dell’Oro Group. The report further divides the total SASE market into its two technology components, Security Service Edge (SSE) and SD-WAN with SSE expected to double the SD-WAN revenue for SASE. The report further breaks down the SSE market into FWaaS, SWG, CASB, and ZTNA.
Sanchez wrote in a blog post:
“Today, enterprises are thinking differently about networking and security. Instead of considering them as separate toolsets to be deployed once and infrequently changed, the problem and solution space is conceptualized along a continuum in the emerging view. The vendor community has responded with a service-centric, cloud-based technology solution that provides network connectivity and enforces security between users, devices, and applications.
SASE utilizes centrally-controlled, Internet-based networks with built-in advanced networking and security-processing capabilities. By addressing the shortcomings of past network and security architectures and improving recent solutions—in particular, SD-WAN and cloud-based network security—SASE aims to bring networking and security into a unified service offering.
While the networking technologies underpinning SASE are understood to be synonymous with well-known SD-WAN, the security facet of SASE consists of numerous security technologies, such as secure web gateway (SWG), cloud access security broker (CASB), zero-trust network access (ZTNA), and firewall-as-a-service (FWaaS). Recently, a new term, security services edge (SSE), emerged to describe this constellation of cloud-delivered network security services that is foundational in SASE.”
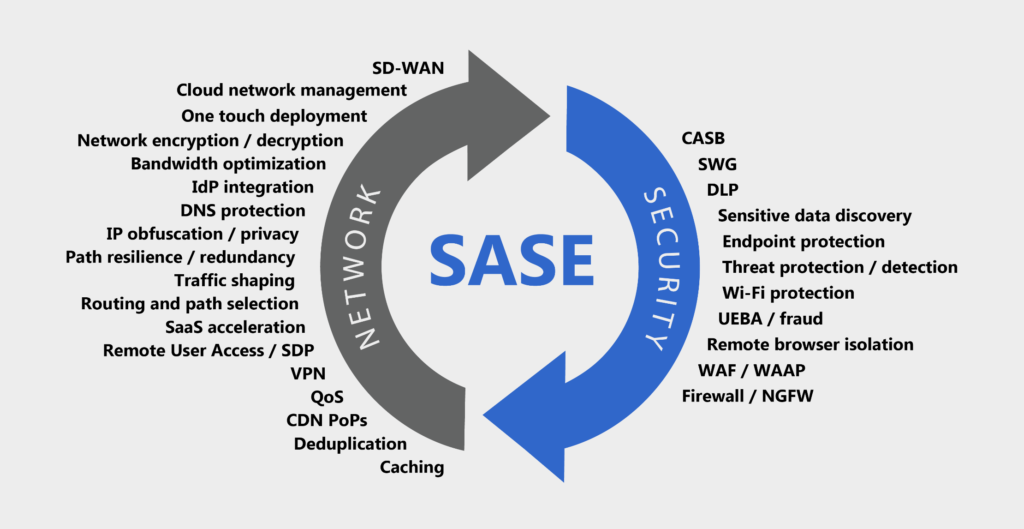
As noted above, Dell’Oro divides the total SASE market into two technology components: Security Service Edge (SSE) and SD-WAN with SSE. Security features such as Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB) and Zero Trust Network Access (ZTNA) fall under the umbrella of SSE, according to Dell’Oro. In addition, Dell’Oro predicts that the security component to SASE “will increasingly be the driver and lead SASE’s SSE to exhibit over twice the growth of SASE’s SD-WAN.”
Dell’Oro’s Sanchez wrote, “We see SASE continuing to thrive independent of the ongoing macro-economic uncertainty as enterprises strategically invest for the new age of distributed applications and hybrid work that need a different approach to connectivity and security. We anticipate that security will increasingly be the driver and lead SASE’s SSE to exhibit over twice the growth of SASE’s SD-WAN.”
Additional highlights from SASE and SD-WAN 5-Year Forecast Report:
- Within SSE, Secure Web Gateway (SWG) and Cloud Access Security Broker (CASB) are expected to remain the most significant revenue components over the five-year forecast horizon, but Zero Trust Network Access (ZTNA) and Firewall-as-a-Service (FaaS) are estimated to flourish at a faster rate.
- Unified SASE is expected to exceed disaggregated SASE by almost 6X.
- Enterprise access router revenue is expected to decline at over 5 percent CAGR over the forecast horizon.
Dell’Oro expects that under the umbrella of SSE, Secure Web Gateway and Cloud Access Security Broker will continue as the most significant revenue components over the five-year forecast horizon. However, Zero Trust Network Access and Firewall-as-a-Service are expected to grow at a faster rate.
Unified SASE, which Dell’Oro qualifies as the portion of the market that delivers SASE as an integrated platform, is expected to exceed disaggregated SASE by almost a factor of six over the next five years. The disaggregated type is defined as a multi-vendor or multi-product implementation with less integration than unified type. Dell’Oro also predicts that enterprise access router revenue could decline at over 5% CAGR by 2026.
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………..
Gartner has a more optimistic forecast of SASE revenue, predicting the market to reach $14.7 billion as early as 2025. “Gartner predicts that global spending on SASE will grow at a 36% CAGR between 2020 and 2025, far outpacing global spending on information security and risk management,” reported VentureBeat last month. According to Gartner, top SASE vendors include Cato Networks, Fortinet, Palo Alto Networks, Versa Networks, VMware and Zscaler.
These disparate predictions could be a result of the nascent nature of the SASE market, a convergence of networking and security services coined by Gartner in 2019. To address the varying definitions for SASE and resulting confusion on the part of enterprise customers, industry forum MEF plans to release SASE (MEF W117) standards this year. MEF started developing its SASE framework in 2020 to clarify service attributes and definitions. (See MEF adds application, security updates to SD-WAN standard and MEF’s Stan Hubbard on accelerating automation with APIs.)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………..
Omdia’s [1.]research also shows security is a major driver for SASE adoption, according to Fernando Montenegro, senior principal analyst with Omdia. “Our own research indicates that end-user organizations value secure web browsing use cases (SWG, CASB, browsing isolation) particularly as they go further into their deployments of SASE projects,” said Montenegro in an email to Light Reading.
Note 1. Omdia and Light Reading are owned by Informa in the UK
Security is critical for organizations in what Omdia calls the age of “digital dominance” and by how the “demands on security teams – both in terms of time and expertise – make the delivery of security functionality via a services model particularly attractive,” Montenegro said.
SASE services also provide “good performance characteristics” when compared to enterprises utilizing their own VPN headends, and especially when hybrid work continues to be popular, added Montenegro.
References:
Total SASE Market to Nearly Triple by 2026, According to Dell’Oro Group
https://start.paloaltonetworks.com/gartner-2022-report-roadmap-for-sase-convergence.html
3 thoughts on “Dell’Oro: Secure Access Service Edge (SASE) market to hit $13B by 2026; Gartner forecasts $14.7B by 2025; Omdia bullish on security”
Comments are closed.



Verizon said in its guide for the “right approach” to secure access service edge (SASE) – the Gartner-coined infrastructure that combines cloud-native network and security stacks- that managing and securing an increasingly complex environment poses “significant challenges.”
https://www.verizon.com/business/resources/T8d/whitepapers/the-right-approach-to-sase.pdf
In 2021 Verizon Business launched SASE solution with a multi-vendor approach that combines SD-WAN and network security capabilities from Versa Networks and Zscaler into a single managed service. Rival AT&T had rolled out its own solution earlier that year in partnership with Fortinet.
Verizon cites the COVID-19 pandemic, virtualization and the move to the cloud, increased security threats, and a shift away from the network appliance box as the primary factors that drove the “SASE frenzy” in recent years.
By 2024, at least 40% of enterprises will have explicit strategies to adopt SASE, up from less than 1% at year-end 2018, according to the Verizon guide.
“Getting SASE right may be a complex proposition that presents significant challenges,” the provider said. “For one thing, it is a still-evolving technology target.”
The SASE architecture combines network edge capabilities like SD-WAN and a set of security capabilities Gartner dubbed the security services edge (SSE) – a cloud-delivered suite that includes zero-trust network access (ZTNA), cloud-access security broker (CASB), secure web gateway (SWG), and firewall-as-a-service (FWaaS).
The major elements that make up SASE have been around in some form or another for “at least 10 years,” Verizon pointed out.
For this reason, a critical component of getting SASE right is cross-technology integration. “There’s no one-size-fits-all SASE solution, which means enterprises will need to be comfortable working with a variety of technologies in order to build an effective implementation that solves a given organization’s specific challenges,” the provider said.
Enterprises adopting SASE need to be able to integrate a broad range of network technologies from physical transport – like private IP and MPLS – up through the virtualization SDN layer in order to build an integrated SD-WAN capability with traffic routing, prioritization, and bandwidth optimization.
Another “key ingredient” to SASE is edge computing like content delivery networks, multi-access edge computing (MEC), or an IoT gateway. “Managing security across these complex and distributed systems will be essential and require a deep understanding of how edge computing fits into the SASE model,” Verizon explained.
Orchestrating SASE Infrastructure
How the technology components of SASE come together is critical.
Verizon recommends enterprises implement service chaining as a key component of SASE because it is a “way of automating and optimizing the service delivery experience.”
In an environment where many vendors are still unable to provide a complete end-to-end SASE solution, organizations likely need to combine technologies and products to create their desired solutions. “Being able to optimize new and already-deployed technology components so each is functioning and contributing at its full potential will be important,” Verizon said.
The ability to conduct testing to make sure SASE is properly integrated and performing at necessary levels will also be critical. Verizon indicated this requires the “proper tools to conduct the integration, performance, and stress testing needed to ensure that functions have been deployed in the optimal order and the most efficient configuration.”
Service chaining and other orchestration in a virtual network requires expertise, which has led to challenges for many organizations in the midst of a global skill shortage. However, this can be mitigated in part through organizational restructuring that sees networking and security teams – which have traditionally operated separately – merge their administration and management from the organizational perspective.
Lastly, Verizon suggested that because SASE is still a work in progress, “CIO and CISO groups will need to rethink their respective roles in supporting enterprise infrastructure operations.”
“Proper governance will be key to success as these changes percolate down through the organization, as they will eventually touch the network architects, security architects, application architects and others that need to work together to execute on a company’s SASE strategy,” Verizon added.
https://www.sdxcentral.com/articles/analysis/verizons-critical-components-to-getting-sase-right/2022/11/
From SDxCentral:
Analysts expect that Secure access service edge (SASE) total worldwide end-user spending will reach $9.2 billion in 2023, marking a 39% increase from 2022.
Gartner, who coined the acronym, also announced its single-vendor SASE leaders. The firm’s definition specifies that a complete SASE offering combines network edge capabilities like SD-WAN, and a set of cloud-centric security service edge (SSE) capabilities, including secure web access gateway (SWG), cloud access security broker (CASB), firewall-as-a-service (FWaaS), and zero-trust network access (ZTNA).
While many vendors still can only supply components of SASE, Gartner recognized nine that offer complete solutions with both networking and SSE capabilities – Cato Networks, Cisco, Citrix, Forcepoint, Fortinet, Netskope, Palo Alto Networks, Versa Networks, and VMware.
Executives from these companies gave SDxCentral their predictions for what 2023 has in store for the SASE market and technologies:
Shlomo Kramer, CEO, Cato Networks
“Just as COVID caused a massive acceleration in digital transformation projects, the recession will accelerate security consolidation. Numerous studies indicate that enterprises maintain dozens of security tools. And with so many security tools, controls are fragmented resulting in reduced visibility; operational overhead increases with the need for extra personnel and skills to master the various tools; and gaps between tools are created leaving the cracks through which attackers can infiltrate. Most companies (75%) expect to reduce the number of security vendors they use, replacing them with one, converged security platform.
Due to recessionary factors, IT staff will be pressured more than ever to do more with less, accelerating the move toward ‘as-a-service’ models. Numerous reports indicate that this recession will be unusual, not marked by the unemployment typical of a recession. But if layoffs are not part of the recession-coping toolbox, organizations will need to find other ways to reduce costs. Adoption of as-a-service models enables IT teams to tap expertise and tools that otherwise would be difficult to onboard.”
Jim Fulton, VP of Product, Forcepoint
“Organizations will further optimize their networking and security for the merging hybrid workforce, and SASE will continue its move into the mainstream as the architecture of choice for those initiatives.
The distinction between single-vendor SASE solutions (SD-WAN and SSE from the same vendor) versus separate SD-WAN and SSE providers will become more prominent as organizations look for ways to simplify their operations during an economic downturn. We will see organizations continue to consolidate vendors and demand platforms that are geared toward reducing the operational burden on security and networking teams, especially during a rocky economy.
Replacing VPNs with ZTNA will accelerate as organizations look to reduce costs and boost control over access to business resources. The role of data security in SASE will continue to grow as organizations realize that it’s not enough to protect how users get to the web, cloud, and private apps. Keeping control of what they do with data after they get there is just as important.”
Nirav Shah, VP of Products, Fortinet
“As the SASE market matures, CIOs will increasingly stop looking at SASE in a silo and examine it as part of their entire infrastructure. We don’t see a cloud-only world in the future, likewise we don’t see an on-premises-only world. SASE is an important cloud-delivered architecture for securing remote access, but it’s important to look at the reality of how most enterprises are building hybrid networks to meet their business needs. That means building a SASE architecture – what is essentially the convergence of cloud-delivered networking and security technologies – with products that are able to seamlessly integrate with each other and with converged on-premises solutions. This ensures enterprises preserve their existing on-premises investments (including SD-WAN investments), and prevents having to completely re-architect everything you already have deployed.
Thinking that convergence only needs to be in the cloud or convergence only needs to be on-premises when you have a hybrid network is not the right way to think – you need both. Many organizations today struggle with complexity because they have taken a piecemeal approach, using disparate tools from multiple vendors to support their security and connectivity needs at headquarters, branch offices, and remote workforce. In 2023, we’ll see more and more CIOs prioritizing consolidation by choosing solutions that can seamlessly integrate across both cloud and on-prem to ensure consistent security and a consistent user experience no matter where users or applications are distributed. We see this same trend manifesting in how CIOs are evaluating ZTNA solutions.”
Naveen Palavalli, VP of Product GTM Strategy, Netskope
“2022 was a challenging year for many organizations, but many are anticipating that 2023 will see continued economic headwinds. As a result, organizations will be looking especially close at how SASE can enable them to continue growing in an optimized, efficient manner. SASE features a number of consolidation and cost-savings benefits, and these will likely feature more heavily in business cases presented to the CIO and executive decision makers, in addition to traditional SASE value drivers like superior user experience or comprehensive security.
Another trend we will see more of in 2023 is the increased adoption of single-vendor SASE solutions by larger organizations. Until recently, these organizations looked primarily at dual-vendor SASE solutions based upon mature, trusted, cloud security platforms and established SD- WAN offerings. However, as complete, robust single-vendor solutions emerge that match or exceed the functionality of their dual-vendor counterparts, these will increase in popularity and market acceptance over the course of the year.
Finally, in 2023, organizations will look to apply some of the evolutionary principles introduced by ZTNA – a fundamental part of SASE – and apply them to the LAN. ZTNA provided remote workers with faster, more secure access to private applications.”
Kumar Ramachandran, SVP Products – Network Security, Palo Alto Networks
“With the recent emergence of multiple single-vendor SASE offerings, these solutions will become preferred over multi-vendor solutions (a.k.a. mix-and-match SASE). This will be driven by increased awareness of the shortcomings of mix- and-match SASE and new capabilities coming from more advanced single-vendor solutions.
Since its introduction earlier this year, ZTNA 2.0 has been gaining traction amongst security-minded early adopters. We expect ZTNA 2.0 to go mainstream in 2023.
The convergence of networking and security solutions, combined with AI and ML, will enable IT teams to predict and resolve issues with applications, networks, and security posture before they cause business disruptions. These cutting-edge capabilities will drive increased productivity and enable IT organizations to go from a reactive to a proactive posture.”
Kelly Ahuja, CEO, Versa Networks
“While the market was initially driven by remote user access to cloud workloads, SASE has emerged as the technology to protect and connect across the entire enterprise footprint. Enterprises are seeking extensible solutions as opposed to point products or technologies that they must integrate themselves. In 2023, SASE solutions that protect enterprise resources while delivering the optimal user/device-to-app or app-to-app experience, simplify policy definition, and add lifecycle management will emerge and establish themselves as the way of future.
SASE has quickly evolved from a set of discrete technologies or functions to a future state blueprint for integrating security and networking. Early adopter enterprises have started their journey to this future state and are charting the course to nirvana. Lessons learned from these early adopters will drive the strategy of the late majority. Their choice of a platform approach versus a portfolio approach will be driven by cost, agility, and operational flexibility. The market opportunity is bigger than it has ever been.”
Karl Brown, Senior Director, VMware
“Enterprise lines of business and operational technology teams are developing new applications or modernizing legacy applications to meet their business objectives. These new applications will collect and process volumes of ephemeral data from a large number and wide array of devices in near real-time. This volume of data and requirements for low latency will mean backhauling data to a cloud or traditional data center is not economically or technically feasible. Thus, requirements for SD-WAN and SASE will expand to encompass several factors.
Connectivity to the edge: Much like connectivity to the cloud, applications at the edge will require a low-latency, secure, and resilient network infrastructure. Further, many new intelligent endpoints will require 5G or 4G LTE LAN connectivity for enhanced mobility, coverage, performance, and reliability.
Compute at the edge: Applications at the edge will require compute capabilities. Deploying dedicated servers is not feasible in many locations because they add to the operational burden while posing security risks. Instead, enterprises should look for SD-WAN and SASE solutions that can host edge applications.
Intelligence about the edge: An understanding of application performance at the edge requires AI-assisted tools given the large volume of endpoints and the increased number of workloads. Therefore AIOps-based functionality is a requirement for SD-WAN and SASE management to function optimally.”
Citrix responded to SDxCentral saying they will be less focused on SASE moving forward, but “rather SSE which is more applicable to their portfolio.” Cisco did not respond to request for comment before publication.
https://www.sdxcentral.com/articles/interview/top-sase-execs-make-2023-predictions/2023/01/
Security Service Edge vs. SASE: What Is the Difference?
Secure Access Service Edge (SASE) is a category of networking solutions defined by Gartner in 2019, which combines traditional network security functions with wide area networking (WAN) capabilities. The goal of SASE is to provide secure and reliable connectivity for users and devices, regardless of their location or the type of network they are connected to.
Gartner defines SASE as a cloud-delivered, network security as a service platform that provides secure network connectivity and network security functions in a unified offering, delivered through a common infrastructure and management. SASE combines network security functions, such as zero trust networking, firewalls, and intrusion prevention systems (IPS), with cloud-based networking services like SD-WAN (software-defined wide area networking) and internet connectivity.
……………………………………………………………………..
Secure Services Edge (SSE) is a set of integrated, cloud-delivered secure services that use identities and policies to establish secure connections between authenticated users and business resources. First introduced by Gartner in 2021, SSE is a security category that will secure connectivity in the future of hybrid environments and remote work.
As more employees work outside corporate boundaries, SaaS applications become the norm, and applications move to the public cloud, organizations cannot continue to backhaul user traffic to corporate networks. Many IT organizations are replacing their existing network security appliances, such as firewalls, VPN gateway appliances, and web gateways, with cloud-based options that can better protect data, provide a better user experience, and reduce costs.
SSE platforms provide cloud services that extend secure connectivity to user locations, without connecting users to corporate networks, exposing IT infrastructure to the public internet, or requiring complex network segmentation. Instead, SSE allows IT to provide secure access from anywhere to on-premise applications, secure access to the internet, and fast access to the cloud and SaaS applications.
………………………………………………………………………………………..
Security Service Edge vs. SASE: What Is the Difference?
The main difference between Secure Access Service Edge (SASE) and Security Service Edge (SSE) is the focus of the solutions. SASE combines traditional network security functions with wide area networking (WAN) capabilities, while SSE focuses specifically on security functions.
SASE solutions are designed to provide secure and reliable connectivity for users and devices, regardless of their location or the type of network they are connected to. This can include traditional networking functions like VPNs and SD-WAN (software-defined wide area networking), as well as security functions like firewalls, intrusion prevention systems (IPS), and other controls. SASE solutions are often used by organizations with remote and hybrid workforces to ensure secure access to corporate resources and protect against cyber threats.
https://wire19.com/security-service-edge-vs-sase-difference/