Evaluating Gaps and Solutions to build Open 5G Core/SA networks
by Saad Sheikh, Vice President and Chief Architect, SouthTel, South Africa
Since the “freezing” of the much awaited 3GPP Release-16 in July 2020, many network equipment vendors have sought to develop 5G core/5G stand alone (5G SA) network capabilities. Those includee network slicing. massive IoT. uRLLC (ultra reliable, ultra low latency communications), edge network computing, NPN (non public network) and IAB (Integrated Access and Backhaul), etc.
It is just natural that all of the big telco’s in APAC and globally have started their journey towards 5G Standalone (5G SA) core network. However, most of the commercial deployments are based on vendor E2E stack which is a good way to start the journey and offer services quickly.
Yet there’s a big caveat: With the type of services and versatility of solution specially on the industry verticals required and expected from both 3GPP Release16 and 5G SA core network it is just a matter of time when network equipment vendors cannot fulfill all the solutions and that is when a dire need to build a Telco grade Cloud platform will become a necessity.
During the last two years we have done a lot of work and progress in both better understanding of what will be the Cloud Native platforms for the real 5G era. As of now, the 5G Core container platforms from an open cloud perspective are not fully ready but we are also not too far from making it happen.
2021 is the year that we expect a production ready open 5G native cloud platform avoiding all sorts of vendor lock ins.
…………………………………………………………………………………………………………………………….
Let’s try to understand top issues enlisted based on 5G SA deployments in Core and Edge network:
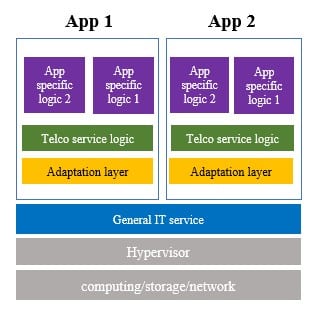
- Vendors are mostly leveraging existing NFVI to evolve to CaaS by using a middle layer shown Caas on Iaas. The biggest challenge is this interface is not open which means there are many out of box enhancements done by each vendor. This is one classic case of “When open became the new closed.”
Reference: https://cntt-n.github.io/CNTT/doc/ref_model/chapters/chapter04.html
The most enhancement done on the adaptors for container images are as follows:
- Provides container orchestration, deployment, and scheduling capabilities.
- Provides container Telco enhancement capabilities: Huge page memory, shared memory, DPDK, CPU core binding, and isolation
- Supports container network capabilities, SR-IOV+DPDK, and multiple network planes.
- Supports the IP SAN storage capability of the VM container.
- Migration path from Caas on IaaS towards BMCaaS is not smooth and it will involve complete service deployment, it is true with most operators investing heavily in last few years to productionize the NFVi no body is really considering to empty pockets again to build purely CaaS new and stand-alone platform however smooth migration must be considered.
- We are still in early phase of 5G SA core and eMBB is only use case so still we have not tested the scaling of 5G Core with NFVi based platforms.
- ETSI Specs for CISM are not as mature as expected and again there are a lot of out of the box. customizations done by each vendor VNFM to cater this.
Now let’s consider where the open platforms are lacking and how that might be fixed.
Experience #1: 5G Outgoing traffic from PoD:
The traditional Kubernetes and CaaS Platforms today handles and scales well with ingress controller however 5G PoD’s and containers outgoing traffic is not well addressed as both N-S and E-W traffic follows same path and it becomes an issue of scaling finally.
We know some vendors like Ericsson who already bring products like ECFE and LB in their architecture to address these requirements.
Experience#2: Support for non-IP protocols:
PoD is natively coming with IP and all external communication to be done by Cluster IP’s it means architecture is not designed for non-IP protocols like VLAN, L2TP, VLAN trunking
Experience#3: High performance workloads:
Today all high data throughputs are supported CNI plugin’s which natively are like SR-IOV means totally passthrough, an Operator framework to enhance real time processing is required something we have done with DPDK in the open stack world
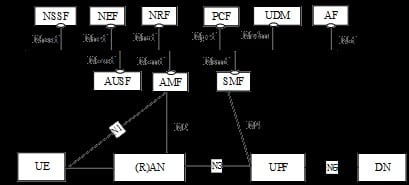
Experience#4: Integration of 5G SBI interfaces:
The newly defined SBI interfaces became more like API compared to horizontal call flows, however today all http2/API integration is based on “Primary interfaces” .
It becomes a clear issue as secondary interfaces for inter functional module is not supported.
Experience#5: Multihoming for SCTP and SI is not supported:
For hybrid node connectivity at least towards egress and external networks still require a SCTP link and/or SIP endpoints which is not well supported
Experience#6: Secondary interfaces for CNF’s:
Secondary interfaces raise concerns for both inter-operability, monitoring and O&M, secondary interfaces is very important concept in K8S and 5G CNF’s as it is needed during
- For all Telecom protocols e.g BGP
- Support for Operator frameworks (CRD’s)
- Performance scenarios like CNI’s for SR-IOV
Today, only viable solution is by NSM i.e. a service mesh that solves both management and monitoring issues.
Experience#7: Platform Networking Issues in 5G:
Today in commercial networks for internal networking most products are using Multus+VLAN while for internal based on Multus+VxLAN it requires separate planning for both underlay and overlay and that becomes an issue for large scale 5G SA Core Network
Similarly, top requirements for service in 5G Networks are the following:
- Network separation on each logical interface e.g VRF and each physical sub interface
- Outgoing traffic from PoD
- NAT and reverse proxy
Experience#8: Service Networking Issues in 5G:
For primary networks we are relying on Calico +IPIP while for secondary network we are relying ion Multus
Experience#9: ETSI specs specially for BM CaaS:
Still I believe the ETSI specs for CNF’s are lacking compared to others like 3GPP and that is enough to make a open solution move to a closed through adaptors and plugin’s something we already experienced during SDN introduction in the cloud networks today a rigorous updates are expected on
- IFA038 which is container integration in MANO
- IFA011 which is VNFD with container support
- Sol-3 specs updated for the CIR (Container image registry) support
Experience#10: Duplication of features on NEF/NRM and Cloud platforms:
In the 5G new API ecosystem operators look at their network as a platform opening it to application developers. API exposure is fundamental to 5G as it is built into the architecture natively where applications can talk back to the network, command the network to provide better experience in applications however the NEF and similarly NRF service registry are also functions available on platforms. Today it looks a way is required to share responsibility for such integrations to avoid duplicates.
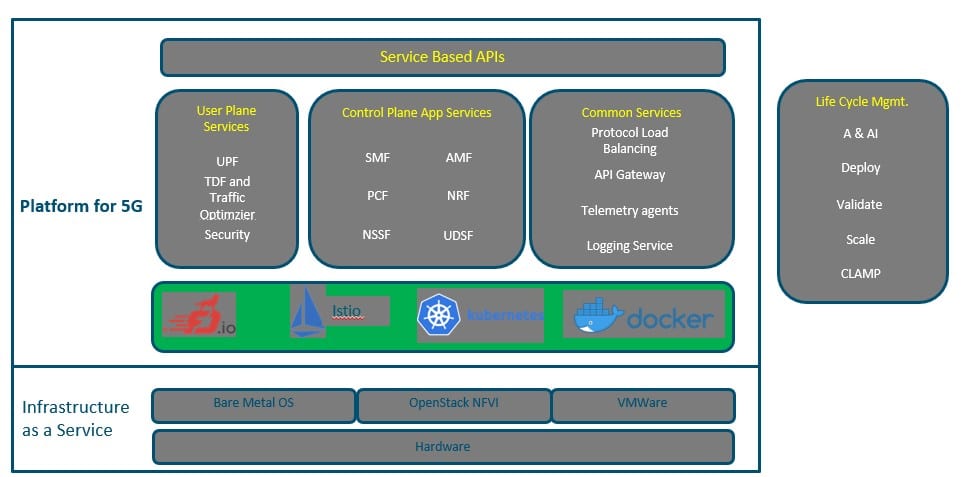
Reference Architectures for the Standard Platform:
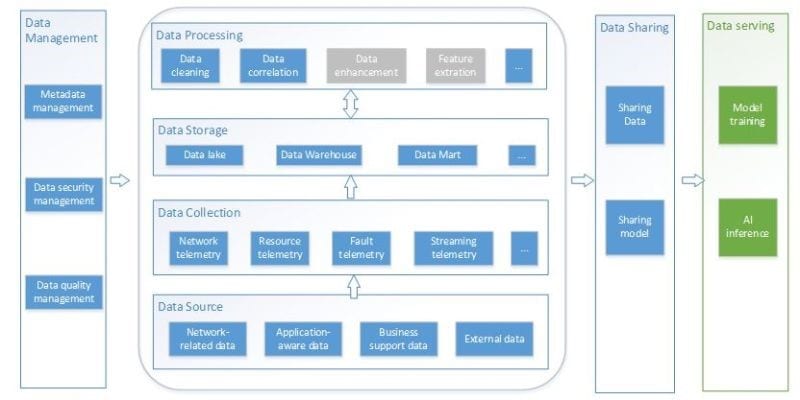
Sol#1: Solving Data Integration issues
Real AI is the next most important thing for telco’s as they evolve in their automation journey from conditional #automation to partial autonomy . However to make any fully functional use case will require first to solve #Data integration architecture as any real product to be successful with #AI in Telco will require to use Graph Databases and Process mining and both of it will based on assumption that all and valid data is there .
Sol#2: AI profiles for processing in Cloud Infra Hardware profiles
With 5G networks relying more on robust mechanisms to ingest and use data of AI , it is very important to agree on hardware profiles that are powerful enough to deliver AI use cases to deliver complete AI pipe lines all the way from flash base to tensor flow along with analytics .
Sol#3: OSS evolution that support data integration pipeline
To evolve to future ENI architecture for use of AI in Telco and ZSM architecture for the closed loop to be based on standard data integration pipeline like proposed in ENI-0017 (Data Integration mechanisms).
Sol#4: Network characteristics
A mature way to handle outgoing traffic and LB need to be included in Telco PaaS.
Sol#5: Telco PaaS
Based on experience with NFV it is clear that IaaS is not the Telco service delivery model and hence use cases like NFVPaaS has been in consideration for the early time of NFV . With CNF introduction that will require a more robust release times it is imperative and not optional to build a stable Telco PaaS that meet Telco requirements. As of today, the direction is to divide platform between general PaaS that will be part of standard cloud platform over release iterations while for specific requirements will be part of Telco PaaS.
The beauty of this architecture is no ensure the multi-vendor component selection between them. The key characteristics to be addressed are discussed below.
Paas#1: Telco PaaS Tools
The agreement on PaaS tools over the complete LCM , there is currently a survey running in the community to agree on this and this is an ongoing study.
Reference: https://wiki.anuket.io/display/HOME/Joint+Anuket+and+XGVELA+PaaS+Survey
Paas#2: Telco PaaS Lawful interception
During recent integrations for NFV and CNF we still rely on Application layer LI characteristics as defined by ETSI and with open cloud layer ensuring the necessary LI requirements are available it is important that PaaS include this part through API’s.
Paas#3: Telco PaaS Charging Characteristics
The resource consumption and reporting of real time resources is very important as with 5G and Edge we will evolve towards the Hybrid cloud.
Paas#4: Telco PaaS Topology management and service discovery
A single API end point to expose both the topology and services towards Application is the key requirement of Telco PaaS
Paas#5: Telco PaaS Security Hardening
With 5G and critical services security hardening has become more and more important, use of tools like Falco and Service mesh is important in this platform
Paas#6: Telco PaaS Tracing and Logging
Although monitoring is quite mature in Kubernetes and its Distros the tracing and logging is still need to be addressed. Today with tools like Jaeger and Kafka /EFK needs to be include in the Telco PaaS
Paas#7: Telco PaaS E2E DevOps
For IT workloads already the DevOps capability is provided by PaaS in a mature manner through both cloud and application tools but with enhancements required by Telco workloads it is important the end-to-end capability of DevOps is ensured. Today tools like Argo need to be considered and it need to be integrated with both the general PaaS and Telco PaaS
Paas#9: Packaging
Standard packages like VNFD which cover both Application and PaaS layer.
Paas#8: Standardization of API’s
API standardization in ETSI fashion is the key requirement of NFV and Telco journey and it needs to be ensured in PaaS layer as well. For Telco PaaS it should cover VES , TMForum,3GPP , ETSI MANO etc . Community has made following workings to standardize this
- TMF 641/640
- 3GPP TS28.532 /531/ 541
- IFA029 containers in NFV
- ETSI FEAT17 which is Telco DevOps
- ETSI TST10 /13 for API testing and verification
Based on these features there is an ongoing effort with in the LFN XGVELA community and I hope more and more users, partners and vendors can join to define the Future Open 5G Platform
Reference: https://github.com/XGVela/XGVela/wiki/XGVela-Meeting-Logistics
 ………………………………………………………………………………………………………………………………….
………………………………………………………………………………………………………………………………….
Glossary:
|
Term |
Description |
|
NFV |
Network Function Virtualization |
|
VNF |
Virtual Network Functions |
|
CNF |
Containerized Network Functions |
|
UPF |
User Plane Function |
|
AMF |
Access Management Function |
|
TDF |
Traffic Detection Function |
|
PCF |
Policy Charging Function |
|
NSSF |
Network Slice Subnet Function |
|
UDSF |
Unstructured Data Storage Function |
|
A & AI |
Active and Available Inventory |
|
CLAMO |
Control Loop Automation Management Function |
|
NFVI |
Network Function Virtualized Infrastructure |
|
SDN |
Software Defined Networks |
|
VLAN |
Virtual LAN |
|
L2TP |
Layer2 Tunneling Protocol |
|
SBI |
Service Based Interface |
|
NRF |
Network Repository Function |
|
NEF |
Network Exposure Function |
|
NAT |
Network Address translation |
|
LB |
Load Balance |
|
HA |
High Availability |
|
PaaS |
Platform as a Service |
|
ENI |
Enhanced Network Intelligence |
|
ZSM |
Zero touch Service Management |
|
EFK |
Elastic search, FLuentd and Kibana |
|
API |
Application Programming Interface |
………………………………………………………………………………………………………………………………..
About Saad Sheikh:
Saad Sheikh is an experienced telecommunications professional with more than 18 years of experience for leading and delivering technology solutions . He is currently Vice President and Chief Architect with Southtel, which is the leading System integrator in South Africa. There he is leading 5G, Cloud, Edge Networking, Open RAN, Networking and Automation units. He is helping to bring the power of innovative solutions to Africa.
Prior to this he was Chief Architect with STC (Saudi Telecom Company) where he lead the company Cloud Infrastructure Planning and Architecture Design to deliver large scale 5G , NFV , SDN and Cloud projects in Middle East. Previously, he held senior positions with both vendors and operators in Asia, Africa and APAC driving large scale projects in IT and Telecom.
One thought on “Evaluating Gaps and Solutions to build Open 5G Core/SA networks”
Comments are closed.




June 23, 2021 email from Dave Bolan of Dell’Oro Group:
All of 5G Core will be Cloud-Native, mostly Container-based. Except there are different cloud-native versions and container versions, not making it truly open. Anyone that wants to put their core on the public cloud will have to customize it for each cloud platform. Same may be true for the NFVI if it runs on – x86, AMD, ARM, or Nvidia – and couple that with the different UPF acceleration techniques, it gets complex very quickly.