5G Network Slicing
Google Fiber and Nokia demo network slicing for home broadband in GFiber Labs
Network slicing has previously been restricted to 5G Stand Alone (SA) networks, which the IEEE Techblog regularly covers (see References below). However, network slicing software may also have a place in the home broadband network, as per a demo from Google Fiber and Nokia. Google Fiber says that this use of “network slicing gives us the ability to carve up a customer’s home network into different “lanes,” each optimized for a specific use.” In a GFiber Labs demo, gaming was used as the test scenario.
Google Fiber placed two gaming consoles next to each other and simulated network congestion, which drove the game’s latency up to 90 milliseconds. Unsurprisingly, “it was stalling, pixelating…a really ill experience for the end user,” said Nick Saporito, Google Fiber’s head of product. “This was a foundational test and it worked,” he added.

In the long-term, this could truly change how home internet works, especially when it’s driven by the customer. Today’s one-size-fits-all connections treat all traffic the same. But we know not everyone uses the internet the same way: gamers care about latency, remote workers need video stability, home businesses rely on solid uptime and security, and, we can see a future where applications (AI, VR, etc.) may require next-level performance. Network slicing could be how we level up network performance.
Network slicing opens the door to something new: the ability for customers to tailor their connection to the categories of Internet use that matter most in their home. It’s not about prioritizing traffic behind the scenes, it’s about giving you more control, more flexibility, and more ways to get the performance you need, when you need it. And with GFiber, it will always be in service of giving customers more control, without compromising our commitment to an open, unrestricted internet.
There’s also potential for something called “transactional slices.” These would spin up automatically, just for a few seconds, to keep things like financial logins secure. For example, connecting you directly to a service like your bank without routing traffic across the broader internet. You wouldn’t even notice it happening, but it could add meaningful peace of mind.
Network slicing is the next logical step in how we think about GFiber service — especially our lifestyle products like Core, Home, and Edge, built to meet the needs of customers’ unique internet lifestyles. Those products are designed to better match the way people live and work. Network slicing takes that a step further: adding real-time customization and control at the network level.
While we’re very excited about the possibilities here, there are few things that have to happen before we roll out network slicing across our network. Automation is a key piece of the puzzle. We’ll be diving deeper with Nokia later this year to explore how we can bring some of these ideas to life. This kind of innovation is exactly what GFiber Labs was built for and we’re excited about potentially leveling up the GFiber customer experience — again.
When considering how to implement network slicing on a wider scale, Saporito noted two key challenges. First, “a lot” of network automation is required to ensure a seamless experience. Google Fiber currently has a “mini-app” that lives on the router to help on the automation front, so that a technician doesn’t have to log onto the router and manually configure the settings.
Another challenge is determining how to effectively sell network slicing capabilities to customers. Given how prevalent multi-gig internet has become, Google Fiber is thinking about whether it makes sense to give customers more “ISP-like controls over their pipe,” Saporito said, rather than just providing a one-size-fits-all product.
“Much like you can put your car in sport or comfort mode, maybe our customers could go to the GFiber app and put their internet in gaming mode, for example, and then all their gaming traffic is special handled by network slicing,” he explained. “Those are ways that we’re kind of thinking about how we would productize it.”
But widespread adoption of broadband network slicing is still a ways away, according to Dell’Oro Group VP Jeff Heynen, as most ISPs and equipment providers are still in the proof-of-concept phase. “That being said, if you look down the road and you don’t expect downstream bandwidth consumption to grow as quickly as it historically has, then network slicing could be a way to help ISPs charge more for their service or, less likely, charge for specific slices,” Heynen said.
Aside from improving gaming or AI applications, one interesting use case for slicing is to provide additional security around financial transactions, Heynen noted. An operator could create a slice on a “per-transaction basis,” complementing a more standard encryption method like SSL.
“You could imagine an ISP differentiating themselves from their competition by highlighting that they have the most secure broadband network, for example,” he added. Saporito similarly noted the value of a so-called “transactional slice.” Though Google Fiber has yet to demo the concept, the idea is to create a temporary slice that would work when a customer logs onto their bank account. “We could create an automatic slice in the background to where that banking traffic is going directly to the financial institution’s back-end, versus traversing the transport network,” he said. “The customer wouldn’t even really notice it.”
https://fiber.google.com/blog/2025/06/network-slicing-demo.html
https://www.fierce-network.com/broadband/google-fiber-puts-nokia-network-slicing-technology-test
Téral Research: 5G SA core network deployments accelerate after a very slow start
5G network slicing progress report with a look ahead to 2025
ABI Research: 5G Network Slicing Market Slows; T-Mobile says “it’s time to unleash Network Slicing”
Is 5G network slicing dead before arrival? Replaced by private 5G?
5G Network Slicing Tutorial + Ericsson releases 5G RAN slicing software
5G network slicing progress report with a look ahead to 2025
The “true” version of 5G is 5G standalone (SA), which eliminates the need for a 4G anchor network and supports all 3GPP defined 5G functions, like 5G Security, Voice over 5G New Radio (VoNR) and network slicing. As we’ve noted for years, 5G SA has proven difficult to deploy, partially because there are no standards for implementation – only 3GPP 5G Architecture specs (rubber stamped as ETSI standards, but never submitted to the ITU for consideration as one or more ITU-T recommendations).
Network slicing is only possible with a 5G SA core network. Operators which have deployd 5G SA are using and planning to use 5G network slices for a variety of use cases, including: a priority slice for first responders, support financial or mission-critical applications, or offer broadcasters a dedicated fast 5G layer to transfer video from cameras to production teams at sporting or other live events.

Image Credit: SDx Central
……………………………………………………………………………………………………………….
In the U.S., T-Mobile is the only major carrier offering 5G SA and has been moving forward with network slicing deployments. Verizon said recently that its 5G network slicing public safety field demonstration in Phoenix, Arizona, is operational but still in trials. AT&T has tested prioritized access to its network, but so far has not yet provided a 5G SA network to support network slicing . That’s despite outsourcing development to Microsoft Azure cloud platform in June 2021.
T-Mobile recently launched “T-Priority,” a network slice for first responders supported by the network operator’s 5G SA core network. The wireless telco told regulators at the end of 2023:
“Network slicing involves creating customized, software-defined, virtual networks – or ‘slices’ – that are each logically separated and individually optimized to meet the specific needs of each application. Within a slice, network functions are defined in software and customized to the use case supported by that slice. For example, network slicing allows providers to use a single 5G network to deliver high-intensity network resources to support a small number of robots on a factory floor, while at the same time delivering low-intensity network resources to a very large number of meter-reading sensors on a utility network.”
Overseas, BT, Orange Belgium, Singtel, China Telecom, Reliance Jio, and Telia Finland have deployed network slicing, among other 5G carriers. Singtel’s app-based network slicing is designed to improve the performance of consumer and enterprise applications.
Nokia recently said it tested a network slicing application with network operator Liberty Global and Belgian shipping company Seafar. Nokia said the shipping company could use its API platform to purchase an ultra-low latency slice of Liberty Global’s Telenet 5G standalone network to maneuver Seafar’s ships through ports without having to slow down.
“Slicing will be critical to enabling enterprise cases and providing network solutions for many use cases for which a stand-alone purpose-built network is not feasible,” Nokia stated in a February meeting between CEO Pekka Lundmark and a variety of top FCC officials, including FCC Chairwoman Jessica Rosenworcel.
The GSMA, which is NOT a standards development organization, launched its “Open Gateway” campaign last year. Earlier this year the group said that 47 mobile operators representing 239 mobile networks and 65% of wireless connections around the world have signed up. Currently, GSMA and its partners are developing a wide range of APIs for text messaging, location information, billing, quality of service – and network slicing among other applications.
Several analysts believe that network slicing will see more growth next year:
“There will be definitely more rollouts of network slicing capabilities as 5G SA networks mature, and as 5G NSA networks move to SA in the next few years,” AvidThink principal analyst Roy Chua said in an email. “Using a network slice for privacy/security/isolation or for ensuring QoS (live broadcasts, sporting events, emergency and disaster support) will likely continue.”
Lead analyst at Techsponential Avi Greengart agreed that more network slicing deployments will happen in the coming year as more operators upgrade to 5G SA. “Network slicing has been a long-touted feature of 5G, and we’re starting to see it used for large venues (ex: sports stadiums) and public safety,” he told Fierce Network. Greengart warned that slicing is not a panacea for private networks or Wi-Fi.
“I do think that network slicing will be operator specific,” noted neXt Curve executive analyst Leonard Lee. “There is still the open question of what the generally monetizable services will be and the scenarios that make them viable. This, each operator will be answering for themselves on their own timeline. For outside observers, it will be like watching a kettle boil,” he said, adding a note of caution.
References:
https://www.lightreading.com/network-automation/2025-preview-network-slicing-gets-real
https://www.fierce-network.com/wireless/network-slicing-slides-more-vigorously-2025
https://www.sdxcentral.com/5g/definitions/key-elements-5g-network/5g-network-slicing/
FCC Draft Net Neutrality Order reclassifies broadband access; leaves 5G network slicing unresolved
ABI Research: 5G Network Slicing Market Slows; T-Mobile says “it’s time to unleash Network Slicing”
Telstra achieves 340 Mbps uplink over 5G SA; Deploys dynamic network slicing from Ericsson
Ericsson, Intel and Microsoft demo 5G network slicing on a Windows laptop in Sweden
Is 5G network slicing dead before arrival? Replaced by private 5G?
5G Network Slicing Tutorial + Ericsson releases 5G RAN slicing software
Latest Ericsson Mobility Report talks up 5G SA networks and FWA
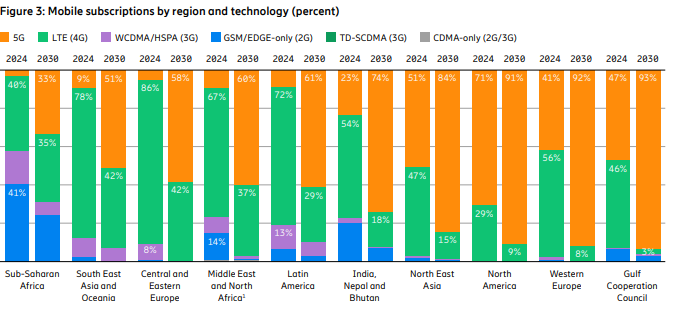
Ericsson’s November 2024 Mobility Report predicts that global 5G standalone (SA) connections will top 3.6 billion by 2030. That compares to 890 million at the end of 2023. Over that same period of time, 5G SA as a proportion of global mobile subscriptions is expected to increase from 10.5% to 38.4%, while average monthly smartphone data consumption will grow to 40 GB from 17.2 GB. By the end of the decade, 80% of total mobile data traffic will be carried by 5G networks.
That rosy forecast is in sharp contrast to the extremely slow and disappointing pace of 5G SA deployments to date. In January, Dell’Oro counted only 12 new 5G SA deployments in 2023, compared to the 18 in 2022. “The biggest surprise for 2023 was the lack of 5G SA deployments by AT&T, Verizon, British Telecom EE, Deutsche Telekom, and other Mobile Network Operators (MNOs) around the globe. As we’ve stated for years, 5G SA is required to realize 5G features like security, network slicing, and MEC to name a few.”
Fifty 5G Standalone enhanced Mobile Broadband (eMBB) networks commercially deployed (2020 – 2023):
The report states, “Although 5G population coverage is growing worldwide, 5G mid-band is only deployed in around 30% of all sites globally outside of mainland China. Further densification is required to harness the full potential of 5G.” Among the report highlights:
- Global 5G subscriptions will reach around 6.3 billion in 2030, equaling 67% of total mobile subscriptions.
- 5G subscriptions will overtake 4G subs in 2027.
- 5G is expected to carry 80% of total mobile data traffic by the end of 2030.
- 5G SA subscriptions are projected to reach around 3.6 billion in 2030.
Source: Ericsson Mobility Report -Nov 2024
“Service differentiation and performance-based opportunities are crucial as our industry evolves,” said Fredrik Jejdling, EVP and head of Ericsson’s networks division. “The shift towards high-performing programmable networks, enabled by openness and cloud, will empower service providers to offer and charge for services based on the value delivered, not merely data volume,” he added.
The Mobility Report provides two case studies in T-Mobile US and Finland’s Elisa – both of which have rolled out network slicing on their 5G SA networks and co-authored that section of the report:
- T-Mobile has been testing a high priority network slice to carry mission-critical data during special events.
- Elisa has configured a slice to support stable, high-capacity throughput for users of its premium fixed-wireless access (FWA) service, called Omakaista.
The Mobility Report doesn’t say if those two telcos are deriving any monetary benefit from network slicing, or more broadly from their 5G SA networks.
……………………………………………………………………………………………………………………………………………………………………………………………………………..
The Fixed Wireless Access (FWA) market has momentum:
- Ericsson predicts FWA connections will reach 159 million this year, up from 131 million in 2023.
- By 2030, connections are expected to hit 350 million, with 80% carried by 5G networks.
- In four out of six regions, 83% or more wireless telcos now offer FWA.
- The number of FWA service providers offering speed-based tariff plans – with downlink and uplink data parameters similar to cable or fiber offerings – has increased from 30% to 43% in the last year alone.
- An updated Ericsson study of retail packages offered by mobile service providers reveals that 79% have a FWA offering.
- There are 131 service providers offering FWA services over 5G, representing 54 percent of all FWA service providers.
- In the past 12 months, Europe has accounted for 73%of all new 5G FWA launches globally.
- Currently, 94% of service providers in the Gulf Cooperation Council region offer 5G FWA services.
- In the U.S. two service providers (T-Mobile US and Verizon) originally set a goal to achieve a combined 11–13 million 5G FWA connections by 2025. After reaching this target ahead of schedule, they have now revised their goal to 20–21 million connections by 2028.
- The market in India is rapidly accelerating, with 5G FWA connections reaching nearly 3 million in just over a year since launch. • An increasing number of service providers are launching FWA based on 5G standalone (SA).
References:
https://www.ericsson.com/en/reports-and-papers/mobility-report/reports/november-2024
https://www.ericsson.com/4ad0df/assets/local/reports-papers/mobility-report/documents/2024/ericsson-mobility-report-november-2024.pdf
5G Advanced offers opportunities for new revenue streams; 3GPP specs for 5G FWA?
FWA a bright spot in otherwise gloomy Internet access market
Where Have You Gone 5G? Midband spectrum, FWA, 2024 decline in CAPEX and RAN revenue
GSA: More 5G SA devices, but commercial 5G SA deployments lag
Vodafone UK report touts benefits of 5G SA for Small Biz; cover for proposed merger with Three UK?
Building and Operating a Cloud Native 5G SA Core Network
How Network Repository Function Plays a Critical Role in Cloud Native 5G SA Network
NRF (Network Repository Function) facilitates cloud-native 5G networks by enabling dynamic and efficient discovery of peer Network Functions, enhancing scalability.
Ajay Lotan Thakur
Introduction:
DNS (Domain Name Service) has been widely used by networks to discover 3G and 4G Network Functions (NFs). Every time there is a change in the network, this entails adding or updating records in the DNS server. This solution was not cohesive. The 5G Network Repository Function (NRF), which was introduced in the 5G specification, addresses this issue. Every Network Function needs to register its profile with NRF when it’s ready to service the APIs. Every NF type contains unique information in the NF profile. For example, Session Management Function (SMF) might provide the set of Data Network Names (DNN) it serves.
It’s important to note is that SMF may still choose User Plane Function (UPF) using proprietary logic because the UPF interface to NRF is still optional. In this article we shall see various advantages provided by 3GPP’s NRF network function over traditional 3G/4G networks.
Advantages of 5G NRFs:
Using 5G Network Resource Function (NRF) for discovering peer Network Functions (NFs) compared to relying on DNS servers in 4G networks brings several advantages:
- Efficiency in Resource Discovery: NRF offers a more efficient and dynamic way of discovering peer NFs within the network. Unlike DNS servers, which rely on static records and hierarchical lookup mechanisms, NRF enables direct discovery of available NFs, reducing latency and enhancing resource utilization. NRF can search the NFs based on many parameters like load, slice Ids, DNN name etc.
- Enhanced Security: NRF can incorporate security features such as authentication and authorization mechanisms, ensuring that only authorized NFs can be discovered and accessed. This helps in mitigating security threats such as DNS spoofing or cache poisoning, which are concerns in traditional DNS-based architectures.
- Support for Network Slicing: NRF is well-suited for 5G network slicing, where multiple virtualized networks coexist on the same physical infrastructure. It allows for efficient discovery and allocation of NFs specific to each network slice, enabling tailored services and resource optimization.
- Service Orchestration: NRF facilitates service orchestration by providing real-time information about the available NFs and their capabilities. This enables dynamic service composition and adaptation based on changing network conditions and application requirements. NRF can be used to put some of the NFs under maintenance mode as well.
- Low Latency: With NRF, the latency in discovering and connecting to peer NFs is significantly reduced compared to DNS-based approaches. This is crucial for applications requiring real-time communication or low-latency services, such as edge computing or autonomous vehicles. In case NRF is overloaded then it can scale-out to bring down the latency.
- Scalability: NRF architecture is designed to handle the scalability demands of 5G networks, where the number of NF instances and their dynamic nature can be high. It allows for efficient scaling of network resources without relying on centralized DNS servers, which may face scalability challenges under heavy loads. This allows Network Functions to implement dynamic scale in & scale out without touching any DNS servers.
- Dynamic Network Updates: NRF supports dynamic updates of network information, allowing for real-time changes in the availability and status of NF instances. These are NRF notifications supported as per 3gpp specification. In contrast, DNS records may require time to propagate changes across the network, leading to potential inconsistencies or delays in service discovery. Each NF can update its profile as and when it sees changes.
Conclusions:
Overall, leveraging NRF for NF discovery in 5G networks offers improved efficiency, scalability, low latency, security, and support for advanced network functionalities compared to relying solely on DNS servers in 4G networks.
References:
3GPP TS 23.501 – System Architecture for the 5G System
3GPP TS 29.510 – Network Function Repository Services
GSA: More 5G SA devices, but commercial 5G SA deployments lag
Global 5G Market Snapshot; Dell’Oro and GSA Updates on 5G SA networks and devices
Ericsson Mobility Report touts “5G SA opportunities”
Analysys Mason: 40 operational 5G SA networks worldwide; Sub-Sahara Africa dominates new launches
Samsung and VMware Collaborate to Advance 5G SA Core & Telco Cloud
5G SA networks (real 5G) remain conspicuous by their absence
GSM 5G-Market Snapshot Highlights – July 2023 (includes 5G SA status)
About the Author:
Ajay Lotan Thakur, Senior IEEE Member, IEEE Techblog Editorial Board Member, BCS Fellow, TST Member of ONF’s open source Aether (Private 5G) Project, Cloud Software Architect at Intel Canada.

Blog post edited by Alan J Weissberger
FCC Draft Net Neutrality Order reclassifies broadband access; leaves 5G network slicing unresolved
Introduction:
The FCC will take a series of steps to reestablish the commission’s net neutrality framework and reclassify broadband internet access service (BIAS) as a Communications Act Title II telecom service in a 434 page declaratory ruling and order which doesn’t resolve the issue of network slicing as a paid priority 5G service.
A draft of the items to be considered during the agency’s April meeting, released Thursday, would establish “broad” and “tailored” forbearance for ISPs. “Access to broadband Internet is now an unquestionable necessity. We also exercise broad forbearance for broadband providers as part of the Title II reclassification. Since the Commission’s abdication of authority over broadband in 2017, there has been no federal oversight over this vital service. This item would reestablish the Commission’s authority to protect consumers and safeguard the fair and open Internet, which protects free expression, encourages competition and innovation, and is critical to public safety and national security.”
Network Slicing:
The draft doesn’t make a final determination on how network slicing should be treated under the rules. Network slicing, which requires a 5G SA core network, enables 5G network operators to create multiple virtual networks on top of a shared network. How slicing should be treated has been hotly contested.
“To the extent network slicing falls outside of BIAS, we will closely monitor these uses to evaluate if they are providing the functional equivalent of BIAS, being used to evade our open Internet rules, or otherwise undermining investment, innovation, competition, or end-user benefits in the Internet ecosystem,” the draft said.
“The record reflects that the potential use cases for network slicing are still under development” and that carriers “are in the early stages of adopting the technique, with some moving more quickly than others. Given the nascent nature of network slicing, we conclude that it is not appropriate at this time to make a categorical determination regarding all network slicing and the services delivered through the use of network slicing.”
Yet the document also says it agrees with NCTA “that we ‘should not allow network slicing to be used to evade [the] Open Internet rules.’”
“The FCC declined to do what either side wanted” on slicing, New Street’s Blair Levin stated in a note to investors. “While this was not the clear, decisive win the wireless providers may have hoped for, we don’t believe this or a future FCC is likely to crack down on the primary uses of network slicing, which we understand to be network management techniques that better match wireless services to specific needs in ways that increase spectrum utilization.”
“The text left me rather confused more than reassured,” Digital Progress Institute President Joel Thayer said Friday. The commission seems interested in addressing slicing case by case, he said: “This does not bode well for consumer-facing uses of slicing as that tech starts to develop.”
One implication is the FCC might crack down on slicing if the agency sees it as a form of paid prioritization of network traffic, said Jonathan Cannon, R Street Institute policy counsel-technology and innovation and former aide to FCC Commissioner Nathan Simington.
The report and order would: “Reinstate straightforward, clear rules that prohibit blocking, throttling, or engaging in paid or affiliated prioritization arrangements, and adopt certain enhancements to the transparency rule.”
………………………………………………………………………………………………………………
The new FCC order would adopt “conduct-based rules” in the commission’s net neutrality framework, establishing “bright-line rules to prohibit blocking, throttling, and paid prioritization” by ISPs. An accompanying draft report and order would also reinstate a general conduct standard and establish a “multi-faceted enforcement framework.”
The draft declaratory ruling would officially reclassify broadband as a Title II service, saying the step would allow the commission to “more effectively safeguard the open internet” and establish a nationwide framework. The draft would largely adopt the commission’s 2015 rules on forbearance, making clear that the record “does not convincingly show that imposing universal service contribution requirements on BIAS is necessary at this time.”
The commission in the draft defended reclassification as a national security matter, noting it has previously taken action under Title II to address national security threats against voice services. “The nation’s communications networks are critical infrastructure, and therefore too important to leave entirely to market forces that may sometimes, but not always, align with necessary national security measures,” the item said.
The draft declaratory ruling also addresses the impact of reclassification on the commission’s universal service goals under section 254 of the Communications Act. Reclassification “will put the commission on the firmest legal ground to promote the universal service goals of section 254 by enabling the commission and states to designate BIAS-only providers” as eligible telecom carriers, the draft said, adding that BIAS-only providers would be allowed to participate in the high-cost and Lifeline programs.
The draft elaborates on the importance of reclassifying broadband to the agency’s authorities under Section 214 of the Communications Act, another issue raised by industry (see 2403070040). Reclassification “enhances the Commission’s ability to protect the nation’s communications networks from entities that pose threats to national security and law enforcement.”
“We find that reclassification will significantly bolster the Commission’s ability to carry out its statutory responsibilities to safeguard national security and law enforcement,” the draft said: “There can be no question about the importance to our national security of maintaining the integrity of our critical infrastructure, including communications networks.” It noted that Congress created the FCC “for the purpose of the national defense.”
The agency dismissed arguments that reclassification isn’t justified for national security purposes: “The nation’s communications networks are critical infrastructure, and therefore too important to leave entirely to market forces that may sometimes, but not always, align with necessary national security measures.” Arguments about potential costs “are unpersuasive given that, at this point, they represent only speculation about hypothetical costs and burdens.”
A draft order on reconsideration included with Thursday’s item said the net neutrality order would resolve four outstanding petitions for reconsideration filed against the FCC’s 2020 net neutrality remand order by Incompas, California’s Santa Clara County, Public Knowledge, and jointly several public interest groups including Common Cause. “As a procedural matter, we find that we have effectively provided the relief sought by each of the Petitions through a combination of the 2023 Open Internet NPRM and today’s actions,” the draft order said. “In light of the Commission’s actions today, we grant in large part and otherwise dismiss as moot” all four petitions for reconsideration. “We agree with the petitioners that the Commission’s analysis in the [Restoring Internet Freedom] Order and RIF Remand Order was insufficient in addressing the public safety, pole attachment, and Lifeline-related repercussions of classifying BIAS as a Title I service,” the draft said.
House Commerce Committee ranking member Frank Pallone, D-N.J., and Communications Subcommittee ranking member Doris Matsui, D-Calif., praised Rosenworcel “for moving to finalize rules that reflect reality: broadband internet service is critical infrastructure and an indispensable part of American life, and it must be treated that way.” The FCC’s move for Title II reclassification shows the commission is “recognizing this reality and asserting its rightful authority over broadband providers in order to protect this vital service and the hundreds of millions who rely on it each day,” Pallone and Matsui said. The two lawmakers “have confidence that a court reviewing this action will uphold it, just as courts have done in the past.” Sens. Ed Markey, D-Mass., and Ron Wyden, D-Ore., also lauded the proposal Thursday after earlier urging Rosenworcel to prevent loopholes in the rules.
The House Commerce GOP majority was tight-lipped after the draft’s release Thursday. Republican members tweeted Wednesday that the net neutrality proposal showed the commission “continues pushing Biden’s Broadband Takeover by imposing unnecessary heavy-handed regulations.”
References:
https://docs.fcc.gov/public/attachments/DOC-401676A1.pdf
https://communicationsdaily.com/reference/2404040064?BC=bc_661167bc293cd
https://communicationsdaily.com/article/view?search_id=847526&id=1928175
BT Group, Ericsson and Qualcomm demo network slicing on 5G SA core network in UK
ABI Research: 5G Network Slicing Market Slows; T-Mobile says “it’s time to unleash Network Slicing”
Ericsson, Intel and Microsoft demo 5G network slicing on a Windows laptop in Sweden
Is 5G network slicing dead before arrival? Replaced by private 5G?
5G Network Slicing Tutorial + Ericsson releases 5G RAN slicing software
Network Slicing and 5G: Why it’s important, ITU-T SG 13 work, related IEEE ComSoc paper abstracts/overviews
Telstra achieves 340 Mbps uplink over 5G SA; Deploys dynamic network slicing from Ericsson
Australian telco Telstra announced this week that it has achieved a 5G uplink speed of 350 Mbps over 5G Standalone (SA) using sub-6 GHz frequencies in a live commercial network in partnership with Ericsson and Qualcomm. Telstra claims this as a new global record for 5G uplink speed, which is 100 times faster than the average 3G uplink speed.
Telstra’s new 5G SA uplink capability combines its mid-band spectrum holdings to create a 140MHz channel for sending data from the device to the network.
The tests were completed using a mobile test device powered by Qualcomm Technologies’ latest Snapdragon® 5G modem-RF System and an existing in-market NetGear Nighthawk M6 Pro Mobile Broadband device in the live commercial network on the Gold Coast.
The latest software from Ericsson brings together different combinations of frequency ranges and types to enable a single 5G uplink and downlink data channel.
By aggregating carrier bands, it considerably increases the uplink speeds, while the ability to use low band carriers in these combinations of frequencies delivers improved coverage and performance enhancements for the 5G SA Network.
Mr Amirthalingam says: “The uplink and downlink 5G data channels work together to provide a seamless and almost symmetrical like 5G service, meeting the increasing demand for data-intensive applications such as augmented and virtual reality, or sharing photos and memorable movie moments with friends.
“The technology also includes advanced features in the base station that can prioritise different types of data and applications and can support future differentiated services, like network slicing.”
“On top of this, Telstra also has the option to use the n5 (850MHz) carrier that is currently serving its 3G Network. “
“Our latest 5G Standalone uplink speed achievement is 100 times faster than the typical 3G uplink speed, which is great news for customers. Enterprise Applications such as these are increasingly becoming more uplink heavy with things like such as high-definition video surveillance cameras and the faster speeds and coverage will all provide a much better experience.”
“The ability to use low band frequencies and repurpose our 3G low band 850 MHz frequency to deliver 5G SA coverage when the 3G network closes on 30 June 2024, has the benefit of providing improved depth of coverage and enhancing the 5G experience for customers.”
“It’s a further example of how we are leading the way in 5G innovation and investment, and how we are committed to delivering the best and most advanced network for Australia.”
To test and validate this capability, Telstra worked with long-term partners Ericsson, the global leader in 5G network equipment, and Qualcomm, one of the world’s leading wireless chipset companies.
Emilio Romeo, Head of Ericsson Australia and New Zealand, says: “Ericsson’s latest software features enables Telstra to capitalize the full spectrum portfolio for a wider coverage whilst providing far superior data rates. Customers will be empowered to explore new experiences offered with 5G Standalone such as differentiated services and a range of applications, which will in turn drive network monetization.”
Durga Malladi, Senior Vice President and General Manager, Technology Planning & Edge Solutions Qualcomm Technologies, Inc., says: This live test proves that uplink carrier aggregation on 5G Standalone network has the potential to significantly increase upload speeds and capacity, thus unlocking new experiences for consumers.”
This latest achievement takes Telstra’s World-First count to 53 since the launch of 3G. It is only through its collaboration efforts with industry and its strategic partners, like Ericsson and Qualcomm, that it can deliver the technology innovation and leadership that its customers can benefit from.
……………………………………………………………………………………………………………………
Telstra has also implemented Ericsson’s Dynamic Network Slicing software for automated network orchestration. This software gives the operator a fully automated and monetizable network slicing orchestration capability to sell slicing services to enterprise customers.
………………………………………………………………………………………………………………
References:
Telstra’s T25 to extend 5G coverage and offer enhanced customer experiences
Telstra wins most lots in Australia’s 5G mmWave auction
BT Group, Ericsson and Qualcomm demo network slicing on 5G SA core network in UK
Years after 5G network slicing was hyped to the sky (see References below dating from 2028), BT Group, Ericsson and Qualcomm Technologies, Inc. have successfully demonstrated end-to-end consumer and enterprise 5G differentiated connectivity enabled by 5G network slicing on Ericsson’s 5G Core and Radio Access Network technology in the UK with devices powered by the Snapdragon ® 8 Gen 2 for Galaxy Mobile Platform.
The trial, which took place at Adastral Park, BT Group’s home of research and innovation, established network slices for Gaming, Enterprise and Enhanced Mobile Broadband (eMBB), and showed how, by allocating a portion of the 5G SA network to provide dynamic partitions for specific use-cases, optimal performance can be maintained for bandwidth-heavy activities including mobile gaming and video conferencing even during peak times.
Mobile gaming is experiencing relentless growth, with traffic on EE’s network almost doubling since the beginning of 2023 to more than two petabytes of data every month. With consistent low-latency, jitter-free and immersive experiences increasingly essential to the gaming experience, network slicing is expected to be a key enabler of performance and growth in the 5G SA era.
Together, BT Group, Ericsson and Qualcomm Technologies demonstrated an optimal mobile cloud gaming experience on Nvidia’s GeForce Now, maintaining a throughput comfortably in excess of the recommended 25 Mbps at 1080p even when a background load was generated. The companies initiated a gaming session on Fortnite using the Samsung S23 Ultra device, equipped with the Snapdragon 8 Gen 2 for Galaxy Mobile Platform, and Ericsson implemented Network slicing along with the Ericsson RAN feature Radio Resource Partitioning on EE’s Network to achieve a smooth experience. The experience was simultaneously compared to a non-optimised eMBB RAN partition, which was congested by the background load, resulting in a less than optimal gaming experience.
The trial also validated the potential of network slicing for BT Group’s business customers. Using the enterprise and eMBB slices, configured via URSP rules which enables a device to connect to multiple network slices simultaneously depending on the application, it demonstrated consistent 4K video streaming and enterprise use-cases using the Samsung S23 Ultra device, powered by Snapdragon 8 Gen 2 for Galaxy. Enterprise communications platforms and video applications such as YouTube require a stable connection and low jitter to work well. The Ericsson 5G RAN Slicing feature, Radio Resource Partitioning, was enabled to ensure the enterprise traffic to achieve an optimal experience.
5G network slicing requires a 5G SA core network. It supports these diverse services and reassigns resources as needed from one virtual network slice to another, making the one-size-fits-all approach to service delivery obsolete.
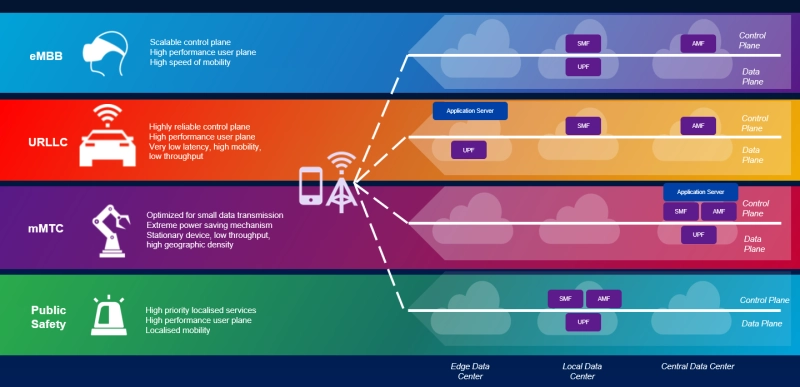
Image courtesy of Viavi
Greg McCall, Chief Networks Officer, BT Group, said: “Network slicing will enable us to deliver new and improved capabilities for customers in the 5G SA era. As we work diligently towards the launch of our own 5G SA network, today’s successful demonstration of how slicing enables us to differentiate Quality of Service to guarantee performance for different segments is a significant milestone, and illustrative of the new services that will be enabled by 5G SA.”
Enrico Salvatori, Senior Vice President and President, Qualcomm Europe/MEA of Qualcomm Europe, Inc., said: “We are proud to collaborate with BT Group and Ericsson on the network slicing trial, which used a device powered by the Snapdragon 8 Gen 2 for Galaxy mobile platform. Together, we showcased the enhanced performance and flexibility 5G Standalone capabilities, such as network slicing, will bring to consumers and enterprise experiences.”
Katherine Ainley, CEO, Ericsson UK & Ireland, said: “5G standalone and network slicing demonstrates that leading operators like EE will be able to offer customers tailored connectivity with different requirements on speed, latency and reliability for specific applications, such as video streaming and gaming. This ultimate next step in connectivity will enable new service offerings for consumers and businesses who require premium performance, while helping to drive future market growth and innovation for the UK in a wide range of new industries.”
References:
ABI Research: 5G Network Slicing Market Slows; T-Mobile says “it’s time to unleash Network Slicing”
Ericsson, Intel and Microsoft demo 5G network slicing on a Windows laptop in Sweden
Ericsson and Nokia demonstrate 5G Network Slicing on Google Pixel 6 Pro phones running Android 13 mobile OS
Samsung and KDDI complete SLA network slicing field trial on 5G SA network in Japan
Nokia and Safaricom complete Africa’s first Fixed Wireless Access (FWA) 5G network slicing trial
Is 5G network slicing dead before arrival? Replaced by private 5G?
5G Network Slicing Tutorial + Ericsson releases 5G RAN slicing software
Network Slicing and 5G: Why it’s important, ITU-T SG 13 work, related IEEE ComSoc paper abstracts/overviews
https://www.viavisolutions.com/en-us/5g-network-slicing
ABI Research: 5G Network Slicing Market Slows; T-Mobile says “it’s time to unleash Network Slicing”
5G network slicing [1.] use cases are still few and far between, mainly because so few 5G telcos have deployed the 5G SA core network which is mandatory for ALL 3GPP defined 5G features and functions, such as network slicing and 5G security.
ABI’s 5G network slicing and cloud packet core market data report found that growing ecosystem complexity and ongoing challenges with cloud-native tooling adoption have placed increased pressure on new service innovation, like 5G network slicing. ABI expects the 5G network slicing market to be worth US$19.5bn in value by 2028. Considering existing market activities, a growing force behind 5G slicing uptake is enhanced mobile broadband (eMBB) and fixed wireless access (FWA). To that end, there is growing market activity and commercial engagements from network equipment vendors (NEVs) Ericsson, Huawei, Nokia, and ZTE, among other vendors. ABI regards these market engagements as representing a good foundation for the industry to match 5G slicing technology to high-value use cases, such as enhanced machine-type communication and ultra-reliable low-latency communications.
Note 1. A network slice provides specified network capabilities and characteristics – or multiple, isolated virtual networks – to fit a user’s needs. Although multiple network slices run on a single physical network, network slice users are sometimes (depending upon the access level of the individual) authenticated for only one network level, enabling data and security isolation and a much higher degree of security. Individuals can be sanctioned for more than network level. Each slice spans multiple connected components that form a network, components that include physical computing, storage and networking infrastructure. These are virtualized, and protocols are set in place to create a specific network slice for each user or application. This means that varying types of 5G traffic, such as video streaming, industrial automation and mission-critical applications, all can be accommodated on the same network, yet each has its own dedicated resources and performance guarantees.
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
“5G Slicing continues to promise new value creation in the industry. However, as reflected in multiple ABI Research’s market intelligence reports, a solid software and cloud-native foundation must be in place for that promise to materialize. That, in turn, is a prerequisite for a wider diffusion of 5G core adoption, an architecture that provides native support for 5G slicing,” explains Don Alusha, Senior Analyst at ABI Research.

Image Credit: Viavi Solutions
From a network architecture perspective, ABI said two modalities are emerging to deploy 5G slicing. The first one is to share the whole infrastructure spanning radio access network (RAN), core, physical devices and physical servers. This, said the analyst, constitutes a unified resource pool, the basis of which can be used to instantiate multiple logical connectivity transmissions.
A second approach is to provide hardware-based logical slices by slicing the physical equipment. The analyst cautions that this is a time-consuming, resource-intensive endeavor, but said it may be the best option for mission-critical services. It requires slicing the physical transmission network and oftentimes a dedicated user plane.
“Horizontal integration for cross-domain interoperability is critical going forward. Equally important is vertical integration for 5G slicing lifecycle management of multi-vendor deployments. There is ongoing market activity for the 5G core network penetration and maturity of 5G slice management functions. To that end, enterprises will seek to create and reserve slices statically and on-demand. They also want to efficiently integrate with cloud providers through open and programmable Application Program Interfaces (APIs) to enable hybrid cloud/cellular slice adoption. NEVs and other suppliers (e.g., Amdocs, Netcracker, etc.) offer solutions enabling CSPs to create fully automated and programmatic slicing capability over access, transport, and core network domains,” Alusha concludes.
These findings are from ABI Research’s 5G Network Slicing and Cloud Packet Core market data report. This report is part of the company’s 5G Core & Edge Networks research service, which includes research, data, and analyst insights. Market Data spreadsheets comprise deep data, market share analysis, and highly segmented, service-specific forecasts to provide detailed insight into where opportunities lie.
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………
T-Mobile US, the only U.S. carrier that has deployed 5G SA core network, has recently shared details of what it claims is “first use of 5G network slicing for remote video production on a commercial network,” which took place during Red Bull’s cliff diving event in Boston, MA. This customized slice gave the broadcast team supercharged wireless uplink speeds so they could easily and quickly transfer high-resolution content from cameras and a video drone circling the event to the Red Bull production team in near real-time over T-Mobile 5G. The uplink speed was up to 276 Mbps!
T-Mobile says they can also use network slicing for specific application types for enterprise customers across the U.S. Earlier this month they launched a first-of-its-kind network slicing beta for developers who are working to supercharge their video calling applications with the power of 5G SA. With a customized network slice, developers can sign up to test video calling applications that require consistent uplink and downlink speeds along with increased reliability. In the weeks since, we’ve seen tremendous interest from the developer community with dozens of companies large and small signing up to join the likes of Dialpad, Google, Webex by Cisco, Zoom and more.
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………
Vodafone recently worked with Ericsson to provision network slices optimized for cloud gaming. In January, Samsung and KDDI announced the successful demonstration of Service Level Agreements (SLA) assurance network slicing in a field trial conducted in Tokyo, Japan. Yet there’s hardly a flood of real-world use cases (see References below).
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………
References:
https://www.abiresearch.com/market-research/product/market-data/MD-SLIC/
https://www.computerweekly.com/news/366550353/5G-network-slicing-value-hits-19bn-but-growth-stalls
https://www.t-mobile.com/news/network/its-time-to-unleash-network-slicing
https://www.viavisolutions.com/en-us/5g-network-slicing
Network Slicing and 5G: Why it’s important, ITU-T SG 13 work, related IEEE ComSoc paper abstracts/overviews
Samsung and KDDI complete SLA network slicing field trial on 5G SA network in Japan
Ericsson, Intel and Microsoft demo 5G network slicing on a Windows laptop in Sweden
Ericsson and Nokia demonstrate 5G Network Slicing on Google Pixel 6 Pro phones running Android 13 mobile OS
Nokia and Safaricom complete Africa’s first Fixed Wireless Access (FWA) 5G network slicing trial
Is 5G network slicing dead before arrival? Replaced by private 5G?
5G Network Slicing Tutorial + Ericsson releases 5G RAN slicing software
GSA 5G SA Core Network Update Report
ABI Research: Expansion of 5G SA Core Networks key to 5G subscription growth
The number of 5G subscriptions will surge from 934 million in 2022 to 3.1 billion in 2027 -a Compound Annual Growth Rate (CAGR) of 27% – according to a study from ABI Research. Further, 5G traffic is forecast to increase from 293 Exabytes (EB) in 2022 to 2,515 EB in 2027, at a CAGR of 54%.
ABI’s forecast is largely based on an increase in 5G Core (5GC) networks. To date, more than 35 5GC networks are operating in 5G standalone (SA) mode. 5GC is expected to lead to a growth in devices connected to the network and the traffic routed through it.
“5GC holds potential for operators to monetize further existing cellular connectivity for traditional mobile broadband (MBB) use cases but also offers scope for operators to expand cellular capabilities in new domains. Additionally, 5GC also offers innovation potential for committed telcos to establish new operating models for growth outside of the consumer domain,” explains Don Alusha, Senior Analyst, 5G Core and Edge Networks, at ABI Research.
5GC presents Communications Service Providers (CSPs) with a fluid and dynamic landscape. In this landscape, there is no static offering (requirements constantly change), no uniform offering (one shoe does not fit all), and no singular endpoint (one terminal with multiple applications). 5GC guides the industry into edge deployments and topologies. CSPs step out of the four walls of either their virtual Data Center (DC) or physical DC to place network functionality and compute as close to their customers as possible. This constitutes decentralization, a horizontal spread of network assets and technology estate that calls for a ‘spread’ in the operating model.
The shift from a centralized business (e.g. with 4G EPC) to a decentralized business (5G SA core network) stands to be a significant trend in the coming years for the telecoms industry. Against that backdrop, the market will demand that CSPs learn to drive value bottom-up. “What customers need” is the starting point for companies like AT&T, BT, Deutsche Telekom, Orange, and Vodafone. In other words, in this emerging landscape, there will be enterprise-specific, value-based, and niche engagements where the business strategy sets the technology agenda. So, it is rational to conclude that a “bottom-up” approach may be required to deliver unique value and expand business scope. That said, CSPs may be better equipped to drive sustained value creation if they learn to build their value proposition, starting from enterprise and industrial edge and extending to core networks.
“A 5G cloud packet core can potentially unlock new transactions that supplement existing volume-centered modus operandi with a local, bottom-up value play for discrete engagements. But the power of a bottom-up model is not enough. To monetize a 5G cloud packet core at scale, some of the existing top-down intelligence is needed too. Learning how to operate in this hybrid top-down and the emerging bottom-up, horizontally stratified ecosystem is a journey for NTT Docomo, Rakuten Mobile, Singtel, Softbank, and Telstra, among other CSPs. In the impending cellular market, an effective and efficient operating model must contain both control and lack of control, both centralization and decentralization and a hybrid of bottom-up plus some of the ‘standard’ top-down intelligence. The idea is that CSPs’ operating model should flexibly fit and change in line with new growing market requirements, or new growth forays may hit a roadblock,” Alusha concludes.
Editor’s Note:
It’s critically important to understand that the 3GPP defined 5G core network protocols and network interfaces enable the entire mobile system. Those include call and session control, mobility management, service provisioning, etc. Moreover, the 3GPP defined 5G features can ONLY be realized with a 5G SA core network. Those include: Network Automation, Network Function Virtualization, 5G Security, Network Slicing, Edge Computing (MEC), Policy Control, Network Data Analytics, etc
Figure 1: Overview of the 5G system
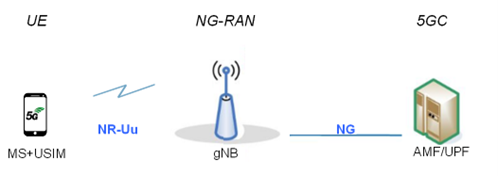
The 5GC architecture relies on a “Service-Based Architecture” (SBA) framework, where the architecture elements are defined in terms of “Network Functions” (NFs) rather than by “traditional” Network Entities. Via interfaces of a common framework, any given NF offers its services to all the other authorized NFs and/or to any “consumers” that are permitted to make use of these provided services. Such an SBA approach offers modularity and reusability.
Figure 2: 5G SA Core Network Architecture
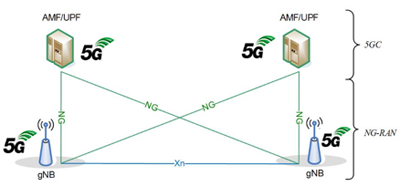
The 5G SA architecture can be seen as the “full 5G deployment,” not needing any part of a 4G network to operate.
Finally, 3GPP has not liased their 5G system architecture specifications to ITU-T so there are no ITU-T standards for 5G SA Core Network or any other 5G non-radio specification. Instead, 3GPP sends their specs to ETSI which rubber stamps them as “ETSI standards.”
……………………………………………………………………………………………………………………………………………………….
These findings are from ABI Research’s 5G Core Market Status and Migration Analysis report. This report is part of the company’s 5G Core & Edge Networks research service, which includes research, data, and analyst insights. Based on extensive primary interviews, Application Analysis reports present an in-depth analysis of key market trends and factors for a specific technology.
About ABI Research
ABI Research is a global technology intelligence firm delivering actionable research and strategic guidance to technology leaders, innovators, and decision makers around the world. Our research focuses on the transformative technologies that are dramatically reshaping industries, economies, and workforces today.
References:
https://www.3gpp.org/technologies/5g-system-overview#
https://www.nokia.com/networks/core/5g-core/
A few key 3GPP Technical Specifications (TSs) are listed here:
- TS 22.261, “Service requirements for the 5G system”.
- TS 23.501, “System architecture for the 5G System (5GS)”
- TS 23.502 “Procedures for the 5G System (5GS)
- TS 32.240 “Charging management; Charging architecture and principles”.
- TS 24.501 “Non-Access-Stratum (NAS) protocol for 5G System (5GS); Stage 3”
- TS 38.300 “NR; NR and NG-RAN Overall description; Stage-2”
Big 5 Event: wireless connectivity use cases for healthcare, network slicing, security and private networks
Emerging use cases for wireless telecommunications technology was discussed at the Big 5G event in Austin, TX last week in a panel session titled, “Future connectivity use cases and the Holy Grail: Private networks, metaverse, 6G and beyond.” The questions addressed included:
- Who is monetizing private networks and what are we learning from their experiences?
- Should telcos move past targeting only large enterprise customers for 5G services?
- When will the metaverse take off?
- How are telcos gearing up for 6G and what are the expectations?
Jodi Baxter, vice president for 5G and IoT connectivity at Telus, described the numerous emerging applications of 5G in healthcare. One example is a connected ambulance project carried out with Alberta Health Services, where, thanks to 5G, doctors can remotely issue authorizations necessary for stroke medication, which needs to be administered within a narrow time window.
Some of the applications developed for the healthcare sector can also be included in telcos’ offerings to corporate customers. Baxter said Telus has included remote doctor and nurse consultations in 5G bundles for small businesses, which can help their staff retention rates. Healthcare companies are also looking at more specific applications, with Baxter citing the example of a healthcare company that would wish to track hip and knee replacements with 5G.
While sustainability is often seen as an unprofitable endeavor, Baxter argued technology can help customers see a return on investment. One of Telus’s projects in this area uses drones and 5G for reforestation.
…………………………………………………………………………………………………………………………………..
Omdia’s research has shown that about a fifth of midsized to large enterprises “want to invest in 5G network slicing in the next two years, but most people cannot find a commercial offer,” said Camille Mendler, chief analyst of enterprise services at Omdia. “[It’s] not there yet, which is a problem, right?” she added. Note that 5G network slicing requires a 5G SA core network, which most 5G service providers have yet to deploy.
Baxter noted that network slicing will be a game changer for security and transportation of critical data. The panel pointed to autonomous vehicles as another potential application that will require its own slice. She also said slicing will be important for ensuring applications from private 5G networks also have a macro capability.
Lori Thomas, senior vice president for strategic engagement and transformation at MetTel, pointed out that a lot of government agencies are currently looking to bring specific functionalities from the private network onto the public network, and make them accessible in edge devices such as laptops and tablets.
…………………………………………………………………………………………………………………………………..
William Britton, vice president for information technology and CIO at California Polytechnic State University, said it is not always easy to figure out how products offered by telecom companies apply to specific use cases. The university has been told to “go elsewhere” by providers when it has approached them about possible 5G applications, as the solutions on offer did not meet requirements, he said.
Speaking about the particular needs of his university, he highlighted the significant demand for bandwidth during limited events, such as course registration, as well as ad hoc scenarios like high data throughput during online gaming events.
A big concern for universities in general is cybersecurity. Britton points out that the education sector has become a massive target for cyberattacks, such as malware and ransomware. Indeed, research suggests that attacks on educational organizations grew by 44% in 2022, while data from endpoint protection firm Emsisoft suggests that the number of individual schools impacted by ransomware attacks also grew.
Security is a major priority for organizations everywhere, not just in the education sector. Thomas points to IoT, where vast amounts of data travel at high speeds, which is particularly attractive for bad actors. Once 5G can be coupled with blockchain, she noted, data security will improve.
One way to look at specific use cases is through innovation labs, with Thomas saying in the short term these can accelerate the time to revenue. She pointed to MetTel’s partnership with SpaceX and VMware, which saw the latter company’s software-defined wide area network deployed over Starlink to bring high-bandwidth communications to remote areas.
Thomas also said demand for more bandwidth was one of the key trends in the public sector. Customers are, according to her, looking at technologies including 5G fixed wireless access (FWA) and satellites to secure it.
A lot of innovation has focused on private networks, but the “real money” lies outside of them, said Mendler. No further details were provided.

Omdia’s Camille Mendler says companies cannot find commercial network slicing.
Source: JLeitner Photography
……………………………………………………………………………………………………………………………….
References: